Archive
Microsoft’s new secret weapon: listening to its customers
I am not Microsoft’s greatest fan. It is a dinosaur stuck on the beach while the fleeter of foot are soaring through the clouds. The reality is that it has no, and has never had, any visionaries. Even its domination of the desktop was more down to luck and sharp practices than genuine vision.
It was lucky that Gary Kildall rejected IBM’s overtures, else there would never have been an MS-DOS; and it was sharp practices that killed off Digital Research — its one serious and technically superior competitor. It was lucky that Apple demonstrated the value of Xerox Parc research and paved the way for Windows. It was lucky Jobs was so far ahead of his time he thought he could have a walled garden in the ’80s; and almost destroyed Apple in the process.
But it was sheer arrogant blindness that made Gates think he could ignore the internet. For the last two decades Microsoft has been forced into playing catch up; but catch up never works if you don’t have the vision to get ahead of the competition.
Now, in just one area, Microsoft is showing visionary signs that could differentiate it from all of its competitors. Microsoft has started listening to its customers rather than imposing its will on its customers.
While Facebook is telling everyone that they don’t want privacy, Microsoft is listening and saying, OK, we will give you privacy. While Google is fighting the European Union over privacy and cloud storage, Microsoft is listening to the EU and saying, OK, we can accommodate and store European data in European data centres.
Now, it’s not as simple as that. The US government can still demand customer data from Microsoft’s European data centres simply because Microsoft is a US company. But it’s making that data much more defensible, and telling the EU that it is willing to cooperate rather than fight.
Similar over privacy. When it became clear last week that Microsoft had, quite legally, searched the emails of one of its customers concerning the theft of Microsoft IP, it knew there would be privacy issues. It immediately said two things: firstly that it would in future get a pseudo warrant from an independent lawyer who had previously been a judge, and secondly that it would include its own searches in future ‘transparency reports’ (the ones that publish the number of law enforcement searches).
It wasn’t enough for the privacy advocates who pointed to the hypocrisy of criticising NSA warrantless surveillance and then doing its own.
To Microsoft’s great credit, within a week, it has listened, heard and understood. Brad Smith announced yesterday,
Effective immediately, if we receive information indicating that someone is using our services to traffic in stolen intellectual or physical property from Microsoft, we will not inspect a customer’s private content ourselves. Instead, we will refer the matter to law enforcement if further action is required.
We’re listening: Additional steps to protect your privacy
Is this a new Microsoft — the genuinely ‘listening’ company? It no longer dominates the world’s operating systems, and is losing ground on desktop office software. But it seems to be doing one thing that none of its competitors are doing. It is listening to its customers, and giving them what they want. That alone, over the next few years, could catapult Microsoft back into a leading position.
Is it safe to carry on using Dropbox (post Prism)? Yes and No: Part III
As the dust from Edward Snowden’s Prism revelations begins to settle, it’s time to think again about whether it is safe to use Dropbox. In Part I (June 2011) we said:
You don’t need to stop using Dropbox, or any of its competitors, or Google Docs – just never, ever put anything confidential or legally dubious anywhere in the cloud. Just don’t.
Is it safe to carry on using Dropbox? Yes and No
In Part II (August 2012) we said:
Dropbox is registered in the US, and is subject to the PATRIOT Act – the US authorities are able to demand details of you and your account simply because they want them. So Dropbox is just not safe for confidential or incriminating content (and nor, note, is any other US-based cloud company).
Is it safe to carry on using Dropbox? Yes and No: Part II
What we’ve now learnt from Snowden is that not only can the US authorities (in the form of the NSA and the FBI) demand details of you and your account, they do as a matter of course have access to your actual files. We also know that if you encrypt those files, it will be taken as a red flag and they will pay particular attention to the files, and by implication to you as well.
So if we ask the basic question once again — but expand it from Dropbox to ‘any US cloud-based service’ — we actually come to a similar conclusion but with more riders.
The first part of the question is, is it safe? Absolutely, categorically and emphatically, No. It is not safe to use any US cloud service.
Ladar Levison ran a ‘secure’ email service, Lavabit. Last week he suddenly shut it down after ten years. If you read his statement, you see a man of principle:
I have been forced to make a difficult decision: to become complicit in crimes against the American people or walk away from nearly ten years of hard work by shutting down Lavabit.
