Archive
China lets slip the true purpose of the European Union
From Radio 4 satire many years ago:

John Major: Who won the bloody war anyway?
Helmut Kohl: Who said it’s over?

Well it is now!

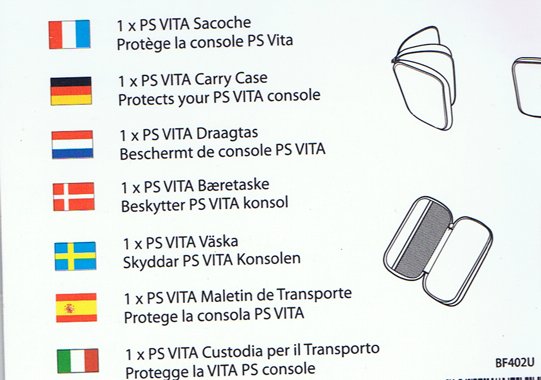
The packaging from a carry case for the PS Vita

This is from a Chinese-made PS Vita carry case. Hint: check the flags and languages…

Hat tip to Daniel Gyenesse.
Europol warns about a new wave of illegal immigrants infiltrating Europe
Listen to the pundits and they will tell you that the world faces a terrifying cybergeddon in 2013: open nation-sponsored cyberwarfare; critical infrastructure meltdown caused by cyberterrorists; worldwide banking system brought to its knees by criminals and Anonymous; hacked drones attacking Capitol Hill courtesy of Iran; terrorists and paedophiles rampaging up and down the information highway; and murder, extortion and rape by the internet of things.
That’s why it was so reassuring to learn that the world I grew up in hasn’t quite gone forever. Australian and North American biker gangs are taking over the real world in Europe. “The arrival of Comancheros and Rebels from Australia, Rock Machine from Canada, plus Mongols and Vagos from the USA creates tension with established outlaw motorcycle clubs in Europe,” warns Europol.

Source: Europol
It’s good to know that the old traditions, the “propensity to use extreme forms of violence” with “the use of automatic rifles like Kalashnikovs, and explosive devices such as grenades” hasn’t disappeared completely. Who needs cyberwar when we’ve got Hells Angels patrolling the streets?
It does sort of put your feet back on the ground, doesn’t it?
Re-Tweet this post – it’s part of my plan to beat the recession
In order to beat the recession I need to expand. In order to expand I need a business loan. In order to get a business loan I need to improve my Klout.
No, really.
I went to the bank. No.
I went home, juggled some figures on the business plan to improve the bottom line projected profits and went back. No.
Apparently it has nothing to do with business potential, it has only to do with collateral. That is, I can have it if I can prove I don’t need it.
There must be another way. So I checked American Banker and found this in Thursday’s issue:
CAN is joining a growing list of companies chasing small business loans by using alternative data sourcing. These companies include Kabbage, which uses social media data as part of lending decisions… Lighter Capital also uses social networking data…
Big Data Comes to Small Business Online Lending
So I checked back into the earlier issues, and found this:
The company [Kabbage] is incorporating social media activity into its analysis now, Frohwein [founder and CEO] says. “We allow our customers to associate their Twitter and Facebook accounts. As our theory goes, the more active you are at keeping in touch, gaining followers, and responding to them, the more likely you’re running a solid, growing business and you’re worth an additional risk. Or there’s less risk associated with you so we can provide more cash or at a lower rate.”
The 10-Minute Small Business Loan
So that’s the plan; and that’s where you come in. Tweaking the bottom line of my business plan no longer works – but with your help I will be able to tweak the bottom line of my Klout score and get the low-interest business loan I so richly deserve. So please use the ‘share’ buttons below: tweet, like, repost, Reddit, whatever – or all – for this post. Do it for Christmas and the lulz, and I’ll still beat the system. You know I’m worth it.
Wonderful graphic from AlienVault: The Eternal Life of Malware
But it does make you wonder why the West is so concerned about cyberwar when it is clearly the world’s greatest protagonist. Do as you would be done by, I say.
The inclusion of Shamoon is interesting. Does it imply that AlienVault considers it is state-sponsored by Iran? If so, the current cyberwar score seems to be US/Israel 5, China 1, Iran 1.

