Archive
Targeted advertising? Bollocks
I have come to the conclusion that all of this targeted advertising is a load of bollocks, and Google’s ability to grab, store and analyse my personal habits is worthless.
Android has just recommended a Coldplay album, which it says is ‘popular with similar listeners’.
- I had to use Wikipedia to find out what Coldplay is
- I have never knowingly listened to Coldplay; and don’t intend to
- I have never listened to any music via Android (apart from a few accidental YouTubes where I have never succeeded in listening to completion).
OK, so they got that wrong.
But maybe it’s other people who are similar to me who like Coldplay… No, that’s no good either, because that means that I’m like people who like Coldplay — and that, frankly (no disrespect) is insulting.
So this ‘targeting’ is way off beam. Which means it’s simple old-fashioned promotional advertising. I just hope for Coldplay’s sake they aren’t paying over the odds for targeting that doesn’t exist.
Happy Christmas from GCHQ and the Orcs
What do you make of GCHQ’s internal Christmas card, obtained by the excellent Hawktalk privacy blog? Note that although not ‘protectively marked’, it is exempt from the Freedom of Information Act – meaning that if you asked for a copy, you wouldn’t get one.


Happy Christmas from the Orcs

The cartoon reflects the growing public perception of GCHQ and NSA. But is it used in defiance or irony? What sort of mindset considers it to be an acceptable Christmas message?
And what should we read into the poem? It goes:
The Terror Bytes of Power
Two terabytes per day to retain all Google searches
Five keeps the content from surveillance perches
Seven for Skype when one speaks to mates
Twelve stores the traffic which flows to the States
And in the darkness where the watchers are
Few laws to obey; nor rules that bar
And for privacy let the protection die
In a secret state where the shadows lie.
Or is it all just an elaborate hoax – either originating from a small cell within GCHQ or somebody on the outside?
Is it just coincidence that the creator of the cartoon is the same cartoonist who does all of Hawktalk’s cartoons: Chris Slane – and it seems consistent with his views? Here’s another lifted from Hawktalk:

British MP caught telling lies about Glenn Greenwald
Two things of note happened yesterday. In the US the White House released the independent report into the NSA global surveillance programs (I’ve done a quick summary on Infosecurity Magazine here: White House Releases the NSA Surveillance Review). Meanwhile, journalist Glenn Greenwald spoke to the European Union via video link.
The NSA review includes this little gem: “A particular concern involves preservation of the rights, and the security, of journalists and the press; their rights and their security are indispensible to self-government.”
I only hope that the UK government reads this report and ponders on that statement. No free press, no democracy.
But the reality is that if Greenwald had flown to Brussels to speak to the EU he would probably have been arrested. The UK could, probably would, have issued a European arrest warrant under the Terrorism Act; and the Belgian police would have been forced to arrest him – just as the UK was ‘forced’ to arrest Assange on an arrest warrant issued by Sweden. Such behaviour would have been par for the course from a government that is determined to curtail rather than protect the freedom of the press.
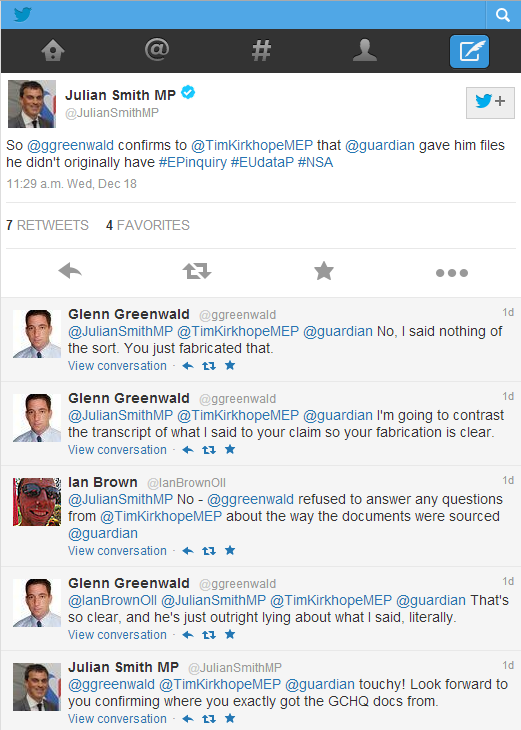
But unable to arrest him, they could only watch and fume impotently; and an impotent politician is a wondrous sight. British MP Julian Smith – the very MP who has been leading the charge against the Guardian and is trying to get it and its editor charged under the Terrorism Act – tweeted: “So @ggreenwald confirms to @TimKirkhopeMEP that @guardian gave him files he didn’t originally have #EPinquiry #EUdataP #NSA.” There was just one problem: Greenwald said nothing of the sort.


