Archive
MS issues out-of-band patch as IE attacks increase
FireEye reported last week (26 Apr 2014) on a newly discovered Internet Explorer vulnerability that is already being exploited in the wild. The vulnerability affects all IE versions from 6 through 11; but was at the time only being exploited in version 9-11 in Win 7 and 8.
Two things have since happened. Firstly the attacks have widened. FireEye reported May 1 on
a newly uncovered version of the attack that specifically targets out-of-life Windows XP machines running IE 8. This means that live attacks exploiting CVE-2014-1776 are now occurring against users of IE 8 through 11 and Windows XP, 7 and 8.
“Operation Clandestine Fox” Now Attacking Windows XP Using Recently Discovered IE Vulnerability
To make this worse, FireEye also noted that multiple actors are now involved in these attacks:
…new threat actors are now using the exploit in attacks and have expanded the industries they are targeting. In addition to previously observed attacks against the Defense and Financial sectors, organization in the Government- and Energy-sector are now also facing attack.
The second new development is that Microsoft has reacted with remarkable speed, and has already released an out-of-band patch for the vulnerability. Users with automatic updates should not need to do anything – all others should make sure that they avail themselves of this update as soon as possible (details here). Interestingly, even though XP is no longer supported, an XP fix is included.

Jerome Segura, senior security researcher at Malwarebytes
(As an aside, I find this an interesting situation. Microsoft will be continuing to support XP for private customers – such as the UK government. It will therefore have the fixes. So, does Microsoft ignore the rest of the XP market even though it can keep it safe, and even though compromised unsupported XP systems could be used to attack the critical infrastructure? Jerome Segura, senior security researcher at Malwarebytes, thinks not. “Microsoft’s decision to patch XP through the automatic update channels may shoot itself in the foot by encouraging users to stick with it awhile longer,” he suggests. “Offering support for Windows XP should really be a last resort scenario because this is an aging operating system that does not meet today’s security and performance standards.”)
I have two questions on the latest developments: why do zero-day vulnerabilities spread to multiple actors so quickly; and is there an added threat from the vast numbers of unpatched, pirated and subsequently compromised XP computers. I asked FireEye’s threat intelligence manager, Darien Kindlund, for his views on these.

Darien Kindlund, threat intelligence manager at FireEye
His answer to the latter is relatively simple: we don’t know. “We know that the number of pirated copies of Windows XP is still quite large; however, we do not have updated statistics on legal vs. pirated copies,” he said.
Although pirated software can still get Microsoft’s security patches, it is quite likely that the pirates will avoid doing so for fear of being discovered. So even if Microsoft continues to release security patches for XP, good people who don’t patch and bad people who won’t patch will leave potentially millions of XP targets that could be turned to the dark side.
On the spread of 0-day attacks I wondered if the original bad actors sell on the vulnerability to other groups once the attacks have been discovered. The initial targets in this instance (defence and finance) could suggest organized crime if not state-affiliated attackers. Such targets could be expected to patch rapidly – so the value of the vulnerability would quickly lessen once its use is discovered and mitigation steps are put in place. Selling on to other actors would maximize the financial return from it when it becomes less effective.
Kindlund, however, offered a simpler explanation. “It is believed,” he said, “the original threat group using this vulnerability passed the exploit onto other groups, in order to make it harder for attribution analysis.”
But this all leaves one major problem for users. This vulnerability was in active use before it was discovered by the good guys. Then followed a period in which mitigation steps were available, but no formal patch. Now we are in the period in which sys admins will be trying to schedule in their updates, and wondering just how urgent it might be. The question is, however, how many users have already been unknowingly compromised?
Cisco has come up with some help. It has analysed an exploit and found a selection of attack indicators.
Due to active exploitation uncovered among our customer base, we are releasing the following indicators about the exploit so that anyone can investigate their own environments and protect themselves:
We’ve associated the following subjects with this campaign so far:
- Welcome to Projectmates!
- Refinance Report
- What’s ahead for Senior Care M&A
- UPDATED GALLERY for 2014 Calendar Submissions
Associated domains so far:
- profile.sweeneyphotos.com
- web.neonbilisim.com
- web.usamultimeters.com
- inform.bedircati.com
Sys admins should therefore look to their logs. If they find any of these indicators, they have been attacked and may already be compromised. Either way, the patch should be applied as early as is feasible.