Storing passwords: why you should flavour your hash with salt
Rider: I am not a cryptographer, so this is an attempt at my understanding of any consensus between genuine cryptographers. If I’ve got anything wrong or you disagree, let me know – or comment.
A cryptographic hash function is widely used to ‘encrypt’ stored passwords. Strictly speaking, it is not encryption: encryption is something you can scramble and then unscramble mathematically – it is two-way. A hash is one-way: it generates a meaningless output (often called a digest) that bears no relation to the input, and cannot mathematically be used to recreate that input. Other characteristics are that it always produces a constant length output regardless of the size of the input, and that no two different inputs will produce the same output.
These characteristics make the cryptographic hash ideal for the secure storage of passwords:
- the plaintext user password is neither stored nor can be recovered mathematically from the hash
- no two different passwords will create the same hash
- the fixed size makes storage simple.
So, when a user account is created, a user password is either created or selected by the user. It is run through the hash function, and a hash is generated and stored with the user name as part of the user account. The plaintext password is not stored and cannot be recovered from the hash.
The next time the user logs on to the account, he or she has to re-present the password. That password is run through the hash function again, and the hash output is compared to the one stored in the user’s account. If they match, access is granted. If they don’t match, access is refused.
If the server is breached and the password database is stolen, no matter, the passwords are securely and irreversibly scrambled. Right? Wrong.
The problem is that attackers have become adept at cracking hashes. It can’t be done mathematically, but it can be done by brute force. In fact any password can be cracked by brute force – brute force simply means that every possible combination of characters and symbols is tried until the correct one is found.
Generally speaking, this is a theoretical possibility rather than a practical reality: even with modern computing power, brute forcing all the possible combinations would take too long to be of any use.
There are many riders to this. The computational power of parallel GPUs or FGAs is improving the time of brute-forcing hashes; so brute forcing just a few hashed passwords is realistic. If the attacker recognises the username of a few high value targets and has the computational power, he could concentrate on brute forcing just those hashes – using, for example, HashCat. Note that Jens Steube, the author of HashCat, has just published a methodology that can reduce the effort needed to brute force SHA1 by 21.1%.
But the attackers have adapted brute force into the so-called ‘dictionary attack’. Here, hashes for millions of the most likely passwords such as names, dates, places, combinations of them, l33t speak variants (h3110_w0R1d), and everyday words in multiple languages are pre-computed and stored in a table or dictionary. Now, instead of having to try every possible output against every possible input, the attacker merely has to take the output and compare it to the dictionary in order to locate the plaintext password. With a good dictionary attack, most passwords can be recovered from the hash in just a few seconds or minutes.
 And this, finally, is why you should flavour your hash with salt.
And this, finally, is why you should flavour your hash with salt.
Salt is a unique random string prepended to each plaintext password before the hash is generated and stored. “What the salt does,” Robin Wood, aka security researcher and pentester DigiNinja, told me, “is prevent an attacker generating a pre-computed list of the hashes.” Robin developed the widely used Pipal password analyser – and knows a thing or two about passwords.
The characteristics of the salt should be a reasonable length, and genuine randomness. Any old pseudo-random number generator isn’t good enough – it should be a cryptographically secure random number generator. (If you want to consider the effort that goes into a good random number generator, have a look at the independent report produced for Intel by Cryptography Research Inc on the Intel Ivy Bridge RNG.)
(Not everyone believes the salt needs to be truly random, just truly unique to each password. However, if it isn’t generated randomly, there is a danger that it becomes predictable.)
This salt is then added to the plaintext password and the hash generated by the combination. Ultimately it does nothing to prevent a brute force attack, so in this way doesn’t make the security stronger. But what it does do is defeat the dictionary attack. The dictionaries cannot contain all of the hashed standard passwords plus all of the possible hashes of each of those passwords with a large random number (or salt) included. Provided that the salt for each password is unique, it needs no security in itself – on its own it can tell you nothing about the plaintext password that is included in the stored, combined hash.
Dictionary attacks are one of the reasons for users to choose a long, strong password. If the password database isn’t salted, a long complicated password may avoid precomputation and still defeat the dictionary.
Unique salts also have the added advantage of creating unique hashes for every user, regardless of their plaintext password. In a Pipal analysis of “the list of passwords from the phpBB leak which I grabbed from the SkullSecurity site,” DigiNinja shows that the top two passwords are ‘123456’ and ‘password’ – and these are likely to figure highly in any list of passwords. Without a unique salt, it would be statistically likely that the most frequently occurring hashes have been generated from one or other of these passwords, even without the use of a dictionary. With unique salts, however, every single stored hash will also be unique, and no statistical analysis will be possible. A long and unique salt is thus important to prevent a standard salt being guessed or discovered by statistical analysis. If the attacker knows a standard salt, he could just precompute an additional dictionary with that added salt.
Conclusions
What this tells us is that the user must do two things: choose long, strong passwords to defeat dictionary attacks where the website doesn’t use salting; and never to reuse the same password on multiple accounts. Using the same password means that it is only as safe as the weakest account we use; and the simple fact is we do not know which websites are storing our passwords safely. It is also sobering to realise that the strength of the password we choose is meaningless if the website stores it in plaintext, and then gets breached.
For the website, it tells us that hashing passwords is essential; but on its own, hashing will not protect the majority of passwords from a dictionary attack.
The addition of a unique, long and genuinely random string appended to the password before hashing will provide a far greater defence against password cracking, without requiring any additional effort to secure or hide the salt itself.