If it wasn’t so funny, it would be worrying. Here we have a member of the British Parliament so determined to kill the messenger that he quite openly and quite blatantly lies to get his way.
Compare and contrast the two nations: the US and the UK. The US houses the Big Brother of spy agencies (the NSA) which is the major culprit in global surveillance, spying and hacking. In response to public outcry it holds an independent enquiry and publishes the result. The UK houses the little subservient brother, GCHQ, which on a slightly smaller scale is just as bad. In response to public outcry it denies any wrongdoing, disrupts any attempts at public debate, and seeks to prosecute the Guardian. And its politicians – or this one at least – tells a stupid, indefensible lie that not merely holds himself up to ridicule, but makes you wonder about the cumulative IQ and morality of our leaders.
Spookerism (noun): a manipulated meaning that allows you to fib without lying
Spookerisms were made popular by the Spook Brothers Clapper and Alexander, a famous 21st century Music Hall Double Act. Spookerisms are a major tool in the disinformation and misinformation armoury of the modern intelligence agent: a method of providing misleading information without telling an untruth.
The thing is, the NSA doesn’t tell lies — at least not within the spookerist frame of reference. So when it says that it was aware of a BIOS-attacking virus, and allows us to believe it comes from China, and that it worked with manufacturers to nullify the threat; and that without intervention this virus had the potential to take out the US economy, it isn’t lying: it is indulging in a spookerism.
This is a transcript from the latest CBS 60 Minutes programme. John Miller is the CBS interviewer (an ex-NSA man). Debora Plunkett is the NSA Information Assurance Director
[voice over]: One they did see coming was called the BIOS Plot. It could have been catastrophic for the United States. While the NSA would not name the country behind it, cyber security experts briefed on the operation told us it was China. Debora Plunkett directs cyber defense for the NSA and for the first time, discusses the agency’s role in discovering the plot.
Debora Plunkett: One of our analysts actually saw that the nation state had the intention to develop and to deliver, to actually use this capability — to destroy computers.
John Miller: To destroy computers.
Debora Plunkett: To destroy computers… The attack would have been disguised as a request for a software update. If the user agreed, the virus would’ve infected the computer.
John Miller: So, this basically would have gone into the system that starts up the computer, runs the systems, tells it what to do.
Debora Plunkett: That’s right.
John Miller: — and basically turned it into a cinderblock.
Debora Plunkett: A brick.
John Miller: And after that, there wouldn’t be much you could do with that computer.
Debora Plunkett: That’s right. Think about the impact of that across the entire globe. It could literally take down the U.S. economy…
[voice over]: The NSA working with computer manufacturers was able to close this vulnerability, but they say there are other attacks occurring daily.
Given this information, the natural takeaway for most people is that China is or was intent on taking down the US economy with cyberweapons, and but for the astuteness of the NSA probably would have succeeded.
Spookerism!
The NSA says nothing like that, but manipulates us into believing it. In fact, it says very little, and relies on us filling in the gaps for ourselves.
There have been many BIOS-attacking viruses. Consider Chernobyl (CIH). It was around in 1998. It was developed in Taiwan — which is a nation-state that likes to call itself China. After it was discovered, computer manufacturers worked on their systems to reduce the threat (and I’m willing to accept, or even bet, that the NSA had at least some tiny involvement in that). Unchecked; that is given free rein, it certainly did have the capability and potential to take down the world’s economy. Thing is, viruses do tend to get checked — there’s an entire security industry dedicated to it.
But when you stop and think about it, this new BIOS Plot described by the NSA to CBS — ably assisted by an ex-NSA journalist — could easily be a rather shaky but not false description of the Chernobyl virus.
And that’s what we call a spookerism.
ResearchGruppen, the Disqus ruckus and the moral issues involved
Martin Fredriksson of ResearchGruppen, the Swedish investigative journalists behind the Disqus ruckus, made an interesting statement late last night: “We’re not very concerned about a criminal case in the US. It would give this issue the attention it deserves.” He was commenting on my post about the security/legal issues around ResearchGruppen’s Disqus expose, which was I believe more politically/morally motivated.
That latter is by far the more important issue, for security can be relatively easily cured while morality cannot. And the implication from Martin’s statement is that it is one he is willing to face prison over. Just ask Julian Assange to what ends the Swedish/US political/intelligence alliance will go to get their man. Add to that Martin’s further comment, “I just heard that Disqus had changed stance. From ‘there has been no breach’ to ‘we have contacted law enforcement’.”
