Archive
Demonstrating that anti-virus doesn’t just depend on up-to-date signatures
The granddaddy of security software is the venerable anti-virus. But the mother of all attacks is the zero-day targeted exploit. Vendors of new products specifically designed to protect against the latter continuously insinuate that anti-virus no longer works — ergo you need to buy their shiny new product to stay safe.
These vendors point out that the attacker merely needs to modify the malware to change its signature to instantly create a pseudo-0-day that defeats AV signature engines. And to prove their point, they will submit the pseudo or actual 0-day to VirusTotal to demonstrate that few if any AV products actually detect it.
This gives a false impression. VT basically just submits the sample to the signature engine — which won’t detect 0-days. But the AV industry long ago accepted that signatures alone are not enough, and built additional behavioural defences into their products. These are not generally tested by VT.
So when a VirusTotal report says a particular sample was not detected by your own AV software, that doesn’t necessarily mean that it would not be detected by the AV product’s behavioural methods in situ on your PC. It’s a difficult thing to prove, and it has left the anti-virus industry disadvantaged against the arguments of the newer products.
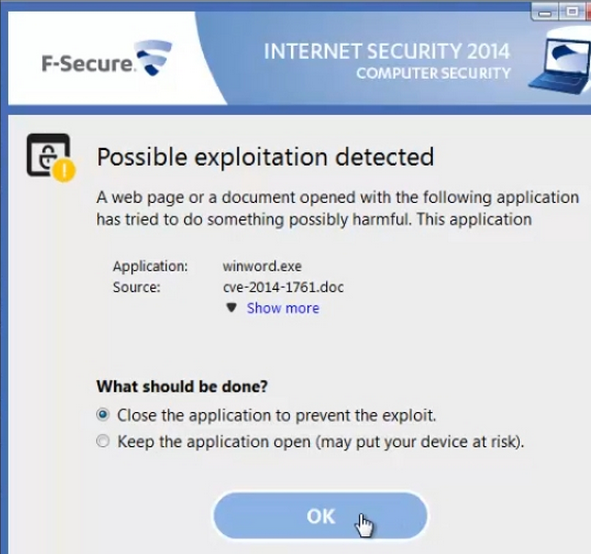
Now F-Secure has tested it. There is a new 0-day MS Word/RTF vulnerability that is expected to be fixed by Microsoft in this week’s Patch Tuesday patches. For the moment, it remains a 0-day.
“Now that we got our hands on a sample of the latest Word zero-day exploit (CVE-2014-1761),” reported Timo Hirvonen, senior researcher at F-Secure, yesterday, “we can finally address a frequently asked question: does F-Secure protect against this threat? To find out the answer, I opened the exploit on a system protected with F-Secure Internet Security 2014, and here is the result:


I would suggest that F-Secure is not the only AV software able to detect the worrying behaviour, if not the signature, of the 0-day without ever seeing the malware.
The reality is that no software can guarantee to stop all malware; but anti-virus software remains the bedrock of good security. Adding to it is prudent; replacing it is foolhardy.
Ransomcrypt can be defeated by AV when the criminals are incompetent
 There is a window of opportunity for anti-virus software to detect and defeat the new style crypto ransomware. This is the malware that scrambles your files with unbreakable encryption that can only be reversed through ‘buying’ the decryption key from the criminals for several hundred dollars.
There is a window of opportunity for anti-virus software to detect and defeat the new style crypto ransomware. This is the malware that scrambles your files with unbreakable encryption that can only be reversed through ‘buying’ the decryption key from the criminals for several hundred dollars.
That window was described by Symantec in its recent discussion on the CryptoDefense malware.
CryptoDefense appeared in late February 2014 and since that time Symantec telemetry shows that we have blocked over 11,000 unique CryptoDefense infections.
How do you block an infection that encrypts? You can block an attack before the infection…
Well, it’s that window of opportunity. Strictly speaking, I suppose Symantec hasn’t blocked the infection, but does manage to block the encryption.
