Archive
Democracy. It’s just an awkward device to make the people feel important
The great weakness in democracy is that whenever you ask the people what they want, they choose something other than what they’re going to get. The great strength is it doesn’t matter: you can always ignore them, go round them or go over them. Whichever route you choose, those damn people will have what we give them.
So, in the UK, the government always chooses self-regulation over legislation. Getting internet censorship legislation voted through the two houses will be difficult; but persuading the ISPs to voluntarily enforce that censorship, step by step, will be easy. The UK simply ignores democracy.
The EU goes round the people. Ask the people and they’ll throw it out, like ACTA. So the EU gets round democracy by sidestepping it; like the private deal being discussed by the Clean IT project between the ISPs and the law enforcement and intelligence services. This way there’s no pesky parliament interfering, and no awkward judges to satisfy.
But both of these approaches are too lily-livered for the macho American presidency. Obama’s approach is to drive straight over democracy and sod the people. If the judges declare his NDAA unconstitutional, so what? He’ll have it anyway. And if Congress rejects his Cybersecurity Bill, who cares? He’ll force it through on an executive order regardless of the people.
Democracy. Pah! Who needs it.
A secretive EU project is designed to close down the internet on demand
A terrorist is someone who advocates terrorism. Terrorism is the use of violence and threats to intimidate. A bit like some of our police do all too often.
Anonymous has responded by urging the public to shoot the police – with their phones. “We ask you to videotape and record the police during their daily duties. If you see an officer issuing a parking ticket, record him. If you see an officer holding a victim at gun point, record him. If you see an officer harassing a fellow protester, record him.”
For this our governments define Anonymous as cyberterrorists. Have you ever thought that’s a bit over the top?
Well, the problem is that Anonymous – and especially Anonymous+WikiLeaks – is far more dangerous than a real-life terrorist. Terrorist bombs do not topple governments; but the truth does. You can shoot a man holding a bomb; you cannot (easily) shoot a man holding the truth. But if you label the man with the truth a terrorist, then you can shoot him. And if you label the truth terrorism, then you can hide it.
In Europe there is a secretive project called Clean IT, funded by the EU (that is, by us), but designed to be without political control. Its stated purpose is to prevent the terrorist use of the internet, and it is driven by law enforcement and security agencies. It says it wants to do this “without affecting our online freedom”. That’s what it says. A secret internal document leaked by EDRi says otherwise.
But before we look at the document, remember that as far as these law enforcement and security agencies are concerned, terrorist includes Anonymous. By extension, that includes anyone who supports Anonymous. And by extension, that means anyone of us who may have ever voiced support for or agreement with any Anonymous action. It’s a short hop to realise that this argument, the prevention of terrorism, can be used against anyone.
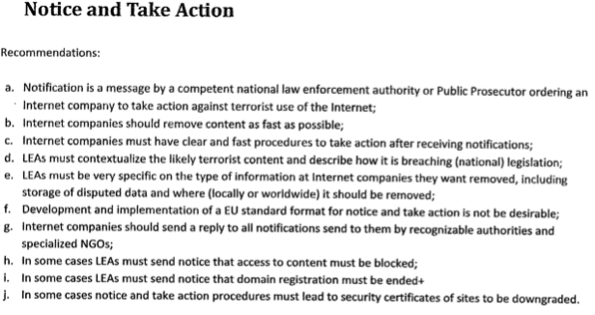
So, to the document. It is called Clean IT Project – detailed recommendations document for best practices and permanent dialogue. And it is headed, on every page, ‘confidential’ and ‘not for publication’:
But we needn’t worry because the whole project is designed to prevent terrorism – just like RIPA, used by Moray Council in Scotland to monitor the ‘underage sale of tobacco’, is an anti-terrorist law. So how does Clean IT define terrorism? It doesn’t.
Is there any guidance? Well, yes there is…
Have a closer look at this. ‘Unwanted by local society’ even if it ‘is fully legal’ and ‘in line with terms and conditions of the relevant service provider’. And who is to decide whether it is unwanted by local society? Why, the LEAs and security agencies of course. The next section is reproduced in full. Look closely for any mention of the courts or court orders or legal process or legal redress. Look and weep for what they secretly want to do: the Clean IT project will be used against anyone and anything the authorities do not like.
