Archive
ACTA and the Time Warp
Before I go further I need to offer thanks to three sources. Firstly, to Monica Horten at the excellent IPtegrity blog who saw the connection. Secondly to the genius of Richard O’Brien who penned such a prescient prophesy. And thirdly to the authors of ACTA, without whom – well, I wish we were without whom.
The story reported by Monica is the jump to the left in the European Parliament (socialist rapporteur says he recommends that ACTA be rejected) followed by the step to the right (EPP Sarkozy-ite delays things to buy more time for the rightsholder lobbyists to regroup) – and it was Monica who made the connection with Richard O’Brien. (I’ve reported the ‘news’ side of this story on Infosecurity Mag) “ACTA: EU Parliament takes a step to the right,” is Monica’s headline. “It took a jump to the left…” is the first line.
“It’s just a jump to the left And then a step to the right” is the source in Richard O’Brien’s phenomenal Time Warp song from The Rocky Horror Picture Show. What I hadn’t realised is quite how accurate those lyrics turn out to be.
Hollywood/government lays out its intention for the internet: It’s astounding, time is fleeting – Madness takes its toll – But listen closely, not for very much longer – I’ve got to keep control
But users are lost in their own, innocent, dreamy vision of the internet: It’s so dreamy, oh fantasy free me – So you can’t see me, no not at all
This is such a romantic view of freedom and the internet! But Hollywood/government responds: In another dimension, with voyeuristic intention – Well-secluded, I see all – With a bit of a mind flip – You’re there in the time slip – And nothing can ever be the same
This is O’Brien at his most prophetic. Hollywood/government wishes, from a hidden point of view, to see everything that happens on the internet. And once they succeed, nothing will ever be the same again.
O’Brien goes on to foretell what will happen. The user concludes: Well I was walking down the street just a-having a think – When a snake of a guy gave me an evil wink – He shook me up, he took me by surprise – He had a pickup truck and the devil’s eyes. – He stared at me and I felt a change – Time meant nothing, never would again.
Hollywood/government wins. The Time Warp itself? They will just keep cycling round in a time warp, time and time again, until they succeed. Just beware when that snake of a guy gives you an evil wink – and make sure you never vote for him again!
Time for ACPO to go
Back in February I commented on David Harley’s blogs on the Association of Chief Police Officers (ACPO) National Cyber Crime Conference. David attended as a speaker. He blogged afterwards, “The constantly recurring conference theme of working with other sectors rather than using them purely as an information feed into a black box, seems a more positive approach.”
At the end of my post I said:
Incidentally, I have asked for reports from the conference, but been told that “There will not be an output report from this event but a brief summary will be available in the next week or so.” Well that’s a good start for a two-way information exchange.
I finally received the brief summary today, more than two months later. Here it is in full:
Due to the confidential nature of the discussions which took place as part of this conference, Forum members have made the decision not to publish this to a wider audience.
Well, I’ve said it before, but I’ll say it again. The police have no right to be secretive about how they police. They should be more open – they are, after all, our servants. I am a firm supporter of elected chiefs of police and the abolition of this unaccountable, self-fulfilling, private company funded by private donations and public money that is known as ACPO. It’s time they went.
Keynote sessions from Infosecurity Europe 2012 – and a few other stories
Infosecurity Europe is over for another year. If you weren’t there, well I just suggest you make sure you get there next year. Meantime, here’s my take on a couple of the announcements and almost all of the keynote sessions:
Infosecurity Europe 2012: Minister of State for Universities and Science introduces the 2012 security breaches survey
The challenge, says the Rt Hon David Willetts, is that in order to get the economic and social benefits that the internet offers, we need to first tackle cyber security.
24 April 2012
PwC and Infosecurity Europe release the latest Information Security Breaches Survey
Significant attacks more than double, but one-in five companies still spend less than one percent of their IT budget on security, and more than half of small organizations do no security training at all.
24 April 2012
Russian cybercrime: what Russia is doing, and what it should be doing
Russian security company Group-IB says Russian cybercriminals made £2.3b in 2011; Russian-speaking cybercriminals made more than $4b; and worldwide, cybercriminals made more than $12.5b.
