Archive
Demonstrating that anti-virus doesn’t just depend on up-to-date signatures
The granddaddy of security software is the venerable anti-virus. But the mother of all attacks is the zero-day targeted exploit. Vendors of new products specifically designed to protect against the latter continuously insinuate that anti-virus no longer works — ergo you need to buy their shiny new product to stay safe.
These vendors point out that the attacker merely needs to modify the malware to change its signature to instantly create a pseudo-0-day that defeats AV signature engines. And to prove their point, they will submit the pseudo or actual 0-day to VirusTotal to demonstrate that few if any AV products actually detect it.
This gives a false impression. VT basically just submits the sample to the signature engine — which won’t detect 0-days. But the AV industry long ago accepted that signatures alone are not enough, and built additional behavioural defences into their products. These are not generally tested by VT.
So when a VirusTotal report says a particular sample was not detected by your own AV software, that doesn’t necessarily mean that it would not be detected by the AV product’s behavioural methods in situ on your PC. It’s a difficult thing to prove, and it has left the anti-virus industry disadvantaged against the arguments of the newer products.
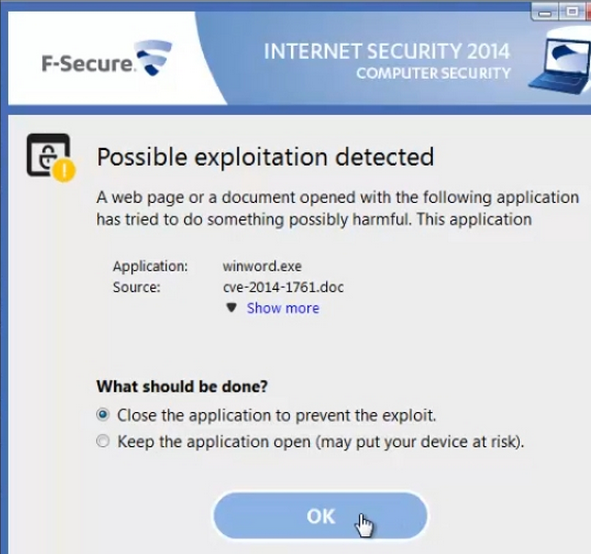
Now F-Secure has tested it. There is a new 0-day MS Word/RTF vulnerability that is expected to be fixed by Microsoft in this week’s Patch Tuesday patches. For the moment, it remains a 0-day.
“Now that we got our hands on a sample of the latest Word zero-day exploit (CVE-2014-1761),” reported Timo Hirvonen, senior researcher at F-Secure, yesterday, “we can finally address a frequently asked question: does F-Secure protect against this threat? To find out the answer, I opened the exploit on a system protected with F-Secure Internet Security 2014, and here is the result:


I would suggest that F-Secure is not the only AV software able to detect the worrying behaviour, if not the signature, of the 0-day without ever seeing the malware.
The reality is that no software can guarantee to stop all malware; but anti-virus software remains the bedrock of good security. Adding to it is prudent; replacing it is foolhardy.
It’s time for McAfee and Symantec to state clearly that they do not collaborate with governments
When I wrote the piece, Is the AV industry in bed with the NSA, I concluded that on balance it probably is. I have no evidence. It’s just that I cannot believe that an organization complicit in developing and deploying its own malware, and able to ‘socially engineer’ RSA into doing its bidding, would leave AV untouched.
Obviously I spoke to people in the industry. In private conversation with one contact, while accepting his own protestations of innocence, I asked, “What about McAfee and Symantec?” He paused; but then said, “If I had to question anyone, those are the two names that would come to mind.”
I should say, again, that I have no evidence. It’s just doubts born out of the repetition of hyped-up statistics, frequently used by government to justify its actions, and what appears to be preferential treatment from government.
A couple of months later, the Dutch digital liberty group Bits of Freedom wrote to the leading AV companies for a formal position. One of the questions it asked was, “Have you ever been approached with a request by a government, requesting that the presence of specific software is not detected, or if detected, not notified to the user of your software?”
My understanding is that some, but not all, AV companies replied, in writing, that they do not collaborate with governments.