My willy is bigger than yours
I got an email yesterday (29 April 2014). It said:
Today the Websense Security Labs found a new vulnerability in Microsoft Internet Explorer which affects Internet Explorer versions 6 through 11. However, current reported attacks are targeting Explorer 9 through 11. The Labs have issued a blog post which outlines solutions for those who have been affected by the attack.
Not another IE 0-day surely? Because FireEye found one just a couple of days ago. On Saturday (26 April 2014) FireEye blogged:
FireEye Research Labs identified a new Internet Explorer (IE) zero-day exploit used in targeted attacks. The vulnerability affects IE6 through IE11, but the attack is targeting IE9 through IE11. This zero-day bypasses both ASLR and DEP. Microsoft has assigned CVE-2014-1776 to the vulnerability and released security advisory to track this issue.
New Zero-Day Exploit targeting Internet Explorer Versions 9 through 11 Identified in Targeted Attacks
This is strange, because the 0-day ‘found’ by Websense two days later is also given the vulnerability assignation CVE-2014-1776:
A new vulnerability found in Microsoft Internet Explorer affects Internet Explorer versions 6 through 11. However, current reported attacks are targeting only Internet Explorer 9 through 11. The vulnerability allows attackers to remotely execute arbitrary code on the target machine by having the user visit a malicious website.
This vulnerability has been assigned reference CVE-2014-1776…
Microsoft Internet Explorer Zero-day – CVE-2014-1776
In fairness to Websense, its blog does not claim to have found the vulnerability itself – that is left to the email sent to journalists such as myself. But nor does it give any credit to FireEye – which would have been good. Just in case there is any doubt about who really did first discover this particular vulnerability (apart from the hackers of course), Microsoft’s advisory is quite explicit:
Microsoft is aware of limited, targeted attacks that attempt to exploit a vulnerability in Internet Explorer 6, Internet Explorer 7, Internet Explorer 8, Internet Explorer 9, Internet Explorer 10, and Internet Explorer 11…
Microsoft thanks the following for working with us to help protect customers:
- FireEye, Inc. for working with us on the Internet Explorer Memory Corruption Vulnerability (CVE-2014-1776)
OK. So having established that FireEye really does have the bigger willy, and implying that Websense is a wee bit envious in trying to pass off the discovery as its own… what is this vulnerability? Well, it’s a bad one. Bad enough, in fact, for the European security agency, ENISA, to issue its own advisory (something I am not aware of it having done before).
- This is a significant threat for IE users as there is no quick fix to repair, and “patch” this
- Users who want to avoid the abovementioned risk should temporarily use another browser until this security gap has been fixed
- Users should keep their systems patched and up-to-date
- Many users have two different browsers installed so they should easily be able to switch. If not, this is a good reason why they should have it; when needed.
ENISA
This is the best advice I’ve seen. While many experts are advising users not to surf in admin mode, to install EMET and to activate EPM, the majority of IE users will not even know what any of this means. Far simpler, and much more effective, would be to install multiple browsers (I’ve got five: Firefox, Chrome, IE, Safari and Opera); to keep them all fully patched; and to switch between them whenever a new 0-day is discovered for any one of them.
US magistrate makes Schengen internet more likely
Microsoft could either see the Schengen Cloud coming or was privy to politicians’ thoughts. In January this year it announced that it would allow European customers to keep their data on servers within Europe. This followed a blog by legal counsel Brad Smith in December 2013 that voiced concern over US surveillance:
And we’ll assert available jurisdictional objections to legal demands when governments seek this type of customer content that is stored in another country.
Protecting customer data from government snooping
So when news broke in February that Germany’s Merkel and France’s Hollande were keen on developing a European cloud to protect the privacy of European citizens, Microsoft was in a strong position to say, hey, we’re already with you: European data will remain within Europe; Microsoft can be part of the European cloud. (That proposed cloud is now known as the Schengen Cloud. Since the UK has never joined the Schengen group it is a way of excluding the UK — and specifically GCHQ — from Europe’s cloud.)