(For the Americans, and especially in this instance, ‘the American people’ is a metaphor for ‘everyone in the world’ — it’s just that it has never legally been a crime for the NSA to spy on non-Americans.) It is clear that he is now subject to a court order from the secretive US FISA court — the one that the NSA and FBI use to justify their surveillance practices — complete with a gag order: that is, you must hand over your customers’ data but you may not tell anyone about it. However, it is Levison’s last comment that is specifically relevant here:
I would _strongly_ recommend against anyone trusting their private data to a company with physical ties to the United States.
Kim Dotcom ran the Megaupload website, long since seized — quite possibly illegally — by the US authorities. While fighting extradition from New Zealand to the US he has set up a new and far more secure service, simply called Mega. He has first-hand experience of the reach and practices of the US authorities. His take is this:
Remember, move your Internet business to small nations that are free of conflict and therefore don’t have a massive spy agenda. Look for countries that have robust privacy and human rights laws. Stay out of the US. Don’t even host a single server there.
It looks as if he is preparing to move Mega to Iceland. New Zealand is, after all, one of the Five Eyes global surveillance countries with very close ties to the other four: the US, the UK, Canada and Australia.
But what of the other part of our question: can we carry on using Dropbox (and other US cloud services)? Clearly, we shouldn’t; but can we? As with everything else, it’s a risk-based decision: we have to weigh the risks against the advantages.
Snowden has shown us that the risks are far greater than we thought. The danger, however, is that we will conclude, ‘I’m not doing anything wrong so why should I worry: for me there is no risk.’ Think again. Adam Curtis has shown that the intelligence authorities see a plot behind every shadow: MI5 founded on a lie, maintained on a lie, and still lying today – allegedly. There is no reason to suspect that the NSA and FBI are any different; because if they don’t find the plots they will lose their budget and shrink.
Just because you do no wrong does not mean that they will see no wrong.
So the answer to our question today has to be, technically and possibly, perhaps yes; but realistically, no, no, no. Do not use Dropbox. Do not use Drive. Do not use any US cloud service. And if you are already doing so, get ready to move as early as possible to a non-US service. Don’t trust Europe — it is too closely allied to the US. As Dotcom suggests, Iceland currently looks attractive (at least until it joins the EU and gets caught up in EU subterfuges and becomes just another US and US-business puppet). As things currently stand, quite frankly the only secure solution is do not use cloud.
See also: Is it safe to carry on using Dropbox (client vulnerability)? Yes and No: Part IV, which discusses the latest ‘vulnerability’ in the Dropbox client (31/08/2013)
Toward a new strategy for Microsoft
Back on 7 August I suggested that Microsoft’s plan for its own tablet was a big mistake (A Microsoft-made tablet? Big mistake). I may have been wrong – but only if it is part of a completely new and wider strategy.
Let’s look at the Big 4: Apple, Google, Microsoft and The User.
Microsoft’s strategy is built on the predominance and continued dominance of the PC. Without the PC there is only a small Microsoft – and the PC is in decline, and possibly a terminal decline. Microsoft’s strategy is in decline.
Apple’s strategy is built around owning everything, both hardware and software – and charging an obscene price for that monopoly. So far it has worked very successfully; but if you listen to the undercurrents from The User there is growing User dismay over both the price of that monopoly, and the frequency with which loyal subjects are asked to dump existing product and buy new product. Apple’s strategy is at the apex, and the only way is down (with a slight delay when it dumps OS/X in favour of desktop iOS).
Google’s strategy is to base everything in the cloud, and to own the cloud. This makes distribution very, very cheap, and upgrades cheap, seamless and invisible to the User. Google is proving very, very successful in this strategy.
But what about The User? The User’s strategy is to demand everything now, preferably free (but at least very cheap), anywhere and anytime. Microsoft provides none of this. Apple provides some, but not much, of this. Google provides it all.
So on current strategies, Microsoft is doomed, Apple will decline while Google will grow and thrive. (Incidentally, Amazon seems to have seen the writing, and I rather suspect that all three will have to watch out for Amazon in a few years time.)
But what if Microsoft has also finally come to its senses? What if the Microsoft tablet is not just a one-off foray into hardware, but part of a completely new strategy aimed at combining Apple’s hardware/software monopoly approach with Google’s cloud efficiency?
There are growing rumours that Microsoft is about to switch from, say, 3-yearly Windows releases to yearly releases. This makes no sense whatsoever under the current strategy. Expecting users to buy a new operating system every year won’t wash. Unless…
Let’s say that the MS plan is not new operating systems delivered in box or on disk, but new downloads delivered from the cloud just as its current patches are delivered every second Tuesday of the month. This model would require something like an annual license for the OS rather than a fixed price for the box. If that license were around £25 per year (preferably less), few users could say that use of Windows for just £2 per month is excessive. Let’s now take that to the logical conclusion: Windows and Office both migrate to the cloud and are both upgraded or patched on a continuous basis, as and when required, and paid for on a low-cost rolling license.