F-Secure’s Mikko Hyppönen spoke yesterday at the TrustyCon conference. I wasn’t there, so this is from The Register’s report:
A surprising number of governments are now deploying their own custom malware – and the end result could be chaos for the rest of us, F-Secure’s malware chief Mikko Hyppönen told the TrustyCon conference in San Francisco on Thursday…
While ESET, F-Secure, Norman Shark, Kaspersky, Panda and Trend Micro replied to Bits of Information, Symantec and McAfee (among others) have not responded, Hyppönen claimed.
Same names. Coincidence? I wonder.
Bits of Freedom seeks clarity from the AV industry on collusion with law enforcement
On 25 September I posed the question: Is the anti-virus industry in bed with the NSA? Now Bits of Freedom, a Dutch digital rights group, has asked the same question in a letter signed by more than 25 civil rights groups and individuals (including Bruce Schneier, EDRi and EFF).
On 25 October it wrote to more than a dozen of the world’s leading anti-virus companies asking four specific questions:
1. Have you ever detected the use of software by any government (or state actor) for the purpose of surveillance?
2. Have you ever been approached with a request by a government, requesting that the presence of specific software is not detected, or if detected, not notified to the user of your software? And if so, could you provide information on the legal basis of this request, the specific kind of software you were supposed to allow and the period of time which you were supposed to allow this use?
3. Have you ever granted such a request? If so, could you provide the same information as in the point mentioned above and the considerations which led to the decision to comply with the request from the government?
4. Could you clarify how you would respond to such a request in the future?
With the greatest respect, this is a pointless exercise; the companies will deny any collusion with law enforcement to subvert their products whether they have or not. And they may have, or they may not.
I have no idea whether there is collusion between AV and law enforcement. Every single member of the AV industry I have spoken to denies it absolutely – and I believe them. There really are some great, learned, honest and honourable guys in the AV industry. But the NSA says it doesn’t break the law; and I absolutely do not believe them.
We know that the NSA hacks into third-party computers and installs malware. We know that it is the AV industry’s job to detect and neutralise such malware. We therefore know that the NSA will not want the AV industry to do that to their own malware.
It would be easy enough to defeat AV engines to get onto a computer; but it is less easy to stay hidden for any length of time after that. But we know that state-sponsored malware remains undetected for years. How does it do that? The easiest way would be to subvert the seek and destroy software that hunts it.
So, given the amount of time and resources that the NSA has spent on subverting what gets in its way – such as encryption – is it reasonable to believe that it hasn’t spent similar effort on neutralizing the AV industry?
I don’t know the answer; and it doesn’t matter who in the AV industry tells me, nor in what regard I hold them, nor how many times they tell me, I still will not know.
And that, perhaps, is the very worst thing that the NSA has done. It has destroyed trust in the internet, and has destroyed trust in anything to do with the internet. For that the NSA cannot – and must not – ever be forgiven.
Is the anti-virus industry in bed with the NSA – why do CIPAV, FinFisher and DaVinci still defeat AV?
September 2013 is the month in which the extent of direct government hacking – as opposed to traffic surveillance – became known.
4 September – WikiLeaks releases Spy Files 3, demonstrating increasing use of third-party hacking tools, such as FinFisher.
6 September – Bruce Schneier writes in the Guardian
The NSA also devotes considerable resources to attacking endpoint computers. This kind of thing is done by its TAO – Tailored Access Operations – group. TAO has a menu of exploits it can serve up against your computer – whether you’re running Windows, Mac OS, Linux, iOS, or something else – and a variety of tricks to get them on to your computer. Your anti-virus software won’t detect them, and you’d have trouble finding them even if you knew where to look. These are hacker tools designed by hackers with an essentially unlimited budget. What I took away from reading the Snowden documents was that if the NSA wants in to your computer, it’s in. Period.
7 September – details of an NSA MITM operation against Google users in Brazil revealed.
12 September – FBI admits that it hacked Freedom Hosting. The implications are that it inserted the malware that monitored visitors, and the almost certainty that the malware was CIPAV.