The first thing the malware must do when it infects the computer is report back to the C&C server so that it has a channel to send the decryption key. If it doesn’t do that, the criminals have no way to effect the ransom (other than bluff, which would only work a couple of times). So if the AV software can recognise this behaviour, it has a brief period in which to cut the communication and ‘block’ the encryption.
In this particular instance the criminals have developed a sophisticated trojan that has one fatal flaw.
CryptoDefense, in essence, is a sophisticated hybrid design incorporating a number of effective techniques previously used by other ransomcrypt malware authors to extort money from victims. These techniques include the use of Tor and Bitcoins for anonymity, public-key cryptography using strong RSA 2048 encryption in order to ensure files are held to ransom, and the use of pressure tactics such as threats of increased costs if the ransom is not paid within a short period of time. However, the malware author’s poor implementation of the cryptographic functionality has left their hostages with the key to their own escape.

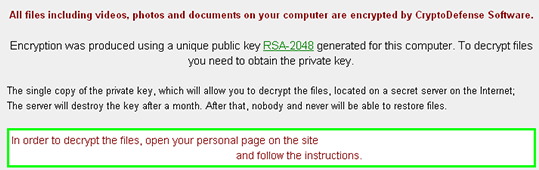

That fatal flaw is to leave a copy of the decryption key on the user’s PC.
With Cryptolocker, the private key was only ever found on servers controlled by the attacker, meaning the attackers always maintained control over the encryption/decryption keys. On investigating how CryptoDefense implemented its encryption, we observed that the attackers had overlooked one important detail: where the private key was stored.
In short, if you use Windows’ own crypto functions, you should know where it stores the decryption key. With CryptoDefense, the criminals either didn’t know or overlooked it, despite its otherwise sophistication. Windows stores a copy of the key on the disk; and CryptoDefense leaves it there.
So in this instance, some basic incompetence from the criminals is the victims’ salvation. But don’t expect it to continue. The criminals will rapidly update the malware to defend their leverage. The best bet is to avoid the infection in the first place — and that means up-to-date anti-malware, and constant vigilance against phishing and attachments.
Android malware is no longer just about premium rate calls
Experts have been warning for some time about the increasing sophistication of mobile malware. Now FireEye has discovered a new variant of Android.MisoSMS — which was already an advanced information-stealing Android Trojan.
Like the original version of the malware, the new variant sends copies of users’ text messages to servers in China. But the newest rendition adds a few features that make it harder to detect, including a new disguise, encrypted transmissions, and command-and-control (CnC) communications that are handled natively rather than over email.
FireEye — Android.MisoSMS : Its back! Now with XTEA
The latest variant seeks to communicate with its C&C server — still located in China — via a selection of hardcoded public DNS servers. This helps defeat sandbox detection and analysis since sandboxes “typically use internal DNS servers and cut off access to outside networks,” explains FireEye. “If the malware cannot access the hard-coded DNS servers, it does nothing and is therefore not detected.”
A further new sophistication is the use of encryption — a variant of the XTEA encryption algorithm — in communication with the C&C server. It is clear that it is malware designed to infiltrate and persist.

It suggests, warns FireEye, “that cyber attackers are increasingly eyeing mobile devices — and the valuable information they store — as targets. It also serves as a vivid reminder of how crucial protecting this threat vector is in today’s mobile environment.”
It’s time for McAfee and Symantec to state clearly that they do not collaborate with governments
When I wrote the piece, Is the AV industry in bed with the NSA, I concluded that on balance it probably is. I have no evidence. It’s just that I cannot believe that an organization complicit in developing and deploying its own malware, and able to ‘socially engineer’ RSA into doing its bidding, would leave AV untouched.
Obviously I spoke to people in the industry. In private conversation with one contact, while accepting his own protestations of innocence, I asked, “What about McAfee and Symantec?” He paused; but then said, “If I had to question anyone, those are the two names that would come to mind.”