The moral issue raised by ResearchGruppen is this: how do you balance freedom of speech (and the right to anonymity that supports it) with the protection of minorities (and the limitations to freedom of speech it requires) and a right to know what our political and judicial and police masters actually believe?
The rule of law
The easy, and erroneous, answer is to use the rule of law. This is a concept that is pushed by governing authorities to emasculate their people. It states simply that you must always and absolutely obey the law of the land. The opposite is true. People have a duty to obey their conscience above their national laws. And if that means defying or breaking the law, so be it.
A right to freedom of expression.
This should be a statement of fact, but it rarely exists in reality. It is often considered to be a primary distinction between democracy and authoritarianism. Western governments, ostensibly democratic, use ‘national security’ to severely curtail that right – to such an extent that we need to ask ourselves whether they are genuinely democratic countries. It is also, and in my opinion quite rightly, curbed in order to protect minorities. But the difference between jokes, satire, political licence and hate speech becomes very confused.
If I was to say that 90% of the UK Cabinet are dangerous, lying bastards who should be burned at the stake, I would probably get away with just a wry smile. But if I was to say that 90% of blacks/Jews/immigrants/Moslems/unmarried mothers (take your pick) are dangerous, lying bastards who should be burned at the stake, then I would get a very different reaction.
A right to anonymity on the Internet
This should be a given. Without it, freedom of expression could be bullied out of existence by political, criminal and just plain thuggish elements. The problem is that those same political, criminal and just plain thuggish elements use that same anonymity to peddle their own particular brand of hate speech. So while freedom fighters and libertarians demand and need it, governments, law enforcement and intelligence agencies seek to remove it.
The conflict comes when anonymity is used to hide the identity, and therefore give free rein, to hate speech aimed at minorities who can little defend themselves. Minorities deserve protection in a free country, and anonymity weakens that protection.
The right to know what society’s shapers really believe
There is a second category wherein the right to anonymity should perhaps be curtailed: one we could define as ‘society’s shapers’. This would include politicians (who make our laws), the judiciary (who interpret those laws), the police (who enforce the laws), and the influencers (who manipulate the making of our laws, such as leading economists, top bankers, captains of industry and lobbyists). When we the people accept or reject the laws imposed upon us, we have a right to know the real motivations of those involved in the making of those laws. This can be and sometimes is hidden behind the cloak of anonymity.
I believe it is this last aspect of anonymity that concerns ResearchGruppen; and it is one with which I can sympathise. But it still carries enormous moral problems. In order to expose the secret thoughts of a few of Sweden’s shapers, the group has compromised the anonymity of millions who deserve that anonymity. I think the group is aware of this. “We focused on swedish hate sites,” commented Martin Fredriksson. As for the rest of the 19 million-strong database, “I still don’t know what to do with it. Delete it or see what politicians, economists and lobbyists are really concerned about, when they think they’re anonymous.”
But there are two further issues that we need to consider. Firstly, if Disqus was a European country, it would almost certainly be prosecuted, as the data controller, for breach of the Data Protection Directive. In the UK, Sony was fined £250,000 because it was breached by LulzSec. Disqus, I suspect, would receive similar treatment for being breached by ResearchGruppen.
Secondly, if journalists can find such a gaping hole in Disqus’ logic, then you can guarantee that the NSA, GCHQ and FRA were already aware of it. And who else? Hate sites and user comments would be a perfect recruitment centre for both spies and jihadists. When all is said and done, and irrespective of either legal or moral issues, ResearchGruppen has done the world a favour by forcing Disqus to close this hole.
You might also be interested in a new article: Disqus breach + IRS theft = fraudulently obtained credit reports and political coercion in Sweden
What lessons should we learn from the Disqus security breach?
I did a news story this morning on Infosecurity Magazine: Disqus May Not Have Been Hacked; But It Was Certainly Exploited. As often happens, however, the implications and side issues are often as interesting as the raw news.
Background
A bunch of Swedish journalists belonging to ResearchGruppen (a group of politically motivated investigative journalists) working with the Swedish tabloid Expressen has downloaded something like 29 million comments from the Disqus service. In doing so, it also obtained the email addresses of otherwise anonymous commenters.
“You don’t need to trade in your identity for the ability to speak up. The freedom to express how you want is what lets you be truly authentic,” says the Disqus website. Anonymity is a key selling point – but here it was letting ResearchGruppen (and who knows who else) download the email addresses of its users. Those addresses were hashed with MD5; but with no mention of salting this is barely a delaying tactic.
Whatever way you look at it, this was a serious breach of security. It allowed politically motivated researchers to discover the real identity behind some rather inflammatory ‘anonymous’ posts.