So Microsoft’s new strategy could be to own both hardware and software – starting with its own tablet but moving into phones (perhaps by buying Nokia?) and desktops (perhaps by buying Dell or Acer, or even building new from scratch?) – in mimicry of Apple; and then maintaining its software in and distributing from the cloud in mimicry of Google. Such a strategy would combine the best of all possible worlds; and while it is by no means certain that Microsoft could do it, if successful it could reverse the decline of Microsoft.
Google bashing in Europe: politics or business?
Later this week Jeff Gould, the president of SafeGov.org, will publish an article titled European privacy ruling has far-reaching implications for Google Apps in Europe. It discusses the recent findings of the Article 29 group (the EU’s data protection working party) led by the French CNIL (equivalent to the UK’s ICO) on Google’s new privacy policy, and argues,
If fully applied, the ruling could effectively shut down deployments of Google Apps by European governments, schools and enterprises, at least until Google makes the changes the EU regulators are seeking.
This raises a number of other questions – for example, is the European Commission’s love affair with the cloud heading for an impasse with its own regulators? Back in September the EC issued a ‘communication’, Unleashing the Potential of Cloud Computing in Europe. It concluded with a call
upon Member States to embrace the potential of cloud computing. Member States should develop public sector cloud use based on common approaches that raise performance and trust, while driving down costs. Active participation in the European Cloud Partnership and deployment of its results will be crucial.
Last week, ENISA published an excellent overview of the Privacy considerations of online behavioural tracking, which I thoroughly recommend. It tries to draw a distinction between behavioural tracking and behavioural advertising; but the reality is that this is probably a technical rather than practical separation. This is likely to become the crux of Europe’s problem: it wants to maximise the cloud, accepts that it must allow commercialisation, but politically needs to ensure privacy – and the two things might simply be incompatible. As Peter Hustinx, the European Data Protection Supervisor said in his Opinion on Friday,
the use of cloud computing services cannot justify a lowering of data protection standards as compared to those applicable to conventional data processing operations.
In other words, as of right now, the EC’s desire to unleash the potential of cloud computing is incompatible with the need to maintain existing data protection standards. But we needn’t worry too much: it will all, as King John might have said, come out in the wash. Big business will give a little, the regulators will give a little, and the EC will twist and squirm a lot – and we’ll all be able to use the cloud happily.
The question is, will it be with Google? That’s the second issue coming from the Article 29 working party: has Europe got it in for Google? In October, Ars Technica commented:
The French seem to have an appetite for regulating the Internet, and for going after Google in particular. A new proposed law would force Google to make payments when French media show up in news searches; but Google has responded, in a letter to French ministers, that it “cannot accept” such a solution and would simply remove French media sites from its searches.
Two weeks later, Le Canard Enchaîné reported that France had made a €1 billion tax claim against Google and was using this as a bargaining chip in the newspaper content dispute. France, of course, with its current socialist government, likes to tax everything that moves – but as one of the key movers and shakers within the EU, you have to wonder if it is merely spearheading a wider European antipathy; and if so, where does this come from?
Well, again back in October, Henrik Alexandersson [a ‘Swedish libertarian, working for the Pirate Party in the European Parliament’] attended a luncheon seminar organized by ICOMP, the Initiative for a Competitive Online Marketplace (funded, it would seem, by Microsoft).
However, already when we received the seminar documents at the entrance – we realized that this really was something else: A Microsoft-funded Google Bashing lunch.
Google Bashing is a very popular sport in the EU, these days.
Alexandersson was so annoyed by the initial talk by “one of Microsoft’s lawyers, Pamela Jones Harbour… speaking about everything that Google does wrong,” that he and his party got up and left. But privacy, he says,
is not what Google Bashing in Brussels is about. Here it is rather a question of a number of Google’s competitors trying to whip up political criticism, for business reasons. They simply don’t like that Google more or less own the search market.
So here’s a thought. Is that anti-Google sentiment in Europe ‘political exploited by business’, or ‘business exploited by politics’? It’s a moot point. Either way, Google should be in no doubt that it has powerful adversaries in Europe.
Is it safe to carry on using Dropbox? Yes and No: Part II
Ever since the news of a potential breach at Dropbox emerged, my old post “Is it safe to carry on using Dropbox?” has been getting an elevated number of hits. It is time perhaps to update.