I should say, again, that I have no evidence. It’s just doubts born out of the repetition of hyped-up statistics, frequently used by government to justify its actions, and what appears to be preferential treatment from government.
A couple of months later, the Dutch digital liberty group Bits of Freedom wrote to the leading AV companies for a formal position. One of the questions it asked was, “Have you ever been approached with a request by a government, requesting that the presence of specific software is not detected, or if detected, not notified to the user of your software?”
My understanding is that some, but not all, AV companies replied, in writing, that they do not collaborate with governments.
F-Secure’s Mikko Hyppönen spoke yesterday at the TrustyCon conference. I wasn’t there, so this is from The Register’s report:
A surprising number of governments are now deploying their own custom malware – and the end result could be chaos for the rest of us, F-Secure’s malware chief Mikko Hyppönen told the TrustyCon conference in San Francisco on Thursday…
While ESET, F-Secure, Norman Shark, Kaspersky, Panda and Trend Micro replied to Bits of Information, Symantec and McAfee (among others) have not responded, Hyppönen claimed.
Same names. Coincidence? I wonder.
PrisonLocker + CryptoLocker = PowerLocker
This is a bit worrying:


Nothing, but nothing, can guarantee security!

Guaranteeing security merely means you’re clueless and dangerous. But it’s indicative of the panic around CryptoLocker.
Panic, of course, is a universal life force – it gives living energy to any inanimate object. When you add panic to any story, it gains a life of its own; it grows legs and runs.
Panic has now been added to PrisonLocker (AKA PowerLocker), a new encrypting malware being readied for release by a guy called gyx.
But if you read the original and excellent expose published last week by Malware Must Die, you cannot help but have a few questions. For example, each new announcement says release is imminent, but each new announcement doesn’t seem to bring it any closer.
Nor does the author sound much like the traditional hacker. His command of the written language is pretty good. There are relatively few typos or howling grammatical errors and the syntax is Anglo-Saxon – he’s probably British, or at least not American. He reads like a native English speaker. He spells ‘behaviour’ with a ‘u’ (an American or someone brought up on American-English would not), he writes created by the group “Romanian Antisec”. with the fullstop outside of the quotation marks (an American would put it inside).

Fraser Howard, Sophos
So with a few questions of my own, I spoke to Fraser Howard, a security researcher with Sophos. He too was a little puzzled.
“Typically,” he explained, “ransomware falls into one of two camps. The first simply locks the user out; but data and files are not normally modified or encrypted. This is easy to deal with – once the malware is removed, the user is back to normal. It’s more of an annoyance than anything else, scaring the user into paying up.
“The second encrypts the users’ files. The ‘serious’ ransomware families do this, using cryptography correctly to securely encrypt files without leaving the key anywhere accessible. PowerLocker,” he added, “claims to do both lockout and encrypt.”
This is one of the things that puzzles him: why have both? “Seems a bit daft to me – why bother locking them out if you have encrypted their data? The author claims: ‘Even if the user is able to somehow get out of locker screen, files will still be encrypted with practically unbreakable encryption.’
Well, that’s just flawed, illogical thinking.
“It makes me suspicious – it’s indecisive. When I read claims like this, it makes me wonder if the author is actually very capable.” But that’s not all. “Some of the text in the other screenshots [from the Malware Must Die report] make me suspect the author’s skills. Talk about ‘UAC bypass’ and ‘admin privileges’ – well, that’s all very basic stuff used by most malware today.”
My guess is that PrisonLocker was originally intended to be purely locking ransomware. Given the success and publicity surrounding CryptoLocker, gyx decided to add encryption. Not wishing to abandon what he’d already done, he kept the original locking mechanism. But with encryption now perceived as the primary sales incentive, the ‘prison’ epithet was no longer adequate, so he changed the name to ‘power’ locker (crypto locker already being taken).
But there’s one other thing we could consider. gyx is suggesting a purchase price of $100 for his malware. Firstly, he doesn’t seem intent on using it himself. Secondly, that’s remarkably cheap – unless, of course, it’s a ‘loss-leader’ being used to break into a new market.