24 April 2012
Trustworthy Internet Movement Launches Pulse Tracker
The problem, says Pulse, is that we are telling users that this site has SSL, so it’s secure. That’s not necessarily true. We are promulgating a false sense of security, and we need to fix that.
25 April 2012
Infosecurity Europe 2012: defining risk management in the context of information security
The three companies represented on the keynote panel (G4S Secure Solutions, Steria UK, and Skipton Building Society) are very different; and their CISOs have very different views on the functioning of risk management within infosec.
25 April 2012
Infosecurity Europe 2012: the rising role of the CISO
Chaired by Quocirca’s Bob Tarzey, Network Rail’s CISO Peter Gibbons and Yell’s CISO Phil Cracknell led a lively discussion on the current and future role of the CISO.
25 April 2012
Ipswitch survey reveals the extent to which IT is losing control over data
IT needs governance; but users are choosing simplicity. In choosing and using their own non-sanctioned methods for data transfer, users are causing IT to lose control over its own data.
25 April 2012
Infosecurity Europe 2012: AET & APT – Is this the next-generation attack?
Advanced persistent threats (APT) and advanced evasive techniques (AET): what are they, who’s doing them, and what can we do about them?
26 April 2012
Has the time come to dump anti-virus?
Bit-9 asks the question that dare not be spoken: is anti-virus beyond its sell-by date? And is BYOD the final straw?
26 April 2012
Infosecurity Europe 2012: The ICO on better regulation and better infosec
Christopher Graham, the UK Information Commissioner, talks about his role as an information regulator and facilitator at Infosecurity Europe in London
26 April 2012
Infosecurity Europe 2012: Are we smart enough to secure smartphones?
Three heads of security from three very different organizations came together to discuss their practical and very different experiences in introducing a company BYOD strategy.
26 April 2012
Infosecurity Europe 2012: The insider threat – is it real?
While the primary security stance faces outwards and is designed to keep hackers and malware outside of the system, organizations are increasingly aware that their own staff are also a potential – and in some cases an active – threat.
27 April 2012
Infosecurity Europe 2012: The cloud – do you really know what you’re getting in to?
The cloud is new; but it’s been around for years. It’s insecure; but more secure than we fear. Two practitioners discussed the cloud of FUD.
27 April 2012
It’s the lack of understanding of virtualization that makes security an issue
A new study from Kaspersky Lab confirms an earlier one from Crossbeam Systems: it’s a lack of knowledge about virtualization that leads to fear for its security.
26 April 2012
Anonymous calls for citizen action against CISPA
CISPA, the Cyber Intelligence Sharing and Protection Act, was rushed through the House of Representatives on Thursday last week. It was passed by 248 votes to 168. On the previous day, Wednesday, President Obama – or more specifically, the Office of Management and Budget – warned that he would veto the bill: “Legislation should address core critical infrastructure vulnerabilities without sacrificing the fundamental values of privacy and civil liberties for our citizens… for the reasons stated herein, if H.R. 3523 were presented to the President, his senior advisors would recommend that he veto the bill.”
Doesn’t mean he will veto the bill. Guantanamo? NDAA?
It’s a possibility not lost on Anonymous. On Friday it issued its own citizen call to arms. It’s not asking for the usual DDoS attack – at least not yet, because it’s not clear who would need to be attacked, but it does say:
President Obama has already stated that he will veto the bill, but this is also what was said about NDAA.
Anonymous’ call is:
We have defeated previous attempts to censor our only platform of true honest communication, the internet. SOPA was only the beginning.
Sign petitions, call your congressmen, and kill this act in the senate.
As a foreign observer I would say that one thing is very clear about CISPA: it is being sold to the American public on a tissue of lies, misconceptions, misleading claims and overarching FUD. It will do nothing to prevent terrorism. It will do nothing to curtail crime. But it will allow both US law enforcement and the entertainment industry to legally spy on the private and legitimate communications of both innocent US citizens and everyone else anywhere in the world. A specific misleading endorsement? Joel Kaplan, Vice President-U.S. Public Policy, Facebook, wrote:
Importantly, HR 3523 would impose no new obligations on us to share data with anyone –- and ensures that if we do share data about specific cyber threats, we are able to continue to safeguard our users’ private information, just as we do today [my ironic emphasis].