Firstly, what’s this about a breach? Well, Dropbox wasn’t breached in the traditional sense of the word. The likelihood is that a number of Dropbox users had the same log-in credentials (email address and password) that they used on a different web account that was breached. The criminals were able to reuse the credentials stolen from elsewhere, and gain access to a number of Dropbox accounts.
Unfortunately, one of these accounts belonged to a Dropbox employee. The criminals gained access to his account and found a file containing an unknown number of users’ email addresses. It was probably these users that were subsequently spammed, leading to the suggestion that Dropbox had been hacked.
This leaves us two questions: is Dropbox safe to use; and what lessons should we learn?
Dropbox is no more nor less safe than it was before; that is, it is not safe. This for two reasons: firstly, it is in the cloud; and secondly, Dropbox is a US company. You don’t know what is happening in a cloud that is not your own; so it is not safe. Dropbox is registered in the US, and is subject to the PATRIOT Act – the US authorities are able to demand details of you and your account simply because they want them. So Dropbox is just not safe for confidential or incriminating content (and nor, note, is any other US-based cloud company).
But why worry if the data you store is neither of these? You can increase the level of security by locally encrypting the files (with something like TrueCrypt) and storing only encrypted files. The basic rule is simple: if it is important that nobody else ever sees the data, don’t use Dropbox; if it doesn’t matter if other people see your files, you can use Dropbox. If you’re somewhere in-between, encrypt.
What should we learn from this? Well, it is good that Dropbox has or will be initiating additional security – including two-factor authentication. This will make your data more safe from hackers, but it has no effect on law enforcement intrusion. And judging from Google’s 2FA, few people will bother using it.
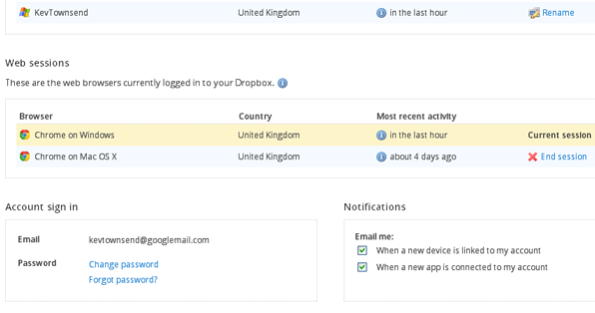
I also very much like the new security page (partial screenshot below). It’s available at your Dropbox settings location, and shows who has recently accessed your account and who is currently accessing your account. This is certainly worth checking regularly. Note also that this is where you change your Dropbox password.
But despite this good response from Dropbox, the fact remains that these are reactive and not proactive steps. Security is still an afterthought, added on to systems rather than designed into them. That’s one lesson we don’t seem able to learn. Secondly, it is sad that a Dropbox employee should be guilty of fundamental security no-nos: he stored a file with user emails in plaintext; and he was reusing the same password on at least two different accounts.
These are the main lessons that we all need to learn: do not trust other people or systems to do security for you. It is your, not their, responsibility (or at least, even if it is their responsibility, you cannot assume they will do it).
And finally, and fundamentally, and beyond all others: when will we ever learn to stop re-using the same password on multiple accounts? Tens of millions of passwords have been stolen from tens of major providers this year alone – and that’s just the ones we know about. Are you sure that your own password is not included? If it is, and you re-use it on multiple accounts, then you simply don’t know who has access to your accounts. And if that includes your email account or bank account, not to put too fine a point on it, you’re screwed.
So, is Dropbox safe? Probably not; but that doesn’t mean we shouldn’t use it under certain circumstances. I shall certainly carry on using it. But are we safe? Absolutely not until we start using unique, strong passwords for every different account. Hint. Use a good password manager.
Update: the revelations from Edward Snowden concerning US government access to cloud services, which will include Dropbox, adds new urgency to considering the use of Dropbox. See our latest commentary following Edward Snowden’s Prism revelations: Is it safe to carry on using Dropbox (post Prism)? Yes and No: Part III
See also: Is it safe to carry on using Dropbox following the DMCA takedown revelations? (03/31/2014)
Is it safe to carry on using Dropbox with Condoleezza Rice on the Board? (04/14/2014)
News stories on Infosecurity Magazine: 17, 18, 21 and 22 May, 2012
My recent news stories…
You don’t need to be hacked if you give away your credentials
GFI Software highlights the problems of users’ carelessness with their credentials: who needs hacking skills when log-on details are just handed over?
22 May 2012
A new solution for authenticating BYOD
New start-up SaaSID today launches a product at CloudForce London that seeks to solve a pressing and growing problem: the authentication of personal devices to the cloud.
