Archive
The eBay hack, the loss of 140 million records, and the PR fiasco
There are two functions to PR: the first is to shout the good news from the hilltops, while the second is to bury the bad. When bad news hits, PR says very little.
Bad news has hit eBay. It admitted Wednesday that it had been hacked – but it actually gives very little information. This is a mistake. It means that people will comb their words used looking for clues over what has actually happened. The result is conjecture; but what follows is the conjecture of some very clever security people.
Three things leap out from the eBay statement. The first is the repeated use of the word ‘encrypted’, with no mention of hashing for the passwords. The second is the duration of the breach – it occurred in February/March, but was only discovered a couple of weeks ago. And the third is the mention of the database – not part of, nor a geographical region, but the (whole?) database. So what can we surmise from all this?

Ian Pratt, co-founder of Bromium
Firstly, were the passwords encrypted or hashed? It makes a difference. The implication from the statement is that they were encrypted. Most security experts believe that this would be a mistake – passwords should be hashed and salted. In fact, Ian Pratt, co-founder of Bromium, goes so far as to suggest, “It would be rather unusual to encrypt passwords rather than hash them; it’s probably just lack of precision in the statement.”
But that’s what we said about the Adobe breach – and it turned out that the passwords were indeed encrypted rather than hashed. The opinion among the experts I talked to is fairly evenly balanced – while eBay’s semantics suggest they used encryption, many experts find it hard to believe. “This heavily implies that the passwords were not hashed,” said Chris Oakley, principle security consultant at Nettitude. “eBay’s report suggests that the passwords were encrypted rather than hashed,” added Brendan Rizzo, Technical Director EMEA for Voltage Security. Sati Bains, COO of Sestus, said, “Yes… it appears from the comment that they did [encrypt rather than hash].”
“Encryption and hashing are often confused with each other,” explains Jon French, a security analyst at AppRiver. “But from the sounds of the [eBay’s] press release, it seems they were using some sort of encryption.”
Andrey Dulkin, senior director of cyber innovation at CyberArk, is in no doubt. “Indeed, from the eBay statements we understand that the passwords were encrypted, rather than hashed. The fact that the statements repeatedly use the words ‘encrypted’ and ‘decrypted’ supports this interpretation.”
It is, of course, possible that eBay is simply not differentiating between the two processes, since most of its customers will not understand the difference. “The public understand the word ‘encrypted’ more than hashed – so encrypt is frequently used in place of hashed. But it is believed they were hashed,” suggests Guy Bunker, spokesperson for the Jericho Forum and a cyber security expert at Clearswift.
Ilia Kolochenko, founder and CEO of High-Tech Bridge (HTB), doesn’t believe we can tell from eBay’s comments. “The difference isn’t easily understood by users. Even the spokesperson might not be aware. It’s quite possible that the company simply didn’t want to introduce the complexity of describing the technicalities of hashing and salting in a brief announcement.”
What’s the difference, and why does it matter?
The primary operational difference is that encryption can be decrypted; that is the original plaintext can be retrieved from the ciphertext through the use of the encryption key. Hashed outputs cannot be mathematically returned to the original plaintext.
In practice, an entire database of passwords would be encrypted via a single encryption key. But if hashing was used, each individual password would ideally have an unknown value added to it (a ‘salt’) and the results would be separately hashed. “This salt,” explains Voltage’s Rizzo, “is a way to make sure that the hash of a particular password cannot be compared to the known hash of that same password by the attacker through the use of rainbow tables.”
This means that if an encrypted database is stolen, only one key needs to be found to unlock every password in the database.If the passwords are hashed, every single password needs to be cracked individually.
“The advantages to hashing,” Nick Piagentini, senior solutions architect at CloudPassage, told me, “are one, there is no need to manage sensitive encryption keys; two, hashing processes have less overhead to run than encryption processes; and three, there is no need to reconstruct the password data from the hash. Encryption would only be used if there was a need to get the original password back.”
Could the hackers have the encryption key?