If the American citizen can expect the same from the US government as the Facebook user can from Facebook, then expect your personal data to be covertly extracted and sold to the highest bidder. It’s time to listen to those great advocates of US free speech: ACLU, EFF, CDT and, I have to say, Anonymous.
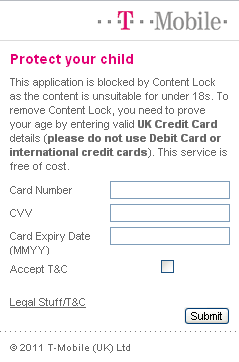
Don’t you just love these ISP child blocks?
I see T-Mobile is at it again. I wanted to have a look at the Ardagh Group. The little I could get was from the Google search blurb: “Ardagh Group is a leading packaging business operating 88 facilities in metal, glass and technology across 25 countries. We employ 14100 people, produce in …” After that, T-Mobile blocked any further access, saying that the content was unsuitable for children.
There’s a number of points here. Firstly, I would like to thank T-Mobile for suggesting that I am under eighteen. Secondly, I suggest that the Ardagh Group sues the arse of T-Mobile because I was about to place a £££multi-billion order with them – and now I can’t. And thirdly, I’d like to suggest that T-Mobile reconsiders the stupidity of its actions.
I have only ever paid for the service by card. They already have my card details. They know from their own records that I am actually 23.
But look at what they want to unblock the Ardagh Group and grant me access to this pornographic, paedophiliac, money laundering, drug running haven of unspeakable depravity: credit card details, not debit card details. I don’t have a bloody credit card. I only ever use a bloody debit card. How TF am I going to prove to them what they already know when they won’t accept the proof they already have?
Infographics are a con and a betrayal of their purpose
I dislike infographics. Nine times out of ten they are a betrayal. When they appear on the author’s website, one time out of ten, they’re fine. When they’re sent to me with the invitation that my blog readers will be interested, they’re a con; and I dislike them almost as much as I dislike the people who send them.
I got another yesterday. The covering letter said:
“Don’t be evil.” Google’s unofficial corporate motto was originally adopted as company-wide belief as well as a jab to its competitors. However, Google has come a long way since it was incorporated in 1998. Can we still trust Google to do no evil? There is increasing evidence to suggest that the answer is ‘no’. Please check out our infographic on Google to learn more and please feel free to reuse it on Kevin Townsend using the embed code provided at the link.
Of course we can’t trust Google. We can’t trust anyone or anything on the internet. What we do is try to understand the issues and act within the level of risk we are prepared to take. But many of us still don’t realise how much data Google has on us – so a nice graphic explanation sounds appealing. I had a look.
It starts with the same paragraph that was used in the email. It ends with “Or you can simply quit using Google products altogether…”
But it was sent to me by anothermarketingconman@gmail.com – clearly someone who believes in what he preaches. And then you see the purpose of this con: the advert for the author of the infographic. Sending these infographics to bloggers in order to get free advertising is a con; and a betrayal of the true purpose of infographics.
Nevertheless, I had a look at the advertiser. Would you believe it? Background checks. “Background checks can be a great way to ensure the safety of your family, home, and employees. You can use them to look up information about an individual’s criminal, financial, and educational history, and then use that information to make an informed decision about that individual’s character and trustworthiness.” Here’s a company effectively complaining about the private information gathered by Google saying ‘we can get you more.’
I dislike infographics. I dislike this one with a vengeance.
Infosecurity Magazine news stories for 10-13 April 2012, and 16-18 April 2012
My news stories on Infosecurity Magazine from Tuesday 10 April until Friday 13 April, and Monday 16 April until Wednesday 18 April
NHS needs a security czar to prevent continuous data walkabout
While the South London Healthcare NHS Trust signs a Data Protection Undertaking, the security industry wonders why we have learnt nothing in the last two years – and calls for a new NHS data protection czar.
18 April 2012
PwC 2012 Information Security Breaches Survey: Preliminary findings report continued mobile insecurity
New statistics show that while many companies appear to understand the business threat from BYOD, many others are taking no precautions whatsoever.
18 April 2012
(ISC)² launches its new EMEA advisory board
In a move designed to offer genuine hands-on security experience to EMEA’s different security initiatives, professional body (ISC)² has launched a new Advisory Board for Europe, the Middle East and Africa (EAB).