And that, frankly, is what it seems like to me. A competent and well-educated coder has turned to the dark side, and is using this ‘project’ to get in. He understands software, but he doesn’t necessarily understand malware nor the malware marketplace. He’s selling it rather than planning to use it himself in order to stay one remove from the hacking, infecting and stealing side of malware – he sees himself more as an underworld manager than an underworld foot-soldier.
But saying all that, if PowerLocker is as good (or as bad) as he describes, then it is going to be a dangerous piece of malware. If it’s taken up by some of the better organised criminal groups with access to 0-day exploits, or simply experienced in the use of exploit kits like Magnitude, then PowerLocker could easily become the next PanicLocker.
Is the anti-virus industry in bed with the NSA – why do CIPAV, FinFisher and DaVinci still defeat AV?
September 2013 is the month in which the extent of direct government hacking – as opposed to traffic surveillance – became known.
4 September – WikiLeaks releases Spy Files 3, demonstrating increasing use of third-party hacking tools, such as FinFisher.
6 September – Bruce Schneier writes in the Guardian
The NSA also devotes considerable resources to attacking endpoint computers. This kind of thing is done by its TAO – Tailored Access Operations – group. TAO has a menu of exploits it can serve up against your computer – whether you’re running Windows, Mac OS, Linux, iOS, or something else – and a variety of tricks to get them on to your computer. Your anti-virus software won’t detect them, and you’d have trouble finding them even if you knew where to look. These are hacker tools designed by hackers with an essentially unlimited budget. What I took away from reading the Snowden documents was that if the NSA wants in to your computer, it’s in. Period.
7 September – details of an NSA MITM operation against Google users in Brazil revealed.
12 September – FBI admits that it hacked Freedom Hosting. The implications are that it inserted the malware that monitored visitors, and the almost certainty that the malware was CIPAV.
FinFisher and CIPAV stand out as government operated spyware; but there are others: RCS (DaVinci), Bundestrojaner etcetera – and, of course, Stuxnet and Flame. We’ve known about them for a long time: see
- CIPAV: FBI, CIPAV spyware, and the anti-virus companies (this site, May 2011)
- RCS: Hacking Team’s RCS: hype or horror; fear or FUD? (this site, Nov 2011)
- FinFisher: Use of FinFisher spy kit in Bahrain exposed (Infosecurity Mag, August 2012)
- Bundestrojaner: Chaos Computer Club warns on “German government” communications trojan (Infosecurity Mag, Oct 2011)
This leaves a major question begging: if we’ve known about this malware for such a long time, how come it can still be used? Why doesn’t anti-malware software stop it?
There are two possible reasons that we’ll explore:
- the AV industry, like so many others, is in bed with the NSA
- the AV industry is not as good as the ‘stops 100% of known malware’ claims that it makes – or put another way, virus writers are generally one-step ahead of the AV industry
In bed with the NSA
This has been vehemently denied by every AV company I have spoken to (see the articles on CIPAV and RCS for examples). Bruce Schneier doesn’t believe it is:
I actually believe that AV is less likely to be compromised, because there are different companies in mutually antagonistic countries competing with each other in the marketplace. While the U.S. might be able to convince Symantec to ignore its secret malware, they wouldn’t be able to convince the Russian company Kaspersky to do the same. And likewise, Kaspersky might be convinced to ignore Russian malware but Symantec would not. These differences are likely to show up in product comparisons, which gives both companies an incentive to be honest. But I don’t know.
Explaining the latest NSA revelations – Q&A with internet privacy experts
And yet the possibility lingers. When Flame was ‘discovered’, Mikko Hypponen issued a mea culpa for the industry. Admitting that F-Secure had Flame samples on record for two years, he said,
Researchers at other antivirus firms have found evidence that they received samples of the malware even earlier than this, indicating that the malware was older than 2010.
