Archive
If you’re British, and you think you live in a democracy, I need to disabuse you
Consider the Communications Bill. That’s the bill that will supposedly allow the intelligence agencies to catch serious criminals and terrorists. But the only people it won’t catch are serious criminals and terrorists. And the only thing it will do is allow the government to know who you are talking to and where you go on the internet at all times and as you do it – at a huge cost to the public purse. (Incidental #1: The public purse is not government money. It is your money. The government doesn’t have any money. It is therefore taking your money to pay for a system to spy on you.)
Obnoxious as this is, it is not in itself undemocratic. You can argue that in a democracy, the electorate votes for a government and gives it the authority to make decisions without further reference to the electorate. (Incidental #2. I believe that this is a mis-interpretation of democracy developed and promoted by governments. I believe that in a democracy, the government is always subservient to the will of the people.)
But what is quite incredible is the experience of Conservative MP Dominic Raab. As a member of parliament he is being asked by the government to vote in favour of this bill. A fundamental part of the spying process will be the filter. ISPs are going to be asked to keep complete records of our communications and browsing. That will be a national database of everything, albeit spread across the different ISPs. Technically, not a problem – it’s a national database from a government that promised to ‘roll back the database state.’ The filter is the mechanism by which the agencies can get to what they want – that is, it is effectively a private government search engine for our emails.
Quite reasonably, Raab wanted to know more about what he was being asked – no, told – to vote for on our behalf. All he wants to know is the advice given to the Home Office to justify the filter. The Home Office said no. So with true Yorkshire grit (he can kiss goodbye to any government preferment in the future) he issued a freedom of information request. But again the Home Office said “no, national security issues, don’t you know old boy.”
So he referred it to the Information Commissioner. The Information Commissioner has requested more information from the Home Office so that he can make a ruling on whether the refusal of the FoI request is justified. The Home Office has just over 20 working days from now to respond or face potential legal action for what amounts to contempt.
My bet is that the Home Office will respond, but we won’t know how, because the Information Commissioner will agree that it is in national security interests to withhold the information. His only alternative is to side with the people, upset the government and kiss goodbye to his knighthood – just like Raab. I will be delighted and will beg his forgiveness for besmirching his noble position if he sides with the people. I doubt that I will have to.
But step back and think about this. The Home Office is demanding that our elected representatives simply do what they’re told with no understanding nor knowledge of what exactly they’re doing. That, I fear, is democracy in 21st Century Britain: we elect people to do what the government wants which is what big business and secret services want. What the electorate wants is irrelevant.
Somebody is lying. Is it Ruppersberger and CISPA, or Aramco?
As expected, Dutch Ruppersberger has reintroduced CISPA following Obama’s Cybersecurity Executive Order. He must be hoping that the warnings voiced by Obama in the State of the Union address will strike a chord and somehow make CISPA more acceptable this time round. And he’s added his own warnings.
In an op-ed in the Baltimore Sun he writes:
August: Cyber attackers disrupt production from Saudi Aramco, the world’s largest exporter of crude oil, taking out 30,000 computers in the process, according to press reports.
Fight cyber crime through information sharing
It didn’t happen. At least Aramco says it didn’t. Yes, Shamoon took out 30,000 desktop computers, but it didn’t touch the production system which is on a separate network. So, regardless of whether there is some gutter press report somewhere saying that production was disrupted, it wasn’t. If it had, and oil production from the world’s largest exporter of crude oil had been disrupted, there would have been an almighty spike in world oil prices. There wasn’t – and Ruppersberger knows it. It’s a pure and simple lie for political purposes.
And it’s not the only truth distortion in his article. He says, “each of the above-referenced attacks could have been prevented by the federal government,” because “The U.S. government can often see the worms and viruses placed by hackers and other evil-doers in the computer networks that make up our modern world.”
Really?
I think if I was Aramco, I’d want to know what the US government was doing inside my networks monitoring unknown malware. On the face of it, if what Ruppersberger is saying is true, the implication has to be that the US government put it there in the first place – and that wouldn’t be the first time that has been suggested.
Later on, he suggests that “a hacker was able to access nearly 4 million tax returns in South Carolina with a single malicious email.” Well, we’ll gloss over the suggestion that the email was all it took, and remember the point he is making – that the government could have stopped this hack if it had been able to share its knowledge with the victims – which it can’t, by law. But the fact is, it did anyway. The South Carolina Tax Department only learnt about the hack because the Secret Service told them it was happening. So although the government can’t, it did – so why does it need new laws?