18 April 2012
Google co-founder worries about the future of the internet
In an interview with the Guardian, the co-founder of Google lists the threats facing the future vitality of the internet.
17 April 2012
Shadowserver uncovers campaign against Vietnam in Hardcore Charlie’s file dump
An analysis of the hacked files dumped by hacker Hardcore Charlie fails to prove Chinese culpability, but finds evidence of ‘yet another cyber espionage campaign against Vietnam.’
17 April 2012
Iranian software manager hacks and dumps card details of 3m Iranians
Khosrow Zarefarid found and reported a flaw in the Iranian POS system. He reported it, but was ignored – so he used it and hacked 3 million Iranian debit card details.
17 April 2012
Dutch Pirate Party forced to take its Pirate Bay proxy off-line
In a move that will be monitored by the UK’s music industry association (BPI), its Dutch equivalent BREIN (translates as ‘Brain’) has obtained a court injunction forcing the political party, the Pirate Party, to take down the proxy site that was allowing users to continue using the blocked Pirate Bay (TPB).
16 April 2012
Is ACTA dead in the water, or is it resurfacing via the G8?
David Martin, European Parliament’s rapporteur on the ACTA treaty, is expected to recommend that parliament should reject ACTA. Does this mean the end for the Anti-Counterfeiting Trade Agreement?
16 April 2012
Commotion Wireless: an open source censorship buster
The great contradiction in modern techno-politics is the need for democracies to promulgate free speech in other countries while controlling it in their own.
16 April 2012
Boston police release unredacted Facebook data of ‘Craigslist killer’
The complete Facebook account of Philip Markoff, in hard copy and including friend IDs, was given by the Boston Police to the Boston Phoenix newspaper.
13 April 2012
EC asks how we would want the internet of things to be controlled
The European Commission (EC) has issued an online ‘consultation’ document: How would you envisage ‘governance’ of the ‘Internet of Things’?
13 April 2012
City trader fined £450,000 by the FSA
“For the reasons given in this Notice…”, says an FSA Decision Notice, “…the FSA has decided to impose on Mr Ian Charles Hannam a financial penalty of £450,000.”
13 April 2012
MPAA’s attempted takedown of Hotfile gets more and more difficult
Don’t throw the baby out with the bathwater says Google; and there’s more baby than bathwater suggests Prof. James Boyle.
12 April 2012
UK private members bill designed to censor pornography on the internet
Baroness Howe of Ildicote has introduced the Online Safety Act 2012, designed to force ISPs to install and operate pornography filters.
12 April 2012
Financial services the target in massive DDoS increase
A new analysis from Prolexic shows a huge increase in DDoS attacks, largely sourced in Asia and primarily attacking financial institutions.
12 April 2012
Smartphones are still firmly ‘enterprise-unready’
Research from by Altimeter Group, Bloor Research and Trend Micro shows that the ‘consumer marketing’ legacy of many smartphones makes them ill-equipped to meet enterprise security demands.
11 April 2012
EU trade committee’s draft opinion on ACTA: Don’t ratify
The European Parliament’s Industry, Research and Energy committee for the Committee on International Trade has published its draft opinion on ACTA. Don’t ratify, it tells parliament.
11 April 2012
DHS gets California company to hack game consoles
In a project that started from law enforcement agencies’ request to the US Department of Homeland Security (DHS), which was then farmed out to the US Navy, Obscure Technologies of California has been awarded a contract to find ways of hacking game consoles.
11 April 2012
Real-time data mining comes to Twitter
Twitter is usually described as a micro-blogging social network. To many who monitor its ‘trending topics’ it is also an early warning news service, frequently pointing users to breaking news before the traditional news media reports it.
10 April 2012
Iran bids farewell to the internet; welcomes its own halal intranet
Iran’s answer to ‘criminality’ on the internet is not to fight criminality, but to block the internet. In the future, Iranians will have access to only the official national intranet and a whitelist of acceptable foreign sites.
10 April 2012
What an Englishman does in bed
Companies that monitor the end point behavior of their remote workers will have to start monitoring their (internet) behavior in bed. That at least is the inference to be drawn from a new street survey conducted by Infosecurity Europe.
10 April 2012
Who is the real criminal?