What this means is that all of us had missed detecting this malware for two years, or more. That’s a spectacular failure for our company, and for the antivirus industry in general.
It wasn’t the first time this has happened, either. Stuxnet went undetected for more than a year after it was unleashed in the wild…
Why Antivirus Companies Like Mine Failed to Catch Flame and Stuxnet
Forget the ‘hand on heart’ for a moment, and consider… That’s the two major government-sponsored malware samples known about and ignored by multiple AV companies for several years. Coincidence? Maybe. But to echo Schneier’s last sentence, I don’t know.
Malware writers are one step ahead of the AV industry
If you listen to the AV marketers, this cannot be true. Every month we hear claims that AV products stop 99.9% to 100% of all known viruses (remember that they ‘knew’ about Stuxnet and Flame, but did nothing). I’ve written on my dismay at this sort of advertising elsewhere (for example, Anti Malware Testing Standards Organization: a dissenting view).
However, if you listen to the foot soldier researchers – and sometimes even higher –within the individual companies, you realise that it is absolutely, inherently, and unavoidably true. Luis Corrons, the technical director at PandaLabs, puts it like this:
The effectiveness of any malware sample is directly proportional at the resources spent. When we talk about targeted attacks (and [CIPAV and FinFisher] are developed to perform targeted attacks) the most important part is the ability to be undetected. Bypassing signature detection is trivial, although it is almost useless too, as most anti-malware programs have several different layers of protection which do not rely on signatures.
The attackers probably know which security solution(s) the potential victim is using. Then it is as ‘simple’ as replicating the same scenario (operating system, security solution, etc.) and verifying that the malware is not being detected. As soon as it is flagged they will change it to avoid detection, until they have the final version.
Once they are done, they will infect the victim and will be spying / stealing information out of him until they are detected. This could be a matter of days, months or even years.
Claudio Guarnieri of Rapid7 said very similar:
Since FinFisher, just as any other commercial spyware, is a very targeted and sophisticated (besides expensive) malware, it’s part of Gamma’s development lifecycle to make sure that they tweaked all the different components to avoid antiviruses before shipping the new FinFisher out to the customers.
The developers likely have their own internal systems to do these testings: think of something as a private VirusTotal. Every time they develop a new feature or a new release, they’ll test it against as many antiviruses as possible and if something gets detected, they debug and try to understand why and find a way around it.
The ‘problem’ with this approach is that they rely on the AV industry not knowing and not having access to their malware: whenever that happens AV vendors react pretty effectively and in fact if you look at FinFisher samples discovered 1 year ago they are now largely detected by most antivirus products.
Conclusion
Is the AV industry in bed with the NSA? The simple fact is that we just do not know. The industry itself denies it – but, well, it would, wouldn’t it? Statistically, since almost every other aspect of the security industry collaborates with or has been subverted by the NSA, my suspicion is that it is. At the very least, I suspect it engages in ‘tacit connivance’.
Are malware developers one step ahead of the AV industry? That depends. As Corrons says, it depends on the resources available to the bad guys, whether that’s NSA, FBI, GCHQ or the Russian Business Network. Well-resourced bad guys will always get in. As Schneier puts it, “if the NSA wants in to your computer, it’s in. Period.” But that probably applies to all governments and all seriously organized criminal gangs engaged in targeted hacking.
But one final comment: nothing said here should be taken to suggest that we don’t need the AV industry. It may not be able to stop the NSA, but it can and does stop a million script kiddie wannabe hackers every day.
see also:
Bits of Freedom seeks clarity from the AV industry on collusion with law enforcement
It’s time for McAfee and Symantec to state clearly that they do not collaborate with governments
Wonderful graphic from AlienVault: The Eternal Life of Malware
But it does make you wonder why the West is so concerned about cyberwar when it is clearly the world’s greatest protagonist. Do as you would be done by, I say.
The inclusion of Shamoon is interesting. Does it imply that AlienVault considers it is state-sponsored by Iran? If so, the current cyberwar score seems to be US/Israel 5, China 1, Iran 1.