“We’ve gotten wake-up call after wake-up call,” he concludes. “It is time to work together to prevent the cyber nightmare from becoming a crippling reality.” He is absolutely right. Such shameful and twisted hyperbole should wake us up to the reality and motives behind this proposed law. The cyber nightmare is CISPA, and we need to work together to stop it becoming a crippling reality.
Oh, and once you’ve managed to stop CISPA, would you all just mind popping over here to help us get rid of the UK’s Communications Bill and the EU Cybersecurity Directive – both of which are actually much worse than CISPA…
See also…
Don’t we care about liberty in Europe?
The confustication of cyberwarfare
Don’t we care about liberty in Europe?
Finally, someone in the UK’s mainstream press has woken up and noticed the EU Cybersecurity Directive – Europe’s CISPA. The Daily Mail, so usually in the pocket of any Conservative government, has spoken:


The language is typical Mail sensationalism, but the facts are essentially correct. The worry is that this EU Directive goes much further than Cameron’s cherished Communications Bill – already broadly known as the Snoopers’ Charter. The danger is that because it’s from the EU, which already owns our legislative process, Cameron and his GCHQ puppet-masters can just turn around and say, sorry guys, we’ve got no choice, the Treaty of Lisbon blah blah blah…
But the surprise is that this dangerous, draconian, police state Directive – much more extreme than CISPA in the US; which incidentally will be re-introduced in the US on Wednesday, along with a presidential executive order decreeing the same thing – is causing hardly a ripple in Europe. Are we so punch-drunk by the politically motivated economic crisis that we are already dead? Do we not care about liberty in Europe any more?
Access to communications data by the intelligence and security Agencies
Have a look at this flow chart. It’s taken from the Intelligence and Security Committee’s report on the Communications Bill, and “illustrates how the elements of the Bill would work in practice.” It is UK democracy at work.
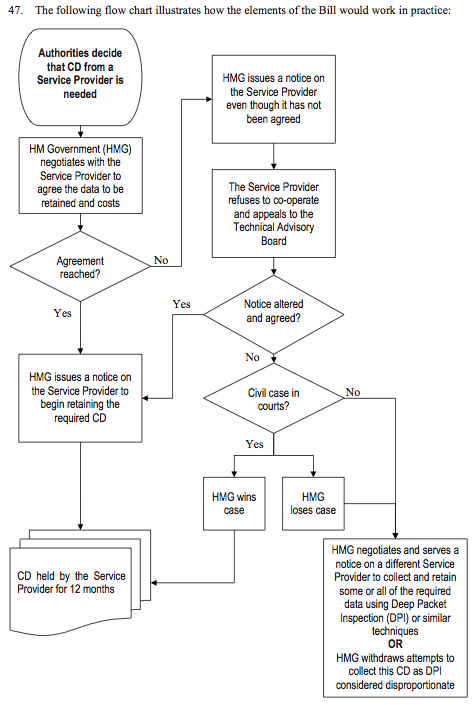
It starts with the authorities deciding that certain data is wanted. If the service provider objects, see how he has the right to appeal. If he accepts the request, he gets a notice to retain the required data. If he rejects the request, he gets a notice to retain the required data. If he still objects, it might go to court. If he wins the case, “HMG negotiates and serves a notice on a different Service Provider to collect and retain some or all of the required data using Deep Packet Inspection (DPI) or similar techniques.” In other words, they chose a different ISP and start all over again. That’s pure democracy: keep asking the question until you get the answer you want.
Of course, it’s not the only worrying thing about the Access to communications data by the intelligence and security Agencies report. My primary concern is that it is not an investigation into the Communications Bill at all. It is really a libation to the Bill. Its only criticism is that the government should have done a better job at selling the Bill to the population. But having said that, the Committee still tries to obfuscate and mislead.
Consider the section on ‘encryption’. It is heavily redacted (another example of modern democracy: ‘don’t tell the plebs what we’re doing’). It effectively says little more than


From the encryption section of the report

Makes you wonder, doesn’t it. What are those ‘options’? And what does it mean for the service provider to provide an unencrypted version of encrypted communications data?
I asked two interested experts to explain the issue for me – and rather than try to comment on their replies, I’m reproducing them in full.