This is the 64 million dollar question (and is only relevant if the passwords were encrypted). We don’t know, and we may never know. But it is certainly possible. There are two possibilities: it could have been cracked or it could have been stolen.
Reuters spoke to eBay spokeswoman Amanda Miller:
She said the hackers gained access to 145 million records of which they copied “a large part”. Those records contained passwords as well as email addresses, birth dates, mailing addresses and other personal information, but not financial data such as credit card numbers.
Hackers raid eBay in historic breach, access 145 million records
eBay says the database was compromised some time around late February or early March; but wasn’t discovered until about two weeks ago. What we don’t know is whether the compromise was still in active use by the hackers, what else they did during the two months they were undetected, or whether they left something unwelcome behind. Frankly, I find it hard to believe that having gained access without being discovered the hackers did not have a good look round.

Chris Oakley, principle security consultant at Nettitude
(Incidentally, it is worth pointing out at this point another comment from HTB’s Kolochenko. Basically, eBay’s statement that financial details were safely stored on a separate server is pretty meaningless. “The two servers would have to communicate,” he explained. “The hackers could have installed some malware to listen to the communication between the servers, and sniffed the plaintext traveling between them.”)
So could they have found the encryption key? Opinion is divided. “This is a primary argument for using hashing over encryption for password storage,” comments Nettitude’s Oakley; “an attacker who is able to compromise the database may also be in a position to obtain the encryption key(s).” (Incidentally, if the passwords were hashed rather than encrypted, the hackers could just as likely have found the salt or salt mechanism, rendering the hashed passwords relatively easy to crack via rainbow tables.)
On the other hand, “I would hope they [eBay] didn’t ‘tape the key to the door of the safe’”, comments Trey Ford, global security strategist at Rapid7. “eBay and PayPal have solid security teams, and go through regular third-party assessments. I refuse to believe they would handle encryption key materials that poorly.”
And yet they left the users’ email addresses and other personal information unencrypted. If they were using encryption seriously, they would have used a hardware security module (HSM) to house the keys, and would have encrypted everything. “They do not seem to be very confident about their encryption system,” comments Sebastian Munoz, CEO of REALSEC, “when they are suggesting their customers to reset passwords. If efficiently encrypted, using specific certified hardware, there would be no need to reset the passwords, since protection is guaranteed. When you use a Hardware Security Module (HSM) and not a simple and insecure encryption-by-software process, there is no way that hackers can gain access to the encryption keys.”
Munoz further suspects that software based encryption was used since only the passwords were encrypted. Since software encryption impacts on performance, then cost arguments come into play.

Sebastian Munoz, CEO of REALSEC
So, given the duration of the breach and the probable lack of an HSM, it is perfectly possible that the hackers also found the encryption key – and if this is the case, they now have access to all of the greater part of 145 million passwords, along with ‘email address, physical address, phone number and date of birth’.
If they did not find the key, would they be able to crack the encryption key? Again, opinion is divided – it all depends upon what encryption algorithm was used. Older encryption algorithms might be susceptible to a ‘known plaintext’ attack (see Wikipedia for details). Getting the necessary plaintext would be no problem. The most popular passwords are remarkable consistent – so a simple analysis with something like DigiNinja’s Pipal on an existing cracked database would provide a fair sampling of plaintext.
“However,” notes Bromium’s Ian Pratt, “assuming any kind of modern encryption (e.g. AES-128) was used then a known plaintext attack should not be feasible to recover the key and hence reveal other passwords.”
“Another approach,” suggested Clearswift’s Bunker, “is to ‘inject’ known passwords (either the hash or the encrypted version) into the database. This would create the equivalent of denial of service for the individual but would allow the attacker free reign over the account.”
The problem is we simply do not know what has happened. eBay’s attempts to downplay the incident is simply leading to conjecture.