BBC finally smells the coffee
“Malware ‘was not from factories’, Microsoft says” is today’s headline. “Several outlets, including the BBC, reported that harmful software was being pre-installed on PCs at the manufacturing stage,” admits the BBC. Actually, it had said “Cybercriminals have opened a new front in their battle to infect computers with malware – PC production lines.” It said that because it didn’t bother reading the Microsoft reports.
And we told them they were wrong five days ago in our own reporting: China is a pariah.
Five days to get it right. Is there an agenda here?
Keep up, or fall behind, as they say.
Townsend slips into the Grammar Fascisti
As I get, well, more mature, I find myself becoming increasingly intolerant of these highly paid (often by my taxes), poorly educated (even though they probably got A-Star A-levels and red-brick double-firsts) moronic murderers of the English language. (If you are more than forty, this doesn’t apply.)
In the weeks prior to the Tour of Britain coming to the rural backroads of Devon, garish yellow signs appeared at regular intervals along the roadsides.
Advanced notice… they said. I tried; I tried very hard, but could find nothing advanced about them. They were, in fact, very basic notices – just simple prior warnings of weaponised wheels spinning far too fast.
But I became more and more apoplectic with every advanced notice I passed. If you cannot use the English language correctly, go back to school. Don’t get paid for annoying me!
There. Feel better now. Stay calm and keep taking the medication.
Recent stories on Infosecurity, featuring Trend Micro, phishing for Apples, NullCrew and more…
A few of my recent stories on Infosecurity Magazine over the last couple of days…
Peter the Great beats Sun Tzu in cybercrime
Despite the hoohaa about the ‘Chinese cyberthreat’ (in reality, read east Asia), Russia’s Peter the Great (in reality, read east Europe) is beating Sun Tzu in modern cyber wargames. Eastern Europe has better cybercriminals than eastern Asia.
Beware of iPhone delivery phishes
iPhone pre-orders are now showing a 3-4 week shipping estimate. Since Apple announced that 2 million pre-orders were sold for the iPhone 5 in just 24 hours, delivery delays are not likely to disappear quickly.
NullCrew: the principled hacker group?
In a wide-ranging interview broadcast over online Spreaker radio but conducted probably via IRC, UK Anon Winston Smith has been talking to Null, the leader of the NullCrew hacking group.
Quantum Key Distribution takes to the air
An aircraft in flight has successfully transmitted quantum encryption keys to a ground station, bringing closer the time when satellites can be used to provide a theoretically (allegedly) secure communications network.
YouTube declines to remove Mohammad video clip
Asked by the White House to reconsider whether the infamous Mohammad video clip is in violation of its terms of service, Google has replied that it is not. Although it is blocking the clip in Egypt, Libya, Indonesia and India, this, says Google, is in keeping with local laws.
AlienVault doxes the man behind the PlugX RAT
AlienVault has been tracking the PlugX remote access trojan for some months, and following extensive detective work has now uncovered enough information to name the person behind it.
The confustication of cyberwarfare
A simple glance around the contemporary threatscape shows that cyberwar is getting increasingly confused and complicated: confusticated, in fact. Nation states are (allegedly) attacking nation states; criminals are attacking infrastructures; nation states are (allegedly) controlling criminals; criminals are attacking the people; and the people are rebelling against their governments.
Let’s start at the top: state-sponsored cyber attacks. It came to the surface with Aurora two years ago – and incidentally, the gang behind it, whether state- (for which read ‘China’) sponsored or not, is still active – blossomed with Stuxnet and Duqu and went into overdrive with Flame and Wiper. The last four are all (allegedly) part of a US/Israeli campaign against Iran; and this is not cyber-espionage, this is pure war.
The thing about Wiper is that it is destructive. It attempts to be – and succeeds in being – a new form of ‘stealth’: it self-destructs to avoid being taken alive. And as far as is known, there is still no live Wiper in captivity. First, as far as we understand, it steals data; then it destroys data; and then it kills itself.