“On average, supporting House members received $52,000 from the media industry, vs an average contribution of $13,000 to opposers. Supporting Senate members received $99,000 from the industry, while the opposers received $33,000,” says buythevote.org in relation to SOPA and PIPA.
“Those who count on quote ‘Hollywood’ for support need to understand that this industry is watching very carefully who’s going to stand up for them when their job is at stake. Don’t ask me to write a check for you when you think your job is at risk and then don’t pay any attention to me when my job is at stake,” said MPAA lobbyist Chris Dodd.
Downloading files. Buying and selling laws. Who is the real criminal here?
Thank god we don’t live in Vietnam or China or Iran
Vietnam is reportedly due to issue a new decree in June entitled “Decree on the Management, Provision, Use of Internet Services and Information Content Online”. It will among other things,
Force foreign companies that provide online services such as social networking, blogging, discussion forums and chat to cooperate with the Vietnamese government and provide it with the information it needs to crack down on activities banned by the decree.
(Reporters Without Borders)
It’s what we have come to expect from authoritarian undemocratic communist regimes. Thank god we have the Free West to protect our freedom, free speech and privacy. All that’s happening in the US is the Internet Rogering Act (otherwise known as Representative Michael Roger’s Cyber Intelligence Sharing and Protection Act – CISPA). And of course all CISPA does is allow companies like Facebook and Microsoft and Google and ISPs to share our personal data freely without just cause or due process or legal redress with themselves and the government because they feel like it.
Well at least we’ve got the UK, with its mother of parliaments, habeas corpus, proud history of tolerance, freedom, justice and other detriments to effective government. All the UK government (you remember, that one that condemned Labour’s authoritarian attitudes when it was in opposition) is doing is the preparation of an unnamed bill to be presented at the earliest opportunity and designed to force all ISPs to provide total traffic information on demand, in real-time, without just cause or due process or legal redress, on all UK citizens to the government’s spy agency (GCHQ). That’s everyone you speak to and every website you visit.
So they’ll know if you speak to a criminal (or terrorist) even if you don’t know it’s a criminal (or terrorist), and you will forever be associated with that criminal (or terrorist) even though you don’t know it. And they will know which websites you visit, whether it’s politically subversive (ie, not in line with government thinking), or pornography (eg, Sun Page 3), or whatever. They’ll know you’re going there probably before you even get there.
But don’t worry. All of us real criminals and terrorists will easily get round both the US and UK laws with encryption and foreign proxies and the onion web – so it’s only the innocent citizens that will actually be affected. Thank god we don’t live in Vietnam or China or Iran.
Security is bought with liberty
Security and Liberty are opposite ends of the same see-saw. If one end goes up, the other must necessarily go down. The problem is finding the right balance between the two. Unfortunately, those with responsibility over our security will always tip the balance in their own favour, thus reducing our liberty. This is dangerous when it is government, for it is an inevitable road to a police state – and both Europe and the US are already a long way down that road.
But it shows itself at every level. The security industry itself faces this dilemma every day: do they do everything they can to protect their customers, or do they temper their actions and beliefs with civil liberty issues?
Here’s a case in point. Apple’s response to the Flashback trojan is, says Wolfgang Kandek, CTO of Qualys, ‘innovative’. “Apple released today a new, quite innovative version of Java for Mac OS X 10.7 and 10.6. Innovative, because the new version does not fix any vulnerabilities, but instead addresses two of the current Java on Mac landscape problems,” he writes. Firstly, it erases known variants of Flashback; and secondly “it automatically disables Java when it has not been used for the last 35 days.”
Wolfgang is pleased with the latter. “It makes total sense to me: we have been telling users to disable or uninstall Java if they do not need it, but we know very well that only very security conscious users will do so.” That’s a security man speaking. But my view is the opposite: Apple has no right to arbitrarily mess with my computer.
By taking away my responsibility for myself, by taking control of my security for me, Apple is simultaneously making me less likely to be personally responsible in the future, while also making me more likely to accept the security dictates of government. Already one of government’s standard arguments whenever it proposes some new form of surveillance is “if you haven’t done anything wrong, you don’t have anything to worry about.” And we actually think they have a point because our concept of our own freedom is constantly eroded.
But the reality is this: because I have done nothing wrong, you have no bloody right to spy on me. So whenever a security man, government or industry, says to you, we’ll look after your security, ask yourself at what cost?