James Firth, CEO of the Open Digital Policy Organisation Ltd
The problem arises because communications can be – effectively – layered. So a portion of ‘content’ at one (higher) layer is actually communications data at a lower layer.
A classic example is webmail. Alice logs in to mail service provider G via secure HTTPS and sends a message to Bob. All her ISP knows is that Alice has a web session with G.
Various proposals being touted – sometimes in the various drafts – include forcing mail service providers to abide by the Comms Bill. Jurisdiction could be enforced in some way for any company with a UK presence, but it would be impractical as the Bad Guys would just use other companies.
But there have been scarier options touted.
If Alice didn’t use a secure method to connect to her mail service provider her ISP could be forced to scan all CONTENT in order to detect nested communications data. In this model her ISP would scrape the email “to” and “from” fields from her web session. I doubt this would pass muster with various EU Directives but that’s been suggested.
Even scarier suggestion – if Alice DID use SSL to connect to her mail service provider it has been suggested – I have a very good contact confirming this – that legislation could be introduced to force her ISP to store the whole encrypted transaction, even though this includes the content.
The idea being that HMG could get a court order – here or in e.g. the US – at a later date to force her mail service provider to disclose their private SSL key. From that it would – in *some cases* – be possible to replay the SSL transaction to discover the session key and decrypt the contents, then extract the communications data, and – honest guv – ignore any content.
The major flaw in this plan is that Google, as one mail service provider, has rolled-out a feature called forward secrecy (http://en.wikipedia.org/wiki/Perfect_forward_secrecy).
Forward secrecy introduces, essentially, a second negotiated secret into the SSL transaction; a secret known only by the client web browser. The protracted SSL handshake with forward secrecy ensures that if one private key was later compromised – e.g. the mail service provider’s key – an attacker would still not be able to reproduce the plaintext from a captured encrypted session.
Clever mail service providers would never want to be in a position where they are forced by a court to hand over their private keys, so forward secrecy is actually in their interests as it devalues their private key as it won’t alone decrypt a captured session. In fact the second secret needed to decrypt a session with perfect forward secrecy should have been destroyed by the client and the server as soon as the session ends.


Alexander Hanff, managing director at Think Privacy Ltd
When an SSL connection is made a ‘tunnel’ is set up and as a result all of the HTTP headers are encrypted (these include the specific web page you are requesting from the server) but the TCP and IP data is not encrypted as they exist on different OSI layers – HTTP/SSL exist in layers 5-7 whereas TCP is layer 4 and IP is layer 3 (if my memory serves me correctly you might want to double-check that).
As you correctly state, it would be impossible to get the encrypted content to the server if the 3rd and 4th OSI layers were encrypted, so yes there is still a DNS lookup (which means the ISP knows the domain and the IP address you are trying to communicate with) but they would not know which web page you are trying to access within that domain.
The same should be true of emails which are not hosted by the ISP (for example I run my own email servers) they would know which email server I am trying to communicate with but since my emails are transported over SSL/TLS the would not know whom I am communicating with or anything else which is held within the encrypted packets (I run my own email servers to circumvent the Data Retention aspects of RIPA/Data Retention Directive).
That said, the ISP could easily set up Man in the Middle attacks similar to how Phorm did with their DPI boxes which would allow them to decrypt everything (including the content) which is what I presume was the redacted content in the report released yesterday when they were talking about the government has a feasible method of dealing with encryption. This of course would be completely illegal under RIPA (without a warrant) so they would need to introduce legislation to do this (which would put them in breach of the EU Data Retention Directive but as we know the UK gov are not good at complying with EU Directives so they probably wouldn’t care).
So in summary, yes encryption restricts them from obtaining some of the higher level data they want but not the low-level data such as domain and IP.

Notice that there is one common element in these two replies: further legislation. It seems highly likely, then, that this Communications Bill will be supplemented by altogether more intrusive legislation (the ‘options’) when the authorities finally realise what everyone has been telling them: this Communications Bill isn’t what they say and will not work. And that, of course, is democracy at work: keep asking the question until you get the response you want.
The Horseless Carriage Bill
I propose that motorised vehicles be banned. They kill innocent women and children in our streets. They allow serious organized criminals to get to and escape from the scene of their crimes. They carry terrorists to training camps and targets. They allow paedophiles to cruise the streets looking for their prey, and provide enticements to promote abduction. And they kill many, many more innocent members of the public than terrorism does. The police should have the power to arrest any and all drivers of horseless carriages on sight.