UPDATE
While writing this report, Rapid7’s Trey Ford noticed adverts for the sale of eBay’s stolen database beginning to appear on Pastebin. “There has now been a posting on pastebin claiming to offer ‘145 312 663 unique records’ relating to the eBay breach,” he told me by email. We don’t know if they’re genuine, “it’s possible that a criminal has just spotted an opportunity to cash in on the attack with some other credentials dump they have.”
An analysis of the sample provided is inconclusive – the records are possibly genuine but not certainly genuine. But Ford had a look at the sample:
The sample that has been shared indicates that cracking the passwords will take considerable time. This is nothing like what we saw when LinkedIn was breached and the stolen credentials were quickly cracked due to only SHA-1 hashing being used for storage. In contrast, this credentials set is using PBKDF2 (Password-Based Key Derivation Function 2) SHA-256 hashes, which means they employ a strong hash function and also intentionally make cracking them more difficult and slow by individually salting and using a high number of hash iterations. The method used can be regarded as the state-of-the-art way to store passwords on web applications. Again though, we don’t know that these are credentials taken from the eBay breach, and no details have come from eBay on how they secure passwords.
This would fit in with eBay’s apparent confidence that the passwords cannot be hacked. However, Reuters spoke to eBay about the sample, and
eBay’s [spokesperson Amanda] Miller said the information was not authentic.
U.S. states probe eBay cyber attack as customers complain
AppRiver’s Jon French also noticed the Pastebin offer. He told me by email,
I’ll be wary of anything like this until I see people saying they see their own names (or if I end up seeing mine). Eventually if the Pastebin offer is legit, someone will post the file for free somewhere or some security company that buys it will verify authenticity.
His colleague, Troy Gill, a senior security analyst at AppRiver also suggested something that serious criminals will be well aware of: “There is always the remote possibility that this is a honey pot set by authorities to lure in would be buyers.”
Summary
eBay is taking the standard route for crisis management: say nothing. This is hugely disrespectful to its customers, who need and have a right to know everything possible. But eBay is also making a mistake in trying to downplay the effect of the stolen data. It says it has “no evidence of the compromise resulting in unauthorized activity for eBay users, and no evidence of any unauthorized access to financial or credit card information.” This is meant to make its customers feel better – the danger is that it might.
What eBay isn’t saying is that the unencrypted personal data also stolen (email address, physical address, phone number and date of birth) is a phisher’s wet dream. Armed with that information criminals will be able to concoct very compelling emails and cold call telephone calls. This is likely to happen on a vast scale and very soon. eBay might feel confidant about its own business, but the data it has lost puts millions of individuals and other companies in danger.
“When companies like eBay keep silent about the details,” commented High-Tech Bridge’s Kolochenko, “I would tend to expect the worst.” It is perhaps worth remembering the Adobe incident, which started off with a breach of a couple of million and slowly escalated into one of the worst breaches in history.
DoJ wants to make it easier for the FBI to legally hack innocent Americans
The precarious balance between law enforcement and personal privacy is highlighted by a new proposal from the Department of Justice — it wants greater leeway in its ability to place malware on multiple computers.
It can do this already, but not easily — it requires a judicial warrant that is only valid in the judge’s home district. Those warrants are not always automatic. In April 2013 magistrate judge Stephen Smith rejected such an application in Houston:
The Government has applied for a Rule 41 search and seizure warrant targeting a computer allegedly used to violate federal bank fraud, identity theft, and computer security laws. Unknown persons are said to have committed these crimes using a particular email account via an unknown computer at an unknown location. The search would be accomplished by surreptitiously installing software designed not only to extract certain stored electronic records but also to generate user photographs and location information over a 30 day period. In other words, the Government seeks a warrant to hack a computer suspected of criminal use. For various reasons explained below, the application is denied.
But even if it had been allowed, the warrant would only have been valid for the named computer within the judge’s district — the Southern District of Texas, Houston Division.