After Wiper we had Shamoon, and this is where things start to get complicated. Shamoon seems to be a poor copy of Wiper, and is believed to have been used to attack the Saudi oil company, Aramco – and possibly the Qatari energy company RasGas two weeks later. Now we are in the land of conjecture. Shamoon could have been designed and used by traditional criminals; but that idea doesn’t quite hang together.
Another theory points the finger at Iran. Shamoon, it suggests, is an Iranian retaliatory strike following Stuxnet and Flame; and targeting Aramco because of the Saudi promise to increase oil production to offset the effect of sanctions against Iranian oil. This theory suggests that since Iran was the primary target of Wiper, it more than any other source would be well-positioned to develop a copy – and indeed Shamoon does appear to be a poor copy of Wiper.
This political theory of Shamoon is supported internally by the malware itself. Part of its data wiping process is to use a fragment of a JPG file. That picture has now been recognised: it is a picture of a burning US flag. What we don’t know is whether Shamoon is state-produced in the same way as Stuxnet, Flame and Wiper; or whether it is produced by criminals ‘encouraged’ by the state. Incidentally, we are in exactly the same position with Aurora. The gang behind Aurora, called the Elderwood gang by Symantec, is still very active and still targeting primarily US defense companies. Is it China or Chinese criminals or Chinese criminals ‘encouraged’ by China?
The simple fact is the confustication of modern cyberwarfare means we neither know nor are likely to know the answers to these questions: plausible deniability lies at the heart of all cyber criminality.
Now let’s consider hacktivism, the ‘civil war’, or just civil rebellion part of cyberwarfare – Wat Tyler Vs the king. Anonymous is the seminal hacktivist – but not the only actor. Since the demise of LulzSec, Anonymous has largely undertaken its protest through DDoS (not entirely, since it was involved in first stealing huge volumes of Iraqi emails, and then leaking them to WikiLeaks). But now it has been ‘joined’ by NullCrew, adding to the hacking power of AntiSec. AntiSec may be mainstream Anonymous; but NullCrew is separate. It just has similar sympathies, and many of its recent hacks have been performed in the name of the Anonymous-led and politically motivated #OpFreeAssange.
Both AntiSec and NullCrew are seriously ‘talented’ hackers. AntiSec recently stole a large number of Apple UDIDs from either the FBI or BlueToad, depending on who you believe. Null Crew hacked a Cambodian Army site, Logica, Cambridge University, the European Space Agency and more and more. 0x00x00, perhaps a member of NullCrew, perhaps not, has undertaken his own Assange campaign, breaking into numerous websites and leaving an Assange poster calling-card.
But while we’re talking about hacktivism, let’s not forget that the king has his own men – the FBI (and SOCA) acting within the king’s law, and Jester – that ‘hacktivist for good’ – acting outside of it. The latter recently took on and took out a well-respected site, Cryptocomb, in what Cryptocomb openly described as a ‘state-sponsored’ attack. Now, if this isn’t confusticating enough, there is even a civil war within the rebels. One faction has been calling for a more organised Anonymous with a supreme council directing operations – only to be slapped down by the existing Supreme Council of One, Commander X. There will be no Supreme Council for at least as long as Commander X remains in charge (which, of course, he is not, other than by general consensus). Confused yet?
Well let’s summarize. There is a legal cyberwar being fought by the US and Israel (and if you believe the cyber-underground, the UK was involved – shortly before his very strange death, it is claimed that Mr Williams had been commuting between GCHQ and the NSA, and had just started talking about whistleblowing on something; all just before Stuxnet exploded. AntiSec claims on Pastebin, “And then you have Gareth Williams (31), the GCHQ hacker murdered and ‘bagged’ inside a MI6’s ‘safe’ house (we’d hate to see what the unsafe ones look like) in August of 2010 after talking about being curious about leaking something to Wikileaks with fellow hackers on irc.”
Then there is an illegal war of retaliation being fought by Iran, together with old-fashioned cyberespionage from China. And finally, the war against terror has spread to the battle against Anonymous (always classified as cyberterrorists, and therefore within the purview of the war on terror, by the king’s men) in an attempt to quell the cyber rebellion.