FinFisher and CIPAV stand out as government operated spyware; but there are others: RCS (DaVinci), Bundestrojaner etcetera – and, of course, Stuxnet and Flame. We’ve known about them for a long time: see
- CIPAV: FBI, CIPAV spyware, and the anti-virus companies (this site, May 2011)
- RCS: Hacking Team’s RCS: hype or horror; fear or FUD? (this site, Nov 2011)
- FinFisher: Use of FinFisher spy kit in Bahrain exposed (Infosecurity Mag, August 2012)
- Bundestrojaner: Chaos Computer Club warns on “German government” communications trojan (Infosecurity Mag, Oct 2011)
This leaves a major question begging: if we’ve known about this malware for such a long time, how come it can still be used? Why doesn’t anti-malware software stop it?
There are two possible reasons that we’ll explore:
- the AV industry, like so many others, is in bed with the NSA
- the AV industry is not as good as the ‘stops 100% of known malware’ claims that it makes – or put another way, virus writers are generally one-step ahead of the AV industry
In bed with the NSA
This has been vehemently denied by every AV company I have spoken to (see the articles on CIPAV and RCS for examples). Bruce Schneier doesn’t believe it is:
I actually believe that AV is less likely to be compromised, because there are different companies in mutually antagonistic countries competing with each other in the marketplace. While the U.S. might be able to convince Symantec to ignore its secret malware, they wouldn’t be able to convince the Russian company Kaspersky to do the same. And likewise, Kaspersky might be convinced to ignore Russian malware but Symantec would not. These differences are likely to show up in product comparisons, which gives both companies an incentive to be honest. But I don’t know.
Explaining the latest NSA revelations – Q&A with internet privacy experts
And yet the possibility lingers. When Flame was ‘discovered’, Mikko Hypponen issued a mea culpa for the industry. Admitting that F-Secure had Flame samples on record for two years, he said,
Researchers at other antivirus firms have found evidence that they received samples of the malware even earlier than this, indicating that the malware was older than 2010.
What this means is that all of us had missed detecting this malware for two years, or more. That’s a spectacular failure for our company, and for the antivirus industry in general.
It wasn’t the first time this has happened, either. Stuxnet went undetected for more than a year after it was unleashed in the wild…
Why Antivirus Companies Like Mine Failed to Catch Flame and Stuxnet
Forget the ‘hand on heart’ for a moment, and consider… That’s the two major government-sponsored malware samples known about and ignored by multiple AV companies for several years. Coincidence? Maybe. But to echo Schneier’s last sentence, I don’t know.
Malware writers are one step ahead of the AV industry
If you listen to the AV marketers, this cannot be true. Every month we hear claims that AV products stop 99.9% to 100% of all known viruses (remember that they ‘knew’ about Stuxnet and Flame, but did nothing). I’ve written on my dismay at this sort of advertising elsewhere (for example, Anti Malware Testing Standards Organization: a dissenting view).
However, if you listen to the foot soldier researchers – and sometimes even higher –within the individual companies, you realise that it is absolutely, inherently, and unavoidably true. Luis Corrons, the technical director at PandaLabs, puts it like this:
The effectiveness of any malware sample is directly proportional at the resources spent. When we talk about targeted attacks (and [CIPAV and FinFisher] are developed to perform targeted attacks) the most important part is the ability to be undetected. Bypassing signature detection is trivial, although it is almost useless too, as most anti-malware programs have several different layers of protection which do not rely on signatures.
The attackers probably know which security solution(s) the potential victim is using. Then it is as ‘simple’ as replicating the same scenario (operating system, security solution, etc.) and verifying that the malware is not being detected. As soon as it is flagged they will change it to avoid detection, until they have the final version.
Once they are done, they will infect the victim and will be spying / stealing information out of him until they are detected. This could be a matter of days, months or even years.
Claudio Guarnieri of Rapid7 said very similar:
Since FinFisher, just as any other commercial spyware, is a very targeted and sophisticated (besides expensive) malware, it’s part of Gamma’s development lifecycle to make sure that they tweaked all the different components to avoid antiviruses before shipping the new FinFisher out to the customers.
The developers likely have their own internal systems to do these testings: think of something as a private VirusTotal. Every time they develop a new feature or a new release, they’ll test it against as many antiviruses as possible and if something gets detected, they debug and try to understand why and find a way around it.