UPDATE:
Jeremi Gosney has demonstrated dramatically improved brute forcing with a cluster of GPUs running Hashcat: see GPU cluster can crack any NTLM 8-character hashed password in 5.5 hours
The Data Protection Regulation should be amended to force companies to disclose how passwords are stored
Over the last couple of days it has been disclosed that an amazing amount of personal data on 1.1 million Americans has been lifted from the US Nationwide insurance group. Passwords do not appear to be involved – it’s a storage of data rather than an interactive site. But the point is that this data would appear to have been unencrypted – at least the company concerned hasn’t specified one way or the other; and that’s the problem.
Time and again we learn of plaintext passwords being stolen. Plaintext is unacceptable, but it happens. Sometimes, they are stored hashed by SHA1. This is unacceptable because dictionary attacks and Jens Steube’s newly announced brute force attack makes them surprisingly vulnerable; but it happens. At the very least, passwords should be stored hashed with SHA1 – preferably better – and salted.
I for one would be reluctant to commit my password to any site that stores that password with anything less than salted SHA2. But they don’t tell us, do they.
So I call now for the European Commission to amend the proposed Data Protection Regulation to include a requirement for all sites that store user passwords to make it clear on their site, at registration, precisely how those passwords are stored: plaintext, hashed (with what), or hashed and salted. This is the only way we will be able to force vendors to improve the way in which they handle our data.

See also: Storing passwords: why you should flavour your hash with salt
The Horseless Carriage Bill
I propose that motorised vehicles be banned. They kill innocent women and children in our streets. They allow serious organized criminals to get to and escape from the scene of their crimes. They carry terrorists to training camps and targets. They allow paedophiles to cruise the streets looking for their prey, and provide enticements to promote abduction. And they kill many, many more innocent members of the public than terrorism does. The police should have the power to arrest any and all drivers of horseless carriages on sight.
As Theresa May said today in an exclusive interview in Rupert Murdoch’s Sun newspaper
The people who say they’re against this bill need to look victims of serious crime, terrorism and child sex offences in the eye and tell them why they’re not prepared to give the police the powers they need to protect the public.
Anybody who is against this bill is putting politics before people’s lives.
We would certainly see criminals going free as a result of this.
Track crime on net or we’ll see more people die
I endorse this wholeheartedly. Ban the horseless carriage. All of those pinko liberals who claim that such a law would destroy any value in a free society worth defending against serious criminals, terrorists and sex offenders are lily-livered apologists who simply don’t understand that control is far more useful than liberty.
What an Italian thinks is wrong with the UK
Call me naive, but I would expect a guy with a BA in International and Diplomatic Studies, an MSC in Economics and Politics of European Integration, and an MA in International Relations to have a fairly subtle grasp of, well, international relations. This is Giuseppe Luca Moliterni’s take on why more than 50% of the UK population would like to leave the EU:
Main UK problems regarding the European Union can be then summarized as follows: UK still believes to be an empire and to have that kind of power; UK still believes to be the privileged partner of the United States; UK still believes to have a say in foreign policy especially in the European Union because of Catherine Ashton position. As the three elements concur in understanding the failure of UK in adapting its position in a more complex world , they also do create a single framework to understand why UK is a broken hero: it is not possible to live in the past!
Broken heroes: UK – EU Relations – Part 1: UK
With apologies to the Welsh and Scots members of the UK, I am adding this rank (and may I add ignorant, arrogant and aggressive) anglophobia to my other reasons for wishing to leave the EU: that I believe nations should be governed by their own people; that people should be able to elect the government executive; that the EU as it stands is corrupt, bloated and controlled entirely by and for the Franco/German duopoly; and that the natural order of things is small rather than large and that large will always and inevitably disintegrate into small. As for that last point, the longer the disintegration takes, the bloodier it becomes – and I sincerely hope that neither I nor anyone I know and love is around when the European Union tears itself apart in bloody civil war. Better to break up now in a controlled and amicable manner.