The issue
But it wasn’t a hack – at least not in the traditional sense. ResearchGruppen did not have to break in and steal the email addresses. The group simply queried the Disqus API and obtained the details. To save time, they used a script to automate their enquiries, running ten enquiries simultaneously. (You have to wonder why the Disqus sys admins didn’t pick up on these queries – to obtain 29 million at 100 per throw would have required 290,000 API calls.)
The real issue in this episode is whether ResearchGruppen’s actions were illegal, and whether they should or should not have been illegal. Probing computers is, after all, the standard method used by security researchers to find flaws and improve internet security for everyone.
US Computer Fraud and Abuse Act
There can be little doubt that ResearchGruppen has broken the US Computer Fraud and Abuse Act (CFAA). Just ask ‘weev’. In 2010 he queried the AT&T system in a similar manner and obtained the email addresses of early iPad adopters. He was prosecuted under the Computer Fraud and Abuse Act, and sent to prison for his pains.
Disqus is a US company with offices in San Francisco and New York. The US is not backward in demanding the extradition of foreigners who have broken their laws even if they have never set foot in America. Frankly, if I was a member of ResearchGruppen – especially given the close relationship between Sweden and the US – I’d be lawyering up or disappearing as fast as possible.
But, and it’s potentially a big but, US lawmakers and public are concerned that the Computer Fraud and Abuse Act allows law enforcement overreach. Ever since its use was implicated in the suicide of internet activist Aaron Swartz, it has been under scrutiny; and there are attempts to rein in its excesses.
In Europe
However, while the US is thinking about softening the CFAA, European lawmakers have been busy creating Europe’s own somewhat draconian CFAA look-alike. Early July this year the European Parliament approved the draft ‘attacks against information systems’ Directive, with 541 votes in favour, 91 against, and 9 abstentions. This is what Green MEP Jan Philipp Albrecht said about it:
Significantly, the legislation fails to recognise the important role played by ‘white hat hackers’ in identifying weaknesses in the internet’s immune system, with a view to strengthening security. This will result in cases against these individuals, who pose no real security threat and play an important role in strengthening the internet, whilst failing to properly deal with real cyber criminals. The result will leave hardware and software manufacturers wholly responsible for product defects and security threats, with no incentive to invest in safer systems.
“MEPs had initially supported a number of Green proposals aimed at ensuring this legislation can contribute to internet security, and is not simply an ineffective law to punish unauthorised log-ons to open servers. However, most positive elements were frittered away in the legislative negotiations, due to the resistance of EU governments. The result is a heavy-handed and misdirected law that will do little to improve internet security.
So, while the European Parliament initially wanted to recognise and defend the role of security researchers, national European governments do not. They now have until July 2015 to transpose the Directive into national laws – after which time, security ‘research’ of the sort undertaken by ResearchGruppen will be clearly illegal throughout the European Union, just as it is in the US.
Implications for the future of independent security research
I personally would not call the members of ResearchGruppen either white hat hackers or security researchers. I believe they were politically motivated and intent on embarrassing the far-right. However, it would be ridiculous to have rules saying you can only do this if your motives are acceptable – and it looks like Europe is coming down on the same side as America: you can’t do it, period.
This will have a sad effect on security research. Consider the current rash of cross-site scripting vulnerabilities. Many are found and reported by researchers, and quickly fixed by websites. Many others are found and exploited by hackers before they can be fixed by the websites. In the future, the researchers may become reluctant to put themselves at risk of imprisonment – leaving the only people looking for, and finding, these flaws will be the criminals wishing to exploit them.
ResearchGruppen may not have done what it did for the purest of motives, but nevertheless it has found a flaw that will be rectified by Disqus. The result is a more secure internet. In the future we may find that the ResearchGruppens and more genuinely white hat hackers will fade away. The internet will become a darker and more dangerous place because of it.
see also: ResearchGruppen, the Disqus ruckus and the moral issues involved; which discusses Martin Fredriksson’s response to this post.
You might also be interested in a new article: Disqus breach + IRS theft = fraudulently obtained credit reports and political coercion in Sweden
To hash or to encrypt — that is the question
Can somebody explain this to me, please? I don’t understand.
In LinkedIn’s data breach, customer passwords were stolen because they had been hashed instead of encrypted.
It’s from the Vormetric blog under the title Breach Blog Roll posted today. My understanding is that it refers to the 2012 LinkedIn breach that resulted in the theft of more than 6 million user passwords. Again, my understanding is that the passwords were hashed but not salted.
What I don’t understand, however, is how being hashed rather than encrypted was the cause of their theft.
Help? Anyone?