The FBI is now seeking a change in judicial rules to allow multiple searches on a single warrant, and for a single warrant to be valid for all 94 judicial districts. Its arguments are reasonable. Firstly, it may know the IP of a suspect computer, but not the precise geographic location. Secondly, modern organized crime can use hundreds if not thousands of computers in a crime — a botnet delivering a DDoS attack to disguise financial fraud for example. Obtaining individual warrants in all possible districts is difficult, time-consuming and expensive.
But there are huge privacy and security issues here. Firstly, the use of 0-day exploits by law enforcement will weaken the security of the internet itself. Secondly, placing spyware on the computer of an innocent person who ‘might’ be unknowingly harboring a bot (and thereby providing access to every intimate and confidential piece of data on that computer) is a dangerous attack on liberty and privacy.
But even more worrying, it is an attempt by the DoJ to make its surveillance desires easier to accomplish. The FBI could and would cherry pick its districts. Ninety-three of the districts might reject an application for a warrant as over broad and in conflict with the Fourth Amendment — but if there was just one sympathetic judge, the warrant would apply to the whole United States.
The FBI already cherry picks where it thinks it might get away with it. In the prosecution of Andrew Auernheimer it chose to prosecute in a district entirely unrelated to the case, but in which it could levy further charges and gain a longer sentence.
Now consider if the FBI had access to the NSA’s TAO catalogue of hacking tools (which it probably already has): no computer would ultimately be safe from the FBI, and the FBI would be acting entirely legally. We have seen over the last year that law enforcement and intelligence agencies have the attitude, if we can do it, we must do it. If the DoJ gets its way on this, the process will escalate until it is able to hack any computer, any time, on any whim.
TAO Inside
This graphic is lifted from a leaked NSA/TAO document published by Spiegel last week.
In case you still don’t know, TAO is the Tailored Access Operations group within the US National Security Agency. It is the heavy lifting – or we should say, the heavy hacking – arm of the NSA. It hacks the difficult targets; and very successfully. So successfully that it feels able to use this graphic:



Need anyone say more?
What ties Microsoft, surveillance, Syria and the Syrian Electronic Army together?
The Syrian Electronic Army (SEA) yesterday hacked Skype’s WordPress and Twitter accounts. The likelihood is that the pro-Syrian group got hold of the password used by Skype’s media people, probably through its usual method of spear-phishing. My report on the incident for Infosecurity Magazine is here.
But this hack was a little different to SEA’s normal escapades. The group’s whole raison d’être is to deliver pro-Assad messages to counter what it believes is anti-Assad propaganda controlled and delivered by western governments. This is the reason that it has concentrated on attacking high-profile media companies.
Well, Skype is certainly high-profile — but the message is not ‘Syrian’. On both the Skype Twitter account and its WordPress blog the SEA message was this:

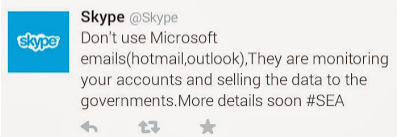
SEA’s message via Skype’s Twitter account

It’s a message you might more likely expect from Anonymous protesting against NSA surveillance and Microsoft complicity in that surveillance rather than a pro-Assad movement.
I asked SEA if it marked a change in its targets and tactics; and got this reply:
We can confirm that attack was done by us. and we gained access to important documents about monitoring accounts/emails by Microsoft.
It’s still about Syria. And we will detail that soon.
So that’s the big question now: what ties Microsoft, surveillance and Syria together?
Reckz0r’s at it again – another hack that hasn’t happened yet
Like many bloggers I watch my logs, trying to work out what appeals to readers. One thing that has continually surprised me is the popularity of a little posting I did almost 18 months ago: Reckz0r hacks MasterCard and Visa. Anonymous says no.
Reckz0r had just claimed two major hacks. Wrongly. In fact an Anonymous contact told me at the time, “He [Reckz0r] is considered the village idiot in Anonymous circles. He pretended he hacked Sony for LulzSec; he pretended he hacked sites that UGNAZI hacked. He has just faked another hack like he always does. Pure Bieber Hacker.”