Alexander Hanff, Think Privacy Inc
But the reality is different. Privacy expert Alexander Hanff, CEO of Think Privacy Inc, said at the time: “Microsoft knows full well that it makes no difference whether the data is hosted in the US or not. They are a US corporation and therefore any data they hold is vulnerable to the US surveillance machine no matter where it is. It is clear from the announcement that Microsoft (as well as the rest of the cloud industry) is really concerned about losing revenues for cloud services and they know there is a strong movement within Europe (not least by the European Commission) to create infrastructure independent of the US and US tech giants.”
He called it right. Brad Smith had been true to his word and had challenged a US law enforcement demand for customer details held in Ireland. The unnamed LEA had demanded everything on the customer, including the content of emails, user’s contact lists, IP addresses and even bank details. Microsoft went to court. It argued that warrants could not be served overseas, and that the warrant should be negated.
On Friday, a US magistrate delivered his decision. He said that while the LEA demand was couched as a warrant, because it involved telecommunications it was to be enacted as a subpoena — and subpoenas can be enforced on overseas locations. Thus, as Hanff had predicted, it matters not where a US company stores its data, the PATRIOT Act can demand and enforce access to it.
In fairness, Microsoft seems to have expected this. It will appeal. Microsoft’s deputy general counsel David Howard blogged on Friday,
When we filed this challenge we knew the path would need to start with a magistrate judge, and that we’d eventually have the opportunity to bring the issue to a U.S. district court judge and probably to a federal court of appeals. Today the Magistrate Judge, who originally issued the warrant in question, disagreed with our view and rejected our challenge. This is the first step toward getting this issue in front of courts that have the authority to correct the government’s longstanding views on the application of search warrants to content stored digitally outside the United States.
One step on the path to challenging search warrant jurisdiction
The stakes are high. If the US courts ultimately uphold law enforcement’s right to demand the data of European citizens held on European premises for all US companies, and if Europe proceeds with the Schengen Cloud, then Microsoft, Google, Facebook, Twitter and other US tech giants will simply be excluded from Europe. This will hurt the US economy. Firstly these companies will be excluded from one of the world’s most important markets, and secondly it will be a huge boost to the indigenous European tech industry — which will hurt the US economy even more.
Microsoft support scammer sent down — first ever successful prosecution in the UK
We’ve all had those phone calls — some of us have had many of them — from Microsoft certified support engineers offering to fix our PCs over the phone. They can be very compelling.
“Your PC is running slow. I can fix it for you over the phone.”
“How much?”
“No fee. You can just pay me what you think it’s worth — maybe £30 — when it’s done. If I don’t improve things, you don’t need to pay anything.”
It’s a good bet. Who hasn’t got a PC that is running slower than it did when we bought it?
What happens next might vary. The scammer will talk you through a few things to gain your confidence. Then he will come a cross a problem too difficult to handle through conversation — but having gained your confidence, where is the problem in letting him fix it for you remotely? All you have to do is install this bit of software, which he’ll talk you through, and he’ll be able to fix it immediately — and even provide a very cheap anti-virus program to improve your security.
Suddenly, that £30 has become £80. He’s fixed nothing and sold you free software — and possibly left something nasty on your computer. Well, the e-crime team from Trading Standards has now successfully prosecuted one of these scammers: Mr Mohammed Khalid Jamil, was sentenced to 4 months imprisonment, suspended for 12 months, and fined £5000. Jamil was also ordered to pay £5665 in compensation to his victims and £13929 in prosecution costs.
Lord Toby Harris, chairman of the National Trading Standards Board, commented, “This is a landmark case, as we believe it may be the first ever successful prosecution of someone involved in the Microsoft scam in the UK. It’s an important turning point for UK consumers who have been plagued by this scam, or variants of it, for several years. Many have succumbed to it, parting with significant sums of money, their computers have been compromised and their personal details have been put at risk. Now that one of the many individuals who’ve been operating this scam has been brought to justice, it’s a stark warning to anyone else still doing it, that they can be caught and will be prosecuted.”