BBC finally smells the coffee
“Malware ‘was not from factories’, Microsoft says” is today’s headline. “Several outlets, including the BBC, reported that harmful software was being pre-installed on PCs at the manufacturing stage,” admits the BBC. Actually, it had said “Cybercriminals have opened a new front in their battle to infect computers with malware – PC production lines.” It said that because it didn’t bother reading the Microsoft reports.
And we told them they were wrong five days ago in our own reporting: China is a pariah.
Five days to get it right. Is there an agenda here?
Keep up, or fall behind, as they say.
The irony…
What irony. As I link to my story on over-hyping the China threat, LinkedIn links to a story that over-hypes the same story. This one is from The Independent: “Microsoft admits millions of computers could be infected with malware before they’re even out of the box”. I’m afraid that I missed both the ‘millions’ and ‘before they’re even out of the box’ comments from Microsoft. Oh, no, I didn’t – they’re not there.
My stories for Infosecurity Magazine, 07 May to 11 May
Pirate Bay defends Virgin Media while founder Peter Sunde faces jail
It is with some irony that The Pirate Bay (TPB) came to the defense of Virgin Media (TalkTalk was also disrupted) after the ISP’s website was taken down by Anonymous.
11 May 2012
BeyondTrust acquires vulnerability management company eEye Digital Security
BeyondTrust, a company that provides privilege delegation and authorization systems with its PowerBroker suite of products, has acquired eEye Digital Security, developer of the Blink and Retina vulnerability management tools.
11 May 2012
Member and spokesperson for TeaMp0isoN arrested in Newcastle
A 17-year old has been arrested in Newcastle by the Police Central eCrime Unit (PCeU) and local Northumbrian Police officers for alleged offenses under the Computer Misuse Act.
11 May 2012
Winners and losers in European card fraud
FICO has produced an interactive map of Europe, showing the evolving European fraud landscape between 2006 and 2011.
10 May 2012
DigiNinja analyzes the Twitter hack, and offers password advice to web services
Yesterday we reported that 55,000 Twitter accounts have been leaked on Pastebin. Security researchers Anders Nilsson and Robin Wood have separately analyzed the dump.
10 May 2012
Queen’s Speech announces ‘measures… to access vital communications data’
As expected, the Queen’s Speech yesterday announced the intention of the UK Government to bring forward (during the current parliamentary session) measures to allow law enforcement and intelligence agencies access to ‘vital communications data’.
10 May 2012
Net neutrality becomes law in The Netherlands
The net neutrality provisions approved by the Dutch Parliament last June as part of its implementation of the European telecommunications package became law yesterday.
09 May 2012
False Facebook account leads to Principal’s resignation
Louise Losos, principal of Clayton High School, Missouri, has resigned following accusations that she created a false persona on Facebook and befriended hundreds of her own students.
09 May 2012
Twitter fights two information security battles
Twitter is in the unenviable position of being ‘attacked’ on all sides: while it tries to fight a subpoena demanding the account details of Occupy protestor Malcolm Harris, hackers release thousands of user logon details on Pastebin.
09 May 2012
Analysis shows social networks increasingly used to spread malware
In its latest monthly analysis of the most prevalent malware, GFI describes how social networks remain the most popular breeding ground for infections.
08 May 2012
“Good on ya’ Mozilla”, says Sophos about Firefox
Firefox is developing a new feature called ‘click-to-play’ designed to provide additional protection for web browsing – but not everyone thinks this is necessarily useful.
08 May 2012
Syrian activists targeted with RATs
There have been several recent examples of Syrian activists being tricked into downloading and installing remote access tools (RATs) that secretly hand control of their computers to a third party.
08 May 2012
PandaLabs malware report – and the balance between law enforcement and user
Almost one-in-four computers in the UK is infected – and the UK is one of the least infected countries in the world, says the new PandaLabs report released today.
07 May 2012