But for 18 months visitors have been landing on that page. Is Reckz0r popular? I doubt it. But what it does tell me is that he is probably much better than I am at self-publicity. And now he’s at it again. This time he claims to have hacked the PS4 — well, not personally, but he almost provides a tutorial on how to implement someone else’s hack.
“Voila! JAILBROKEN!” he concludes. “You now have the ability to run unassigned/assigned code and pirated games on your PS4.” Only, naturally, the link to the actual exploit doesn’t work.
But to support his assertion he also published a Twitter conversation between himself and Sony.


Sony chastises Reckz0r, right?

Doesn’t really sound like Sony, does it? And in the first one they have very cleverly got slightly more than 140 characters into the message.
So, once again we can say with a fair degree of certainty that this is a faking hoax. But, if you’ll pardon the vernacular, it is lame. It is lame beyond even Reckz0r’s traditional lameness. It is so lame, you even have to wonder if it’s a lame joke. But that would be cleverness beyond Reckz0r — so is it even Reckz0r?
Bugger. He’s just proved the point — he really is better at self-publicity than I am.
Adobe – you really cocked-up on this one
I finally got the email I’ve been waiting for. It’s from Adobe. It starts
As we announced on 3 October 2013, we recently discovered that an attacker illegally entered our network and may have obtained access to your Adobe ID and encrypted password. We currently have no indication that there has been unauthorised activity on your account.
To prevent unauthorised access to your account, we have reset your password…
Let’s have a look at this. “We announced on 3 October 2013, we recently discovered…” What does recently mean? They announced on 3 October not because they had discovered the hack, but because Brian Krebs told the world that he had found stolen Adobe data on the internet. So when it was actually stolen (could have been months earlier) and when Adobe actually became aware of the theft (could have been months earlier) is not known.
Let’s be charitable and say Adobe knew about it by 1 October.
They said that just under 3 million usernames and encrypted passwords may have been stolen. Since I don’t have an Adobe account, and since 3 million is relatively few in the overall scheme of things, I thought no more about it.
A few weeks later Adobe admitted that the true figure is nearer 38 million. That’s getting a bit more worrying, so I checked my browser’s stored passwords and my more recently adopted password manager. Still nothing. No Adobe account. And anyway, Adobe said very clearly that the company had reset all the passwords and notified the 38 million users. I had not been notified. I had nothing to worry about.
But then, about a week later, it emerged that it wasn’t a mere 3 million, nor a more worrying 38 million, but a colossal 150 million. Adobe had notified 38 million out of 150 million – but that is by no means the worst of it. When Paul Ducklin got hold of the database of stolen data, now easily available if you know where to look, a quick analysis showed the user’s email in plaintext, an encrypted password, and the user’s password hint in plaintext.
email addresses – you can infer a lot from an address: usually the user’s name and company. For example, Ken Westin at Tripwire looked through the Adobe hack and found 89,997 military addresses. “This is in addition to the more than 6,000 accounts from defense contractors such as Raytheon, Northrup Gruman [sic], General Dynamics and BAE Systems we also found,” he wrote. “Also, on the federal side, there were 433 FBI accounts, 82 NSA accounts and 5,000 NASA accounts.” So, choose your company, guess the user’s name, look through LinkedIn and Facebook and you’ve got enough for a pretty compelling targeted phishing attack.
encrypted passwords – passwords should be hashed and salted with a slow hashing algorithm; they should not be encrypted. Hashing means 150 million passwords need to be cracked; encryption means that one key needs to be cracked and all 150 million passwords are known.
password hints in plaintext – oh, really! Why bother cracking the passwords when the hint will let you guess it? What do you think is the password when the hint is ‘57’; or ‘the bad disciple’?
So Adobe really cocked-up. They didn’t protect the data, they didn’t store it correctly, and they tried to minimise the extent of the damage. And still it gets worse; because they tried to suggest, don’t worry, most of these accounts aren’t real, they belong to people who just signed up to get promotions or freebies.