Don’t let the government or the tech giants fool you into thinking anything is changing
When Bruce Schneier left the employ of BT, he finally got off the pot. His natural inclinations can now be seen. He still hasn’t criticised BT despite it being obvious that BT is no more innocent than any of the big American telecoms companies — but he told me (by email) at the time that he tried to avoid getting involved in foreign politics.

Bruce Schneier — the ex-BT, anti-surveillance privacy guru
He hasn’t been 100% consistent in this. When Swedish journalists discovered Swedish involvement in the MITM NSA/GCHQ hacking program known as Quantum, he said, “Both Quantum and FoxAcid are NSA/GCHQ programs to attack computer users. The fact that Sweden is involved in these programs means that Sweden is involved in active attacks against internet users. It is not just passive monitoring. This is an active attack.”
One day we may yet hear what he knows about BT’s cooperation with GCHQ (Tempora et al).
In the meantime, he is now no longer backward in commenting on surveillance in general and the NSA in particular. An article in The Atlantic last week warns us not to listen uncritically to the protestations of either the NSA or the tech giants that now appear to be up in arms against this NSA hacking and surveillance.
The tech giants (Google, Facebook, Yahoo, Microsoft etcetera) all claim to be doing what they can to prevent further snooping. But they are not doing the one thing that would work — they are not encrypting user data on servers in a way that would be impossible for governments to demand the keys. And the reason they are not doing this is simply because the vendors and the governments both want the same thing — to be able to read our data.
The best we have are caveat-laden pseudo-assurances. At SXSW earlier this month, CEO Eric Schmidt tried to reassure the audience by saying that he was “pretty sure that information within Google is now safe from any government’s prying eyes.” A more accurate statement might be, “Your data is safe from governments, except for the ways we don’t know about and the ways we cannot tell you about. And, of course, we still have complete access to it all, and can sell it at will to whomever we want.”
Don’t Listen to Google and Facebook: The Public-Private Surveillance Partnership Is Still Going Strong
The reality is that for so long as the vendors want access to our data, the governments will be able to demand it. Neither of that is changing; although both sides are trying to pretend it is.
Microsoft’s new secret weapon: listening to its customers
I am not Microsoft’s greatest fan. It is a dinosaur stuck on the beach while the fleeter of foot are soaring through the clouds. The reality is that it has no, and has never had, any visionaries. Even its domination of the desktop was more down to luck and sharp practices than genuine vision.
It was lucky that Gary Kildall rejected IBM’s overtures, else there would never have been an MS-DOS; and it was sharp practices that killed off Digital Research — its one serious and technically superior competitor. It was lucky that Apple demonstrated the value of Xerox Parc research and paved the way for Windows. It was lucky Jobs was so far ahead of his time he thought he could have a walled garden in the ’80s; and almost destroyed Apple in the process.
But it was sheer arrogant blindness that made Gates think he could ignore the internet. For the last two decades Microsoft has been forced into playing catch up; but catch up never works if you don’t have the vision to get ahead of the competition.
Now, in just one area, Microsoft is showing visionary signs that could differentiate it from all of its competitors. Microsoft has started listening to its customers rather than imposing its will on its customers.
While Facebook is telling everyone that they don’t want privacy, Microsoft is listening and saying, OK, we will give you privacy. While Google is fighting the European Union over privacy and cloud storage, Microsoft is listening to the EU and saying, OK, we can accommodate and store European data in European data centres.
Now, it’s not as simple as that. The US government can still demand customer data from Microsoft’s European data centres simply because Microsoft is a US company. But it’s making that data much more defensible, and telling the EU that it is willing to cooperate rather than fight.
Similar over privacy. When it became clear last week that Microsoft had, quite legally, searched the emails of one of its customers concerning the theft of Microsoft IP, it knew there would be privacy issues. It immediately said two things: firstly that it would in future get a pseudo warrant from an independent lawyer who had previously been a judge, and secondly that it would include its own searches in future ‘transparency reports’ (the ones that publish the number of law enforcement searches).
It wasn’t enough for the privacy advocates who pointed to the hypocrisy of criticising NSA warrantless surveillance and then doing its own.