22 May 2012
New HMRC refund phishing scam detected
Every year our tax details are evaluated by HMRC. Every year, a lucky few get tax refunds; and every year, at that time, the scammers come out to take advantage.
22 May 2012
UK government is likely to miss its own cloud targets
G-Cloud is the government strategy to reduce IT expenditure by increasing use of the cloud. It calls for 50% of new spending to be used on cloud services by 2015 – but a new report from VMWare suggests such targets will likely be missed by the public sector.
21 May 2012
New Absinthe 2.0 Apple jailbreak expected this week
The tethered jailbreak for iOS 5.1, Redsn0w, still works on iOS 5.1.1. This week, probably on 25 May, a new untethered jailbreak is likely to be announced at the Hack-in-the-Box conference.
21 May 2012
TeliaSonera sells black boxes to dictators
While the UK awaits details on how the proposed Communications Bill will force service providers to monitor internet and phone metadata, Sweden’s TeliaSonera shows how it could be done by selling black boxes to authoritarian states.
21 May 2012
Understanding the legal problems with DPA
We have known for many years that the EU is not happy with the UK’s implementation of the Data Protection Directive – what we haven’t known is why. This may now change thanks to the persistence of Amberhawk Training Ltd.
18 May 2012
Who attacked WikiLeaks and The Pirate Bay?
This week both the The Pirate Bay and WikiLeaks have been ‘taken down’ by sustained DDoS attacks: TPB for over 24 hours, and Wikileaks for 72. What isn’t known is who is behind the attacks.
18 May 2012
BYOD threatens job security at HP
BYOD isn’t simply a security issue – it’s a job issue. Sales of multi-function smartphones and tablets are reducing demand for traditional PCs; and this is hitting Hewlett Packard.
18 May 2012
25 civil servants reprimanded weekly for data breach
Government databases are full of highly prized and highly sensitive personal information. The upcoming Communications Bill will generate one of the very largest databases. The government says it will not include personal information.
17 May 2012
Vulnerability found in Mobile Spy spyware app
Mobile Spy is covert spyware designed to allow parents to monitor their children’s smartphones, employers to catch time-wasters, and partners to detect cheating spouses. But vulnerabilities mean the covertly spied-upon can become the covert spy.
17 May 2012
Governments make a grab for the internet
Although the internet is officially governed by a bottom-up multi-stakeholder non-governmental model, many governments around the world believe it leaves the US with too much control; and they want things to change.
17 May 2012
News stories on Infosecurity Magazine, Tuesday 15 and Wednesday 16 May, 2012
My news stories for yesterday and today…
Canada’s interception bill C-30 dead in the water?
For all intents and purposes, the bill is dead; it appears that Public Safety Minister Vic Toews’ plans to ease police tracking of those who use the web for criminal purposes has been shelved.
16 May 2012
New iOS jailbreak expected next week
This year’s Hack-in-the-Box Netherlands security conference takes place next week at the Okura Hotel in Amsterdam, and will be the first ever week-long HITB event. A new iOS jailbreak is expected.
16 May 2012
UK companies are cyber self-confident
A new study by BAE Systems Detica shows that British business is pessimistic about security in general, but strangely confident about its own.
16 May 2012
The danger in service operators’ censorship filters
Yesterday we reported that the German Pirate Party had been ‘accidentally’ blocked by an automatic content filtering system used by many German schools. And yesterday the Open Rights Group and the LSE Media Policy Unit published a new report: Mobile Internet censorship: What’s happening and what we can do about it.
15 May 2012
Security is driving cloud adoption
In its 2012 Disaster Preparedness survey, Symantec finds a link between the three great movers of contemporary computing: virtualization, cloud computing and mobility. That link, surprisingly, is security – or more specifically, it is the need for adequate disaster recovery capabilities.
15 May 2012
How safe is your iCloud data?
Last month, Ars Technica asked the question, ‘Can Apple give police a key to your encrypted iPhone data?’ It concluded that it probably could not for the data on the device; but probably could for data stored in iCloud. Now the question has less relevance, with the latest version of ElcomSoft’s EPPB and the increasing use of iCloud.
15 May 2012
Keynote sessions from Infosecurity Europe 2012 – and a few other stories
Infosecurity Europe is over for another year. If you weren’t there, well I just suggest you make sure you get there next year. Meantime, here’s my take on a couple of the announcements and almost all of the keynote sessions:
Infosecurity Europe 2012: Minister of State for Universities and Science introduces the 2012 security breaches survey
The challenge, says the Rt Hon David Willetts, is that in order to get the economic and social benefits that the internet offers, we need to first tackle cyber security.