The ‘problem’ with this approach is that they rely on the AV industry not knowing and not having access to their malware: whenever that happens AV vendors react pretty effectively and in fact if you look at FinFisher samples discovered 1 year ago they are now largely detected by most antivirus products.
Conclusion
Is the AV industry in bed with the NSA? The simple fact is that we just do not know. The industry itself denies it – but, well, it would, wouldn’t it? Statistically, since almost every other aspect of the security industry collaborates with or has been subverted by the NSA, my suspicion is that it is. At the very least, I suspect it engages in ‘tacit connivance’.
Are malware developers one step ahead of the AV industry? That depends. As Corrons says, it depends on the resources available to the bad guys, whether that’s NSA, FBI, GCHQ or the Russian Business Network. Well-resourced bad guys will always get in. As Schneier puts it, “if the NSA wants in to your computer, it’s in. Period.” But that probably applies to all governments and all seriously organized criminal gangs engaged in targeted hacking.
But one final comment: nothing said here should be taken to suggest that we don’t need the AV industry. It may not be able to stop the NSA, but it can and does stop a million script kiddie wannabe hackers every day.
see also:
Bits of Freedom seeks clarity from the AV industry on collusion with law enforcement
It’s time for McAfee and Symantec to state clearly that they do not collaborate with governments
Old Mac Bloggit isn’t really a grumpy old man…
…he’s really a rather nice young chap. But he’s certainly feeling a bit peeved right now, and with some reason. He’s upset about the unquestioning articles in the New York Times (31 December) and the Register (1 Jan) discussing a new report by Imperva. Actually, I discussed it in Infosecurity Magazine on 28 November.
Imperva concluded that anti-virus products are not that good (“The antivirus industry has a dirty little secret: its products are often not very good at stopping viruses,” says the NYT). Imperva’s proof is that VirusTotal (an online collection of AV engines) failed to block many of the 0-day viruses it threw at it. What I said in Infosecurity was that “the real value of VirusTotal is in allowing users to check whether a suspect file is actually malware – it was designed to check malware, not to check AV products.”
Mac Bloggit doesn’t have to acknowledge the niceties of journalism, and can be more succinct. “Perhaps the NYT would care to look up the terms heuristic analysis, behaviour blocking, sandboxing, behaviour analysis, whitelisting, integrity checking, traffic analysis, and emulation, among other approaches that a security program might use to detect possible malicious activity.” His point, and he has a point, is that VirusTotal does not and cannot measure the efficiency of these parts of AV products. The fact that Stoppem Anti Virus on VirusTotal doesn’t detect the latest virus doesn’t mean that Stoppem Anti Virus on a PC won’t detect and/or block the very same latest virus.
Using VirusTotal to judge an anti-virus product isn’t merely bad form, it is positively dangerous – it might tempt users into abandoning AV altogether. That would be a very, very bad idea. The Imperva report is actually a sleight of hand by a non AV vendor. But here’s the rub: the AV industry isn’t innocent of its own sleights of hand.
The one that gets me personally rather hot under the collar is the ‘destroys all known bacteria dead’. Well, that’s the clear message. The actual terminology is ‘stops 100% of viruses in the Wild’. What it is really saying is that Stoppem Anti Virus detects every virus in the Wild List. And the Wild List is very different to ‘in the wild’. In fact, the Wild List is effectively compiled by the AV industry; so in reality, any AV company that doesn’t score at least 99.99% success against viruses in the Wild is largely incompetent.
So I would say this. Imperva, you have been a bit naughty in your report. AV industry, you can be a bit naughty yourself. So stoppit, both of you. Anti-virus is good, not perfect, but essential. Just tell us the truth.
Update
David Harley includes quite a lengthy comment on this blog in his post, Going beyond Imperva and VirusTotal. In particular he delves into the pros and cons of WildList testing. He doesn’t completely disagree with me; but nor does he completely agree – so it’s well worth a read.
My news stories on Infosecurity Magazine this week (so far)
News stories for 30 April – 2 May 2012:
Megaupload prosecution is lawless, says Professor of Law
Eric Goldman, Associate Professor of Law at Santa Clara University School of Law, says the prosecution of Megaupload is “a depressing display of abuse of government authority.”