To Microsoft’s great credit, within a week, it has listened, heard and understood. Brad Smith announced yesterday,
Effective immediately, if we receive information indicating that someone is using our services to traffic in stolen intellectual or physical property from Microsoft, we will not inspect a customer’s private content ourselves. Instead, we will refer the matter to law enforcement if further action is required.
We’re listening: Additional steps to protect your privacy
Is this a new Microsoft — the genuinely ‘listening’ company? It no longer dominates the world’s operating systems, and is losing ground on desktop office software. But it seems to be doing one thing that none of its competitors are doing. It is listening to its customers, and giving them what they want. That alone, over the next few years, could catapult Microsoft back into a leading position.
What ties Microsoft, surveillance, Syria and the Syrian Electronic Army together?
The Syrian Electronic Army (SEA) yesterday hacked Skype’s WordPress and Twitter accounts. The likelihood is that the pro-Syrian group got hold of the password used by Skype’s media people, probably through its usual method of spear-phishing. My report on the incident for Infosecurity Magazine is here.
But this hack was a little different to SEA’s normal escapades. The group’s whole raison d’être is to deliver pro-Assad messages to counter what it believes is anti-Assad propaganda controlled and delivered by western governments. This is the reason that it has concentrated on attacking high-profile media companies.
Well, Skype is certainly high-profile — but the message is not ‘Syrian’. On both the Skype Twitter account and its WordPress blog the SEA message was this:

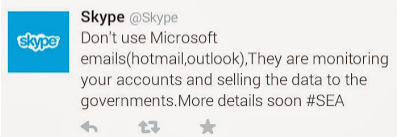
SEA’s message via Skype’s Twitter account

It’s a message you might more likely expect from Anonymous protesting against NSA surveillance and Microsoft complicity in that surveillance rather than a pro-Assad movement.
I asked SEA if it marked a change in its targets and tactics; and got this reply:
We can confirm that attack was done by us. and we gained access to important documents about monitoring accounts/emails by Microsoft.
It’s still about Syria. And we will detail that soon.
So that’s the big question now: what ties Microsoft, surveillance and Syria together?
Is Windows 8 an NSA trojan?
That really does sound a bit extreme even for a cynic – but it’s a question that is being seriously asked and needs a serious answer. It came to a head earlier this week when Zeit Online published a story suggesting that various federal German agencies had come to the conclusion that Windows 8 is not safe for use by government.
We need to put this into context with two technologies: UEFI and TPM. The Unified Extensible Firmware Interface (UEFI) is a specification that is meant to replace the Basic Input/Output System (BIOS) firmware interface on PCs. It provides many advantages over the original BIOS, but more pertinently here, it can be used to provide ‘secure boot’. Microsoft has come in for some serious criticism over implementing UEFI secure boot on Windows 8 – sufficient criticism for a Spanish open source group, Hispalinux, to level a complaint against Microsoft with the European Union for anti-competitive behaviour. Much of that criticism has died down as it has become clear that serious power users can get round it. However, implemented to its full potential it could enforce an Apple-like walled garden around non-Microsoft manufactured PCs.
TPM – trusted platform module – is a separate issue. This is a chip that controls what can and what cannot run on your computer. It can indeed provide additional security, since if only known good software is allowed to run, then any bad software (viruses and trojans and worms and so on) cannot easily run (never say never!). And there isn’t really an issue, since if you don’t want it, you can just turn it off.
Enter TPM version 2; which is what has upset the German government agencies. Microsoft intends to employ it with Windows 8. Windows 8 will be delivered with TPM 2.0 turned on, and no way to turn it off. But for new versions of Office or completely new Microsoft software, Microsoft clearly needs to be able to bypass TPM – and it has its own key to do so. The user does not have a key to do so.
And this is where the NSA comes in. Given everything we have learned about the NSA over the last few months, does anyone really believe that Microsoft will not willingly or at best under secret coercion be forced to give those same keys to the NSA and probably the FBI as well?
Some of us may even remember the NSAKey discovered in Windows NT by Andrew Fernandes in 1999. At the time, Microsoft denied the key had anything to do with the NSA, but frankly only the gullible believed them, and most people accept that it has been present in every version of Windows ever since. Anybody who believes that Microsoft and the NSA don’t go hand in hand is living in cloud cuckoo land under heavy surveillance.