24 April 2012
PwC and Infosecurity Europe release the latest Information Security Breaches Survey
Significant attacks more than double, but one-in five companies still spend less than one percent of their IT budget on security, and more than half of small organizations do no security training at all.
24 April 2012
Russian cybercrime: what Russia is doing, and what it should be doing
Russian security company Group-IB says Russian cybercriminals made £2.3b in 2011; Russian-speaking cybercriminals made more than $4b; and worldwide, cybercriminals made more than $12.5b.
24 April 2012
Trustworthy Internet Movement Launches Pulse Tracker
The problem, says Pulse, is that we are telling users that this site has SSL, so it’s secure. That’s not necessarily true. We are promulgating a false sense of security, and we need to fix that.
25 April 2012
Infosecurity Europe 2012: defining risk management in the context of information security
The three companies represented on the keynote panel (G4S Secure Solutions, Steria UK, and Skipton Building Society) are very different; and their CISOs have very different views on the functioning of risk management within infosec.
25 April 2012
Infosecurity Europe 2012: the rising role of the CISO
Chaired by Quocirca’s Bob Tarzey, Network Rail’s CISO Peter Gibbons and Yell’s CISO Phil Cracknell led a lively discussion on the current and future role of the CISO.
25 April 2012
Ipswitch survey reveals the extent to which IT is losing control over data
IT needs governance; but users are choosing simplicity. In choosing and using their own non-sanctioned methods for data transfer, users are causing IT to lose control over its own data.
25 April 2012
Infosecurity Europe 2012: AET & APT – Is this the next-generation attack?
Advanced persistent threats (APT) and advanced evasive techniques (AET): what are they, who’s doing them, and what can we do about them?
26 April 2012
Has the time come to dump anti-virus?
Bit-9 asks the question that dare not be spoken: is anti-virus beyond its sell-by date? And is BYOD the final straw?
26 April 2012
Infosecurity Europe 2012: The ICO on better regulation and better infosec
Christopher Graham, the UK Information Commissioner, talks about his role as an information regulator and facilitator at Infosecurity Europe in London
26 April 2012
Infosecurity Europe 2012: Are we smart enough to secure smartphones?
Three heads of security from three very different organizations came together to discuss their practical and very different experiences in introducing a company BYOD strategy.
26 April 2012
Infosecurity Europe 2012: The insider threat – is it real?
While the primary security stance faces outwards and is designed to keep hackers and malware outside of the system, organizations are increasingly aware that their own staff are also a potential – and in some cases an active – threat.
27 April 2012
Infosecurity Europe 2012: The cloud – do you really know what you’re getting in to?
The cloud is new; but it’s been around for years. It’s insecure; but more secure than we fear. Two practitioners discussed the cloud of FUD.
27 April 2012
It’s the lack of understanding of virtualization that makes security an issue
A new study from Kaspersky Lab confirms an earlier one from Crossbeam Systems: it’s a lack of knowledge about virtualization that leads to fear for its security.
26 April 2012
My news stories on Infosecurity Magazine
Last week’s news stories (Jan 30 to Feb 3):
Security researchers break satellite phone encryption
German researchers have cracked 2 satellite phone encryption codes – huge implications.
EU publishes 10 Myths about ACTA
EU says ACTA ain’t bad, just misunderstood.
VeriSign repeatedly hacked in 2010
VeriSign was repeatedly hacked in 2010, and never even told its own senior management.
Science and Technology Committee publishes Malware and Cyber Crime report
Commons committee makes recommendations on how to tackle cybercrime.
New development in post-transaction banking fraud
Banking malware now seeks to divert telephone calls between banks and customers.
Counterclank is not malware, just aggressive adware
Contrary to Symantec’s initial claim, Android’s Counterclank (Apperhand) is not a trojan.
Major UK companies still not blocking porn namesakes
UK companies remain open to cybersquatting by YourBrandName.xxx
New Forrester Report: Big Data Risks
Forrester describes how to secure Big Data.
Resilience is the key to security says World Economic Forum
WEF suggest an holistic view of resilience to risk rather than an isolated view of prevention.
A call for a new standard in infosec training and awareness
We need a new standard to improve security awareness in users.
IE6 users: no longer caught between a rock and a hard place
A new product allows legacy IE6 applications to run in new versions of the browser.
75% of all new malware are trojans
PandaLabs 2011 report is full of facts, figures and information.