02 May 2012
Al-Qaeda uses steganography – documents hidden in porn videos found on memory stick
Steganography is the science of hiding data. Its most common digital use is to hide data within graphics – text hidden in a picture. Al-Qaeda apparently hid documents within porn videos on a memory stick.
02 May 2012
VPNs used to defeat censorship and data retention in Sweden
Pirates, typified by The Pirate Bay, are under increasing attack from the authorities around the world. Sweden is more than the spiritual home of The Pirate Bay – so it is not surprising that user-reaction to these attacks is being led by Swedes with an increasing use of VPNs.
02 May 2012
New combined home firewall & anti-virus is free
Home computer users do not, in general, pay for security. They rely instead on free software offered with little or no support. This can cause problems when different free products conflict with each other.
01 May 2012
Trusteer finds new ransomware variant
Ransomware is malware that locks up computers and demands payment for their release. A common ruse is to pretend that the malware is actually a ‘seizure’ by law enforcement agencies.
01 May 2012
UK ISPs must block The Pirate Bay – By Order
It was expected in June, but it happened on the last day of April: UK ISPs must block access to The Pirate Bay (TBP) by order of the court.
01 May 2012
Let’s do the ACTA Time Warp again
It appeared that ACTA was dead in the European Parliament when the ACTA rapporteur David Martin advised that it should be rejected. But now Marielle Gallo has postponed the recommendation of the Legal Affairs committee.
30 April 2012
42 blackmail sites -posing as news sites – shut down in China
Genuine news sites publish information on events – these sites, say the Chinese authorities, promised not to publish information for a fee.
30 April 2012
How to break into security (as a professional)
These are questions that students and unfulfilled geeks continually ask; and ones that all security practitioners receive more than any other. DigiNinja has tried to find an objective response.
30 April 2012
Keynote sessions from Infosecurity Europe 2012 – and a few other stories
Infosecurity Europe is over for another year. If you weren’t there, well I just suggest you make sure you get there next year. Meantime, here’s my take on a couple of the announcements and almost all of the keynote sessions:
Infosecurity Europe 2012: Minister of State for Universities and Science introduces the 2012 security breaches survey
The challenge, says the Rt Hon David Willetts, is that in order to get the economic and social benefits that the internet offers, we need to first tackle cyber security.
24 April 2012
PwC and Infosecurity Europe release the latest Information Security Breaches Survey
Significant attacks more than double, but one-in five companies still spend less than one percent of their IT budget on security, and more than half of small organizations do no security training at all.
24 April 2012
Russian cybercrime: what Russia is doing, and what it should be doing
Russian security company Group-IB says Russian cybercriminals made £2.3b in 2011; Russian-speaking cybercriminals made more than $4b; and worldwide, cybercriminals made more than $12.5b.
24 April 2012
Trustworthy Internet Movement Launches Pulse Tracker
The problem, says Pulse, is that we are telling users that this site has SSL, so it’s secure. That’s not necessarily true. We are promulgating a false sense of security, and we need to fix that.
25 April 2012
Infosecurity Europe 2012: defining risk management in the context of information security
The three companies represented on the keynote panel (G4S Secure Solutions, Steria UK, and Skipton Building Society) are very different; and their CISOs have very different views on the functioning of risk management within infosec.
25 April 2012
Infosecurity Europe 2012: the rising role of the CISO
Chaired by Quocirca’s Bob Tarzey, Network Rail’s CISO Peter Gibbons and Yell’s CISO Phil Cracknell led a lively discussion on the current and future role of the CISO.
25 April 2012
Ipswitch survey reveals the extent to which IT is losing control over data
IT needs governance; but users are choosing simplicity. In choosing and using their own non-sanctioned methods for data transfer, users are causing IT to lose control over its own data.
25 April 2012
Infosecurity Europe 2012: AET & APT – Is this the next-generation attack?
Advanced persistent threats (APT) and advanced evasive techniques (AET): what are they, who’s doing them, and what can we do about them?
26 April 2012
Has the time come to dump anti-virus?
Bit-9 asks the question that dare not be spoken: is anti-virus beyond its sell-by date? And is BYOD the final straw?