As Theresa May said today in an exclusive interview in Rupert Murdoch’s Sun newspaper
The people who say they’re against this bill need to look victims of serious crime, terrorism and child sex offences in the eye and tell them why they’re not prepared to give the police the powers they need to protect the public.
Anybody who is against this bill is putting politics before people’s lives.
We would certainly see criminals going free as a result of this.
Track crime on net or we’ll see more people die
I endorse this wholeheartedly. Ban the horseless carriage. All of those pinko liberals who claim that such a law would destroy any value in a free society worth defending against serious criminals, terrorists and sex offenders are lily-livered apologists who simply don’t understand that control is far more useful than liberty.
FUD marketing: a stick generated by the industry and wielded by governments
One of the things that worries me is the steady stream of inflated or unprovable statistics showing how dire the cyber threat has become. I am not alone in this concern. Ross Anderson and his team at the Cambridge University Computer Lab famously objected to statistics prepared by Detica for the Cabinet Office. On being invited by the Ministry of Defence to come up with their own defensible statistics, they produced a report showing that, statistically, government would achieve much better security by catching the crooks than by applying increasingly more expensive and sophisticated security systems.
But government doesn’t want to do that. As far as government is concerned, security is achieved by control. Having control of the internet and control over the internet’s users will provide the security they want (and the megalomaniac satisfaction they crave).
It is made worse by a huge security industry that can only survive if we buy its products. And the more afraid we are, the more money we will spend and the richer they will get.
So the poor bloody user is caught in an inescapable pincer: both the government and industry want us to be afraid – and horrific statistics and hyped up warnings created by industry and spread by government will do just that.
Here’s an announcement that came out the other day from NCC. Headline: “Hacking attempts to exceed one billion in the final quarter of 2012”. That’s pretty scary.
Rob Cotton, CEO of NCC Group, comments later in the announcement,
We’ve had copious initiatives and plans announced in the last quarter from bodies and governments aimed at addressing this issue, but the urgency just doesn’t seem to correlate with the growing threat… but these initiatives alone are not going to solve the problem. Public and private sector must work together, strategically and tactically, if we are going to be able to realistically defend against a billion hacks a quarter.”
Notice two things: government initiatives (including, I assume, the Communications Bill and GCHQ’s Incident Response Scheme and the Digital Economy Act and RIPA and Baroness Howe’s internet censorship – and that’s just in the UK) are not yet enough to tackle the hacking that has suddenly morphed from ‘attempts’ to “a billion [actual] hacks a quarter”.
A hack is generally speaking the unauthorised access of a computer. According to Mr Cotton, we are currently suffering from more than 333,000,000 every month (or more than 10,000,000 every day). Clearly the government must pass more laws and we must spend more money with the security industry so that we don’t suffer another 10 million hacks tomorrow.
It is only at the very end of the announcement we find the rider, “Stats do not necessarily indicate successful access, just unauthorised attempts.” On this basis, the quoted figure will include automated port scans. (I remember watching such scans click up on my PC at one every few seconds and being stopped by a very early version of ZoneAlarm – say, 5 per minute or 300 per hour or 7200 per day or around or 216,000 per month or around 648,000 per quarter – just for little me and all stopped by my little free firewall.) Add to this every spam email that carries a link to an exploit kit – which can be described as a hacking attempt – and suddenly the one billion figure seems rather conservative but not particularly frightening.
But this is what government and those parts of the security industry close to government do. Its called FUD marketing – they get what they want by disseminating fear, uncertainty and doubt; and they do that by huge, poorly defined and not often defended, scary figures and statistics. If you think we’re being manipulated, it’s because we are.
Good morning, Mr President
Barack Obama has been re-elected. Millions of Americans will be congratulating themselves while millions of others will be wondering what went wrong. Very few understand the reality that votes no longer matter: the winner of any election will be the candidate most likely to deliver what the Secret Service (intelligence services in the UK) currently want.
Obama’s masterstroke was the ‘promise’ of an executive order to fulfil the stalled Cybersecurity Act just before the election. Romney’s failure was business distaste for the Act.
We’ve had it in the UK for decades. A politically astute socialist turned socialite stayed in power for a decade on the promise of delivering centrally controlled national ID cards. When public distaste became overwhelming he was replaced by Brown – but as soon as it was clear that Brown couldn’t deliver a pizza, he too was dumped.