Spam and phishing are growing problems: DMARC has the answer
A new standard is being developed to help stop spam and phishing.
CSO Interchange: Cloud concerns are largely propaganda
Misunderstandings about the cloud make it seem a problem rather than an opportunity.
Up to five million Androids infected with Counterclank
Android’s largest ever infection reported by Symantec.
I’m not behind Kelihos botnet, claims Sabelnikov
Man named by Microsoft says I didn’t do it, guv.
Whitelisting Vs Blacklisting
The fundamental principle that underpins all security is the need to stop bad people or processes while allowing good people or processes. So security is about access control; and access control starts with identity. But identity on its own is not enough – we also need to understand purpose. We need to identify the person or process, and decide whether the intent is good or bad.
This article was written for, first published by, and reprinted here with the kind permission of
Infosecurity Magazine.
Consider passports in the physical world. They prove identity, but do not tell us intent: is the intent of that identity to do good or bad? We reinforce identity with lists of known intent: a whitelist of frequent flyers or VIPs whose intent is known to be good, and a blacklist of terrorists and bad people whose intent is known to be bad.
Cyber security is the same: based on identity and intent we maintain whitelists of known good (or at least acceptable) behavior, and blacklists of known bad (or unacceptable) behavior. Security is largely based on how we use these lists. In the main, we either allow what’s on the whitelist and prevent everything else; or we prevent what’s on the blacklist, and allow everything else. We tend to concentrate on one approach or the other: whitelisting or blacklisting.
Keeping our computers clean is a good example. In the beginning the anti-malware industry simply blacklisted the bad things. But now the alternative is gaining traction: whitelisting the good things. We need to know which is best for maximum security.
In favor of blacklisting
The basis of anti-virus security is a blacklist of all known malware. The technology is based on blacklisting because in the beginning there were very few viruses. A primary advantage of blacklisting is that it is conceptually simple to recognize a few bad things, stop them, and allow everything else.
A second argument in favor of blacklisting is ‘administrative ease’. The maintenance of blacklists is something we can delegate to trusted third parties – in this instance the anti-virus companies. They in turn, particularly with the advent of the internet, can automatically update the blacklist for us. Basically, we don’t have to do anything.
Whitelisting is different: it is difficult to delegate to a third party the decision on which applications we need. “Whitelisting would be the perfect solution if people only have one computer that is never patched and never changed,” explains Dan Power, UK regional manager for anti-spam company Spamina. “Intellectually it makes perfect sense to only allow execution of the files that you know to be good.” But maintaining this whitelist is difficult. “The problem comes when you have to register or re-register every DLL every time you install a new, or patch an existing, application. Which people do you allow to install their own software, and which people do you stop? And which bits of software can make changes and which can’t? It becomes more of an administrative rather than intellectual issue.”
David Harley, senior research fellow at ESET LLC, agrees: “Whitelisting – which isn’t much different in principle to the integrity checking of yesteryear, requires more work by internal support teams and interferes with the end-users’ God-given right to install anything they like; which is more of a problem in some environments than in others.”
That’s not to say that some people consider such delegation to be impossible. Last year Microsoft’s Scott Charney proposed a form of whitelisting for access to the internet; that is, only users with an internet health certificate for their computer should be allowed access. He has few supporters in the security industry. Power, again: “If computers were like televisions, with just one base operating system that was never changed, then it’s doable. But in the real world there are just so many variables associated with Windows and all the bits of software that have ever been written for Windows, that it’s almost impossible to be able to say what is and what is not a clean or healthy computer.”
Jennifer Gilburg, director of marketing at Intel, sees a different problem with this type of whitelisting. “Think of e-commerce,” she said. “An online trader would rather take the occasional fraudulent transaction than risk turning away a good transaction. So the thought of blocking a user from coming onto the internet until they are trusted would terrify many of the e-commerce providers who make their livelihood on the basis of the more users the better. I suspect that most of the e-commerce world would be lobbying very hard to put down this version of whitelisting.” So one of the strongest arguments in favor of blacklisting is the problems concerned with whitelisting.
In favor of whitelisting
However, Henry Harrison, technical director at Detica, points to a specific problem with blacklisting. “Anti-virus blacklisting,” he says, “is based on the idea of detecting things that are known to be bad and stopping them. But it simply cannot detect things that are bad, but not known.” Zero-day threats are not known simply because they are zero-day threats – and blacklisting merely lets them in as if they were good. “What we are seeing today,” continued Harrison, “is a lot of targeted, covert attacks – external infiltration into corporate networks with a view to the theft of valuable information using techniques that are specifically designed to evade blacklisting – and one possible response to zero-day threats is whitelisting.”