26 April 2012
Infosecurity Europe 2012: The ICO on better regulation and better infosec
Christopher Graham, the UK Information Commissioner, talks about his role as an information regulator and facilitator at Infosecurity Europe in London
26 April 2012
Infosecurity Europe 2012: Are we smart enough to secure smartphones?
Three heads of security from three very different organizations came together to discuss their practical and very different experiences in introducing a company BYOD strategy.
26 April 2012
Infosecurity Europe 2012: The insider threat – is it real?
While the primary security stance faces outwards and is designed to keep hackers and malware outside of the system, organizations are increasingly aware that their own staff are also a potential – and in some cases an active – threat.
27 April 2012
Infosecurity Europe 2012: The cloud – do you really know what you’re getting in to?
The cloud is new; but it’s been around for years. It’s insecure; but more secure than we fear. Two practitioners discussed the cloud of FUD.
27 April 2012
It’s the lack of understanding of virtualization that makes security an issue
A new study from Kaspersky Lab confirms an earlier one from Crossbeam Systems: it’s a lack of knowledge about virtualization that leads to fear for its security.
26 April 2012
Infosecurity Magazine news stories for 5-7 March 2012
My news stories on Infosecurity Magazine for Monday, Tuesday and Wednesday this week…
Trustwave to acquire M86 Security
Trustwave, a Chicago-based security company with offices around the world, has signed a definitive agreement to acquire M86 Security, which is based in Irvine California and has international headquarters in London and R&D in California, Israel and New Zealand.
07 March 2012
CIOs recognize the mobile threat; but aren’t yet responding to it
A new survey from Vanson Bourne, sponsored by Sophos, underlines a current anomaly: CIOs believe that mobile devices are a security risk, but aren’t doing much about it.
07 March 2012
LulzSec leader Sabu turns FBI informant
It’s been a tempestuous week in the battle between Anonymous and the law: 25 arrests, the poisoning of the Anonymous DDoS tool, and now the LulzSec leader, Sabu, has been named an FBI informant.
07 March 2012
Trust in communications is decreasing
While the UK is becoming increasingly better connected, trust in those connections is declining.
06 March 2012
THOR: a new P2P botnet for sale
A new botnet is nearing completion and is being offered for sale on the hacking underground at $8000.
06 March 2012
India/Bangladesh cyberwar moves to a new level
The ongoing cyberwar between India and Bangladesh has escalated with Teamgreyhat, in support of “our Indian brothers”, moving from commercial to economic targets.
06 March 2012
Is it time to move on from anti-virus?
On Friday, Wired quoted security expert Jeremiah Grossman as someone who doesn’t use anti-virus software, and asked the question: “Is Antivirus Software a Waste of Money?”
05 March 2012
UK opts in to the EU-USA PNR agreement
The UK’s Home Office says that on the 9th February 2012 it notified the President of the Council that “the government has opted in to the EU-US Agreement on the exchange of passenger name record [PNR] data.”
05 March 2012
Twitter complies with court order – hands over account details
Guido Fawkes in the UK is the pseudonym of an award-winning anti-establishment blog operated by Paul Staines. In the US it is a name associated with a Twitter account handed over to law enforcement. Around the world is has become associated with the Anonymous movement.
05 March 2012
Anonymous (AntiSec) says we’re still here; takes down PandaLabs
It’s always sad, and more than a little embarrassing, when a security site gets owned. But that’s what happened to PandaLabs yesterday evening. AntiSec hit back in retaliation, it said, for PandaLabs’ involvement in the arrest of 25 Anonymous members reported on 28 February. The timing, and indeed the opening statement on AntiSec’s defacement, suggests that it had just as much to do with the FBI yesterday charging six LulzSec hackers, including Sabu (so-called leader of LulzSec) over the Stratfor hack. Sabu had been arrested last summer, but it was never officially announced. Yesterday it became clear that he ‘pled guilty’ at the time – which pretty much confirms that he has been acting as an informant for the FBI ever since.