Enter the genius of Cameron. Tell the people you will roll back the database state while telling the intelligence agencies you will do no such thing. Curtail RIPA (well, limit the snooping capabilities of the jobsworth man-from-the-council while leaving the rest intact), but keep the Digital Economy Act and deliver on promises with the new Communications Act.
Don’t worry, it’s all just a fairy tale. It is, isn’t it?
Statistics, false statistics and damned government lies – the Communications Bill and Theresa May
Theresa May, the Home Secretary, has today re-iterated her and the government’s commitment to the Communications Bill, dubbed by many the snooper’s charter. She was answering questions from the joint parliamentary committee examining the proposals.
I wasn’t there and I have no transcript, so I’m taking the BBC report at face value. It says:
“The aim of this is to ensure our law enforcement agencies can carry on having access to the data they find so necessary operationally in terms of investigation, catching criminals and saving lives.” (said May)
Of the 30,000 estimated cases last year where the police made an urgent request for communications data, between 25% and 40% of them resulted in lives being saved.
Draft Communications Bill: May says web monitoring will save lives
I’ve never heard this before. Between 7500 (25% of 30,000) and 12,000 (40% of 30,000) lives were saved last year because of urgent police requests for communications data? I’ll be honest here: I don’t believe it.
But the question remains, where have these figures come from. Even this government wouldn’t dare pluck random figures from the ether without some face-saving backup.
Well, back in June the Home Office published a document called Communications Data Bill – key background information. It includes the following:
Many tens of thousands of communications data requests are made every year in urgent threat to life situations: e.g. to find a vulnerable or missing person or in kidnap situations.
Communications Data Bill – key background information – 14 June 21012
Ten thousand is not many tens of thousands. Twenty thousand is just a couple of tens of thousands. Thirty thousand could – at a pinch – be described as ‘many tens of thousands’. Logically, then, the figure mentioned back in June accounts for the entire 30,000 cases ‘where the police made an urgent request for communications data’ last year mentioned today by May. It’s the same 30,000 in both cases.
Those requests are largely (we can assume, since that is all that is mentioned) to do with missing persons and kidnaps. (I would guess that kidnaps are far fewer than missing persons requests.) This assumption has some weight because the next premise could, at a pinch, be true: if a missing person is not found, he or she could be presumed dead; or at least would have died if not found. Tenuous, but arguable.
This could easily be used to justify a claim that between 25% and 40% of such requests led to missing persons being found and lives being saved. And I don’t believe anyone would object to communications providers handing over limited intelligence (after all, they know precisely who they are looking for) as quickly as possible in these cases.
Where these figures cannot be used is to justify the blanket surveillance of the entire population on the basis that we’re all potential terrorists and criminals; and that just because missing children and vulnerable lives are saved, so will many more because of the Communications Bill.
That is such a blatant distortion and misuse of statistics that it goes beyond being damned statistics and is a pure and simple blatant lie.
Telegraph becomes the latest media organization to collude with government propaganda
“Britain is target of up to 1,000 cyber attacks every hour” says the headline in a Telegraph article today. It comes from William Hague, UK Foreign Secretary, in his latest interview with the media.
What neither Hague nor the Telegraph do is explain where this figure comes from, nor what type of attack is meant. Last month the White House was breached by Chinese attackers who gained access to US nuclear secrets. The reality is there was a single, but unsuccessful, phishing attack that got past the primary defences. You have to wonder if similar disinformation is at work here.
If we’re talking about ‘all’ attacks, then I would suspect this is an unrealistically conservative figure – 1000 attacks per second – scam, spam, skiddie probes, phishing et al – would be more realistic for the whole of the UK. But limiting the figure to just 1000 makes the reader assume this is 1000 serious, APT-style attacks against the critical infrastructure alone. The problem is, no details are given, leaving the reader to assume the worst.
This lack of detail pervades the entire article/interview.
Hackers and foreign spies are bombarding government departments and businesses around the clock in what has become one of the ‘greatest challenges’ of modern times.
As well as targeting state or trade secrets, the cyber criminals and anarchists also try to disrupt infrastructure and communications and even satellite systems.
Britain is target of up to 1,000 cyber attacks every hour
Anarchists threaten the internet? Really? Typical fear-mongering, reminiscent of the Russian hacker who attacked a US water utility (not), or the attack on Brazilian power supplies that turned out to be soot on the insulators.
This speech is just another fear-mongering attempt by the government to ease the passage of the Communications Bill, and is typical of the sort of government warnings, on both sides of the Atlantic, that always precede new legislation.