UPDATE
For the record, the best response I’ve had so far came via Twitter:
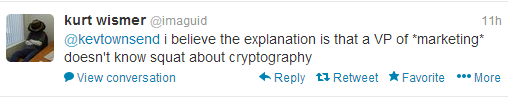
Kurt Wismer operates the excellent ‘anti-virus rants’ blog
‘anti-virus rants’ is here.
Britain continues to hide GCHQ lawlessness
The evidence that GCHQ is engaged in illegal activity is inescapable.
Snowden called GCHQ worse than the US. It was almost certainly GCHQ rather than the NSA that hacked the Belgian telecoms company BelgaCom. And we know that GCHQ has tapped more than 200 backbone fibre cables.
Today we learn of a new document that shows that GCHQ and the Swedish agency FRA, worked together to hack unknown, but probably Russian targets in conjunction with the NSA’s Quantum injection program (the document says, “Thank Sweden for its continued work on the Russian target, and underscore the primary role that FRA plays as a leading partner to work the Russian target, including Russian leadership, energy,… and… and counterintelligence”). In relation to GCHQ and Quantum, this document says, “Last month, we received a message from our Swedish partner that GCI-IQ received FRA QUANTUM tips that led to 100 shots, five of which were successfully redirected to the GCHQ server.”
So GCHQ breaks British and European laws. There can be no doubt.
So what does Cameron do? Does his government call for an investigation? Does it demand that its intelligence agency curb its activities? Does it hellaslike.
- It declares GCHQ activity legal.
- It arrests, detains and confiscates the computer of the boyfriend of a journalist as he stops over at Heathrow on the way from Germany to Brazil.
- It demands and oversees the physical destruction of a newspaper’s computers.
- It refuses to allow the EU to put spying on the table in discussions with the US.
- It threatens the editor of a newspaper with prosecution under the Terrorist Act.
And now one more act that no longer surprises. German MEP and Green politician Jan Philipp Albrecht issued the following statement today about a possible video hearing with Richard [oops! corrected, 13/12/2013] Edward Snowden:
The political groups – except the ECR group of British Tories… agreed on a possible hearing with Edward Snowden via video recording. They paved the way for answers of Edward Snowden to the European Parliament… For the Members of the European Parliament, his answers would be an important step up to substantial fact-finding and to draw consequences from mass surveillance.
True to form, Britain does not want anyone, including its own people, to know what GCHQ does, and which laws it breaks, in their name.
Dear Mr Cameron, you have turned the United Kingdom into a fascist state. I hope you are proud of yourself. I am ashamed of you.
Who’s doing what to protect our data?
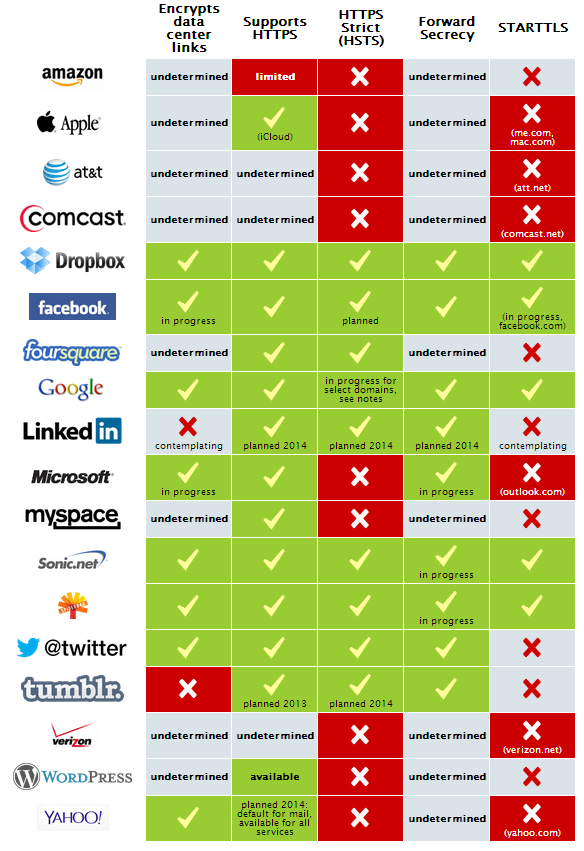
The Electronic Frontier Foundation has a fascinating graphic on which companies are doing what things to protect their customers’ – our – data in the post Prism/Snowden era.


What really leaps out is that the companies is that provide consumer cloud services are on our side (Dropbox, Facebook, Google and Twitter); telecommunication companies are on their side (AT&T, Comcast, Verizon); and the main OS providers (Microsoft and Apple) aren’t really sure which side their bread is buttered.