Lumension’s senior vice president Alan Bentley, points to the sheer volume of malware as a problem for blacklisting. “Blacklisting,” he explains, “is threat centric. Whitelisting is completely the opposite: it’s trust centric. While blacklisting malware used to be adequate, the whole threat arena in the cyberworld has exploded to such an extent we now have to question whether blacklisting alone is still good enough.”
This is what Lumension does: it protects end-points (such as the PC on your desk) by making it administratively easy to create and maintain a whitelist of acceptable applications while supporting that with a blacklist of malware. “We believe that if you look at the two things together, whitelisting should absolutely be the first line of defense for any organization, because it simply stops everything that isn’t approved. But what it cannot do is remove malware once it has embedded itself into a machine.”
Bit9, like Lumension, is a company that concentrates on whitelisting. “The premise of application whitelisting is very simple,” explains Harry Sverdlove, chief technology officer. “What you want running on your system is a much smaller set than what you don’t want. We apply this model to other aspects of security in our life. For example, who do you let into your home? You don’t keep a list of everyone bad in the world. Rather, you only allow people into your home whom you trust.”
What we’re seeing is that the explosion in malware (in excess of 2 million new pieces of malware every month) is exactly what makes us question whether blacklisting remains realistic. “As a general rule, whitelisting is always more secure than blacklisting,” continues Sverdlove. “But it requires you to think more about how software arrives on your systems and whether or not it is trustworthy. That’s why a software reputation database can be an invaluable aid in whitelisting – it provides a trust rating on software, like a trusted advisor or background security check service, that can make the process more manageable. If everything you run comes from a well-known third party, approving software almost exclusively from a cloud based reputation service can be enough. In most cases, however, you also have your only custom or proprietary software. An effective and robust whitelisting solution allows you to combine both your own policies along with those from a reputation database.”
So we should ask ourselves whether we can harness the power of cloud-based reputation systems to generate our whitelists. Spamina already uses this methodology to produce its blacklist of spam sources, calling on six separate reputation blacklists, but never relying on just one (thus minimizing the chance of false positives).
The anti-virus industry
“I’ve never advocated AV as a single defensive layer,” says ESET’s Harley. “Whitelisting can and does work for businesses, though it works best where there’s an authoritarian IT culture, rather than laissez-faire: restricted privileges and so on. I wouldn’t generally recommend it as a complete substitute for AV, but if it’s implemented properly, it’s a rational multi-layering strategy. It does, at a stroke, obviate most of the risk from social-engineering-dependent threats. In fact, most AV nowadays does have some whitelisting ability, though how it’s done and to what extent varies enormously.”
Ram Herkanaidu, security researcher at Kaspersky Lab UK, has a similar viewpoint and acknowledges the increasing relevance of whitelisting. “As the amount of malware increases,” he said, “I can see at some point it could be more efficient to only allow whitelisted files to be run in an organization. The idea has been around for a while but many things have to be taken in consideration, like software updates (especially windows updates), remote users, smartphone and non-standard users. Ideally as well as using the vendor’s whitelist you could have a local whitelist too. So while the idea of having a, ‘trusted environment’ is very appealing, in practice it is difficult to achieve.”
Kaspersky, like other AV companies, is already looking into whitelisting. “We have been running a whitelist program to collect information about all known good files,” continued Herkanaidu. “The files are sent to us by our whitelist partners and also through our Kaspersky Security Network (KSN). This is our ‘neighborhood watch’ which users become part of when they install Kaspersky Internet Security. Information about all unknown files is sent to our ‘in the cloud’ service and automatically analyzed. If malicious, all computers within the network are protected. If it is not malicious it will be added to our whitelist. This has two benefits for our customers: it will reduce the risk of false positives, and will increase scan speeds. In this way we have been able to collect information – not the files themselves – about millions of files.”
Whitelisting or blacklisting?
So what’s our conclusion? Whitelisting is fundamentally the better security solution. If something isn’t on the list, it gets stopped – the default position for whitelisting is secure. But with blacklisting, if something isn’t on the list it gets allowed – the default position for blacklisting is insecure. Against this, the administrative effort involved in blacklisting is minimal compared to whitelisting; and the difference increases as the size of the whitelist increases. However, the efficiency of blacklisting decreases as its size increases. You could almost say that whitelisting is best with a small whitelist, while blacklisting is best with a small blacklist. However, since neither of these situations is likely to occur in the real world, our conclusion is simple: you need both.