The problem is that with access to a TPM 2 key that is always on, the NSA or the FBI or both could come and go at will with no-one being any the wiser. Which is exactly how they like to operate.
So how likely is all this? Professor Ross Anderson from Cambridge University wrote back in October 2011,
We’ve also been starting to think about the issues of law enforcement access that arose during the crypto wars and that came to light again with CAs. These issues are even more wicked with trusted boot. If the Turkish government compelled Microsoft to include the Tubitak key in Windows so their intelligence services could do man-in-the-middle attacks on Kurdish MPs’ gmail, then I expect they’ll also tell Microsoft to issue them a UEFI key to authenticate their keylogger malware.
And if the Turkish government can do that, what could the US government do?
I asked him what he thought now, and whether Windows 8 really is dangerous for governments. He said,
Non-US governments had better think carefully about their policy on all this. Until now you could grab the Linux source, go through it, tweak it till you were happy, recompile it and issue it to officials in your ministry of defence. Serious players like China even sent engineers to Redmond to inspect the copy of Windows that would be sold in their country. But most states don’t have enough competent engineers to do that.
Microsoft’s demand that the industry configure all Windows-branded machines so they’ll only boot signed operating systems will make life significantly harder for medium-sized non-aligned governments. And now that Microsoft’s admitted making NSA access easier, the idea of using COTS Windows is not emotionally compatible with the existence of large pampered signals intelligence bureaucracies, even if there isn’t a reasonable engineering alternative.
And so we return to the original question: is Windows 8 an NSA trojan? Yes. Microsoft and the NSA and the Obama administration will, of course, deny it. And the NSA — post Snowden — may never even use it. But that doesn’t alter the fact that the capability exists and could be used. A nuclear weapon is no less a nuclear weapon just because it hasn’t been used. And Windows 8 is an NSA trojan.
Microsoft Surface RT – an unmitigated disaster
Nobody likes to admit to any enjoyment in “I told you so.” It is therefore with huge regret and personal pain that I now say, “I told you so.”
On August 7, 2012 – just over a year ago, this blog said: A Microsoft-made tablet? Big mistake. More specifically I added
But Microsoft’s solution is just plain wrong. It is planning to build its own tablet, to compete with the iPad and Android.
This would be a mistake…
Almost exactly one year later, on August 12, 2013, ‘Gail Fialkov, individually and on behalf of all others similarly situated’ filed suit against ‘Microsoft Corporation, Steven A Ballmer, Peter S Klein, Frank H Brod and Tami Reller’ in the US District Court, Massachusetts. The suit claims
What Defendants knew, but failed to disclose to investors, however, was that Microsoft’s foray into the tablet market was an unmitigated disaster, which left it with a large accumulation of excess, over-valued Surface RT inventory.
Despite costly attempts to spur the Surface market (such as a free $100 dollar magnetic cover/keyboard and a 30% discount on the price), ‘nothing generated meaningful sales of Surface RT.’
Then, on July 18, 2013, Microsoft issued a press release announcing that its financial results for the quarter ended June 30, 2013 had been adversely impacted by a $900 million charge related to a write-down in the value of its Surface RT inventory. In truth, however, the value of such inventory was materially impaired by March 31, 2013.
On this news, Microsoft common stock suffered its biggest price decline in more than four years, plunging $4.04 per share, or 11.4%, on very heavy trading volume to close at $31.40 per share. The magnitude of the decline in the price of Microsoft’s stock eviscerated about $34 billion of the company’s market value.
The action is claiming that anyone who purchased Microsoft stock between April 18 2013 (that is, just after the date at which it claims Microsoft was aware of the excess stock) and 18 July 2013 (that is, the date of its announcement of excess stock) suffered a material and unnecessary hit on their investment.
Whether Microsoft will issue a defence based on the public availability of this blog that had earlier warned all and sundry that the Surface was a big mistake and that they therefore had prior knowledge of the inevitability of the unmitigated disaster remains to be seen. But it could be, “Well, he told you so.”