But – and we have to stress this – it is all conjecture, allegation and confustication. The problem is, we haven’t mentioned that primary weapon of all warfare used by all antagonists against all enemies: disinformation. And all sides are very good at it.
From Obama to Assange – the evolution of Hope
Take one copyrighted AP photograph of Obama and flip it. Then posterize it and create an iconic work of art – the artist Fairey’s Obama Hope poster. Then take the idea and create an Assange poster.
The idea is brilliant. It’s an image that everyone recognizes, and suggests that our hope for the future is no longer Obama and what he stands for but Assange and what he stands for.
But there’s a problem. AP sued Fairey for copyright infringement. And Fairey himself has issued a cease-and-desist notice to another artist he termed a ‘parasite’. This image has a history, and the protagonists know the law.
Now, I don’t know who ‘created’ the Assange poster. But it’s clearly ‘trading off’. And I do know who’s been distributing it. Forsaking the traditional walls and telegraph poles, 0x00x00 has been using other people’s websites as his whiteboard.
Pissing off SOCA by hacking websites is one thing – but pissing off The Rightsholders is an altogether more dangerous tactic.
The irony…
What irony. As I link to my story on over-hyping the China threat, LinkedIn links to a story that over-hypes the same story. This one is from The Independent: “Microsoft admits millions of computers could be infected with malware before they’re even out of the box”. I’m afraid that I missed both the ‘millions’ and ‘before they’re even out of the box’ comments from Microsoft. Oh, no, I didn’t – they’re not there.
China is a pariah
It subverts our websites, steals our IP, floods us with spam, sabotages our infrastructure, destroys our jobs and rapes our women. It has to be stopped. And if that takes billions of pounds, dollars and euros in taxes, we understand.
Show me the proof.
OK, well, yes, here it is.
Malware inserted on PC production lines, says study
BBC
Several new computers in a Chinese factory were found to have been infected with malware which was installed there, according to a study by Microsoft.
ZDNet
Some computers have been infected with malware on the PC production line, says Microsoft…
TVNZ
Malware infecting PCs on production line, Microsoft says
CBC News
Pre-installed malware in production lines spurs Microsoft’s 3322.org takedown
Infosecurity Magazine
I could go on, but that should be proof enough for anyone – the Chinese have been caught installing malware on the computers they manufacture.
Only that’s not what Microsoft says. There are two primary sources for this story: a Technet blog and a PDF report. ‘Production line’ is never mentioned in either document. The only mention of the source is that “we discovered that retailers were selling computers loaded with counterfeit versions of Windows software embedded with harmful malware.” It does not say who those retailers were. Nor does either document ever say that they were new computers. For all we know, they were second, third-hand PCs sold off a barrow in a back street. And frankly, if you bought one of those in London’s street markets you deserve everything you get preloaded on it.
Microsoft has been very careful in its wording – not so much what it has said, but what it has left unsaid. And by not being clear on where it obtained the PCs nor in what state it bought them, it has allowed the over-hyped anti-China sentiment to shine through our media. This is encouraged by the UKUSA governments in order to divert more of our taxes to the intelligence agencies who will primarily use it to spy on their own citizens. And so far, it looks as if they will get away with it.
My favourite quote on the whole subject comes from the chief security guy at China’s Huawei Technologies. He said, “The bottom line is that you can’t assume that all things East are bad, and all things West are good. In terms of security, we have to be suspicious of everybody.” Before you dismiss that as clever propaganda, its worth considering the chief security guy’s pedigree. His name is John Suffolk and in his own words, “I have 7 years’ experience in the UK Government and was Her Majesty’s Government CIO and CISO for 5 years steering £16bn IT budget per annum using 50,000 IT professionals (after outsourcing).”
I’m not for one second saying that China is good and UKUSA is bad; but I’m saying that so far there is no actual proof for all of the accusations leveled against China. Certainly no proof like a President admitting government involvement in cyber attacks (Stuxnet et al) against a sovereign foreign state. So before you believe all of this anti-China bull, remember that our own governments are at least as bad – and that they are promoting this feeling in order to award the intelligence services even more of our money.