That’s not to say the internet is safe. It isn’t. There are problems, lots of problems and serious problems. We think we’re secure when we’re not. But that’s not the underlying message from Hague and GCHQ. The underlying message here is that terrorists (and anarchists!) are attacking the UK, and the only solution is to pass more laws giving government more powers and us less liberty. The security industry joins in with this conspiracy by leaping on every word the government utters – even though they said it first – and claiming government endorsement of the need for business to buy their products. Government wants our liberty and the security industry wants our money.
But it’s the final two paragraphs of this article that should worry us most.
The Intelligence and Security Committee, appointed by the Prime Minister, believes Britain should declare cyber war on states and criminals who target the country by using aggressive retaliatory strikes to destroy their own operations.
Security and intelligence agencies should be willing to engage in covert cyber attacks on enemy states using programs such as the Stuxnet virus that targeted Iran’s nuclear ambitions, the committee members say.
The worrying thing is not the sentiment – we’ve already been doing that for years. The worrying thing is that government is now openly advocating what it is already doing secretly. The implication is that if things are that bad, we’re effectively at war. War invariably involves martial law. Martial law of the internet is what the government is after. If we think we are at war, attacking and being attacked, we are more likely to accept the draconian laws that the government wants to enact – for our own safety.
We are being manipulated into accepting the loss of liberty. It is disgraceful that a newspaper like the Telegraph should support this manipulation.
WikiLeaks, Antileaks, DDoS, Stratfor and TrapWire
Life is a game of cricket – sometimes you face bouncers, and sometimes beamers; but usually it’s spin and swing. The internet is full of spin and swing, with business, government, law enforcement and hackers all trying to spin the news to their own advantage in order to swing public opinion behind their own position. It’s called disinformation, and everyone’s at it. But like cricket, you only need one ball to spin or swing, and you cannot trust anything ever again.
So with that introductory warning that I really haven’t got a clue, we can ask, what’s going on with WikiLeaks? This is one possibility. It’s all down to TrapWire and the information about TrapWire coming out of the latest WikiLeaks Stratfor emails.
TrapWire seems to be an international surveillance system centred in and run by the US. It makes Cameron’s Communications Bill look pedestrian. That’s not strictly accurate, since the Communications Bill watches people’s cyber movements, while TrapWire watches real world movements; that is, pedestrians (and cars and anything else that moves). It connects the nation’s CCTV surveillance cameras. As an aside, we can be pretty confident that when (not if) the US gets its Cybersecurity Act, that data will be connected to the TrapWire data. What’s more worrying for Brits is that when (not if) Cameron gets his Communications Bill into an Act, that data will also be connected to TrapWire.
This latter is just conjecture, but look at the parallels in UKUSA and do the math. Also consider this from one of the WikiLeaks emails (dated 22 September 2010):
This week, 500 surveillance cameras were activated on the NYC subway system to focus on pre-operational terrorist surveillance. The surveillance technology is also operational on high value targets (HVTs) in DC, Las Vegas, Los Angeles and London and is called TrapWire (www.abraxasapps.com).
So TrapWire was already operational in the UK almost a year ago.
Well, of course I checked on the Abraxas site (a company apparently populated by a high density of ex-CIA staff), but got nowhere.
It’s not just me.
There’s no buzz on the internet (yet at least) that Abraxas has been tangoed down by Anonymous (in retaliation for Antileaks taking out WikiLeaks). So – pure conjecture – they’ve taken it down themselves.
Thank goodness for Google cache (if you’re quick, it might still be there…)
and…
It wouldn’t be surprising if Abraxas has disconnected itself. This TrapWire thing is big, and the Stratfor emails show it’s being used much wider than published. It’s bad enough that the UK government wants to spy on its own citizens (using our taxes to pay for it, of course), but that it has already opened the door to facilitate US government spying on the British people is quite simply obscene. Or, to be British, unacceptable. I can’t begin to think what the American people will make of it.
So, to go back to the original question, what’s going on with WikiLeaks? The obvious conclusion is that it has been taken down (well, effectively blocked) by a continuing DDoS that has been claimed by Antileaks specifically to suppress the emerging information about TrapWire (WikiLeaks is still down as I write this). This is just conjecture on my part; but, well, the dots connect. Under the guise of anti-terrorism western governments will stop at nothing in their determination to have absolute control over us.