Reports suggested that he turned President’s Evidence to minimize any prison term away from his family – and any parent will recognize the pressure. AntiSec’s opening statement on the PandaLabs’ defacement accuses PandaLabs of ‘traison’ – “something we don’t forgive”. But then it immediately goes on to say, “Yeah, yeah, we know… Sabu snitched on us. As usually happens FBI menaced him to take his sons away. We understand, but we were your family too (remember what you liked to say?).”
So in one sense PandaLabs was chosen to make a statement to the world: “We’re still here – expect us.”
However, AntiSec specifically accuses PandaLabs of helping “to jail 25 anonymous in different countries and they were actively participating in our IRC channels trying to dox many others.” At the time, because five of the 25 were arrested in Spain, I specifically asked Panda if it had been involved. “This time, we were not involved on this case,” came a very clear reply. I had earlier talked to Panda about its involvement in the takedown of the Mariposa botnet. “We co-operate with the Spanish police and some other institution on a regular basis,” he added, “but we were not informed about it.”
AntiSec also makes it clear that it takes exception to PandaLabs’ technical director, Luis Corrons. It’s personal. He is quoted: “Really good news. I have just read that LulzSec members have been arrested and that their main head Sabu has been working as an informant for the FBI. It turns out he was arrested last year, and since then he has been working with Law Enforcement. As I said, really good news :)” He is also quoted as saying “sometimes if you want to infiltrate and you have to be one of the criminals, you have to do things that you shouldn’t. In that case, you need to be with law enforcement.” To be frank, neither of these statements sound like the Luis Corrons I know – but time will unravel all.
Perhaps more worryingly, AntiSec also claims to have back-doored Panda’s security products. Again, Panda is categoric: “Neither the main website http://www.pandasecurity.com nor http://www.cloudantivirus.com were affected in the attack. The attack did not breach Panda Security’s internal network and neither source code, update servers nor customer data was accessed. The only information accessed was related to marketing campaigns such as landing pages and some obsolete credentials, including supposed credentials for employees that have not been working at Panda for over five years.”
The difficult thing, however, is to see the wider picture and to determine what is really going on. Remember Luis comment: “you have to do things that you shouldn’t.” Well, law enforcement has certainly been doing that in recent years. There’s the German police spyware, and the FBI’s very own CIPAV – and God know’s what that we haven’t heard about. So let’s look at the last week. Twenty-five Anonymous arrests rapidly followed by the disclosure that the Anonymous free DDoS tool (slowloris) had been poisoned with the, frankly, most well-known and feared malware of the day – Zeus – closely followed by charges against the main figures in LulzSec. That reads like a campaign organized by a marketing company to discredit Anonymous and sow seeds of distrust.
Read the DDoS-hacked announcement from Symantec here. Make up your own mind, but to me it simply doesn’t hang together properly. I’ve got a question mark there. Did the FBI poison slowloris? Now go back the Stratfor hack (late December 2011). It happened after Sabu became an informant, yet he is charged over it. Anonymous very clearly denied any involvement, stating “Sabu and his crew are nothing more than opportunistic attention whores who are possibly agent provocateurs.” And yes, Anonymous knew that Sabu had been turned by the FBI. But the wider and more worrying question is this: if Sabu was already working for the FBI when LulzSec hacked Stratfor, does that mean that Stratfor was sacrificed by the FBI on the altar of misinformation? As Luis is quoted: “you have to do things that you shouldn’t.” But if this is true, it’s going too far.
Is the AV industry showing signs of exasperation at users’ apathy?
I wrote about the March 8 deadline for remaining DNSChanger victims to get clean or lose their internet in Infosecurity Magazine: DNSChanger poses a new threat to its victims.
But I had two late comments from anti-virus people currently in the States and separated by the trans-Atlantic time difference. They both echo Graham Cluley of Sophos’ comment that “if this is the only way to wake the affected users into sorting out the problem, so be it.”
Panda Labs’ Luis Corrons used remarkably similar language. “At least this will make affected people react and secure their computers,” he told me.
And ESET’s David Harley said, “Pragmatically, I don’t have a problem with this: law enforcement doesn’t have a specific responsibility for maintaining service for infected machines.”
But reading between the lines, I suspect that any anger is really directed not at the infected users being apathetic with their own security, but that the nature of the infection makes further infection likely. Such users are being apathetic with other users’ security; and that’s really not on.