Here’s the real danger. In that great mass of one-off freebie-chasing accounts numbering anything between 38 million and 150 million are people who signed up, used a password that they can’t remember, and are completely unaware that their password is now compromised. What if these people signed up years ago before password thefts became a dime a dozen, and lazily used the same password as they use on their email address? There is no way that they can retrieve that password. They now have no way of knowing whether any or which or all of their other accounts have been compromised by Adobe’s failure to adequately protect this password.
One final point. I said at the beginning that I had been expecting the email from Adobe. That’s because I checked with LastPass (who has a little routine that will tell you whether you’re included in the hacked data) and learnt that although I couldn’t ever remember creating an Adobe account, at some point I must have done, because there I was.
So, at least six weeks after it knew of the breach, Adobe bothers to tell me that someone “may have obtained access to [my] Adobe ID and encrypted password” when the world and his dog has access to that encrypted password. I know; Ken Westin, Brian Krebs and Paul Ducklin almost certainly know; LastPass and the hackers most definitely know; and anyone who cares to look will also know. Adobe, however, doesn’t know and continues to insist that ‘an attacker… may have obtained access.”
How dare they, after all this time and all these mistakes, still try to save face at my expense?
Did GCHQ hack Belgacom? It certainly looks like it
Well, I guess that’s as official as we’re likely to get: GCHQ hacked Belgacom.
The reasoning is this…
The European Parliament’s Civil Liberties, Justice and Home Affairs committee (LIBE) is conducting a series of hearings to investigate the ‘Prism scandal’. Yesterday it held the latest in the series: “Allegations of ‘hacking’ / tapping into the Belgacom systems by intelligence services”. Statements were expected from two high-ranking Belgacom executives, and Sir Iain Lobban, director of GCHQ.
After the event, LIBE issued its statement. In full, it reads:
Civil Liberties Committee MEPs expressed their regret on Thursday that the British Government Communications Headquarters (GCHQ) had declined their invitation to take part in a hearing on the alleged hacking of Belgian telecoms firm Belgacom’s servers. Belgacom’s top managers would not confirm or deny media reports that UK intelligence services were behind the attack.
First of all I consider it grossly discourteous for Lobban to fail to attend. This committee comprises elected representatives of the people who pay his wages and on whom he spies.
And then – forgive me for being simplistic – but I have a general principle on such matters: The innocent will never say they are guilty, but can always say they are innocent. The guilty cannot admit guilt, cannot lie, and therefore say nothing.
By avoiding have to say anything, Lobban did not say he didn’t do it – therefore the huge likelihood is that he did. And as for Belgacom, by not saying it wasn’t GCHQ, the huge likelihood is that it was. It’s called the science of gut feeling; and is usually pretty accurate.
But there’s another issue here. The UK is a member of the European Union. What is the point of having a legal union if individuals can simply ignore the elected representatives of the union? And by what moral, if not legal, right does Lobban decline an interview to attend a hearing being held by one of the most important political committees in Europe?
Why do we get hacked? A combination of arrogance and denial is one reason
Have you ever wondered why we hear of a new hack every day? Well, here’s one reason – the arrogance and denial of some of our security managers.
A couple of months back I was speaking to Ilia Kolochenko, the CEO of a pentesting firm called High Tech Bridge. I asked him if pentesting was really necessary. Well, he said, just this morning I found flaws in [several high-profile media websites] that could, if cleverly exploited, lead to the complete owning of the networks concerned.
Needless to say I was interested. I asked him if he could find more, and laid down a few conditions to ensure that these weren’t old vulnerabilities that he already knew about. He delivered the goods, and the full story was published in Infosecurity Magazine: Infosecurity Exclusive: Major Media Organizations Still Vulnerable Despite High Profile Hacks.
Before publishing the story, all of the companies were notified and given a period of time to correct the flaws. Here’s a sample of the notifications:
Last week I have accidentally found an XSS vulnerability on your website that allows to steal visitors’ sensitive information (e.g. cookies or browsing history), perform phishing attacks and make many other nasty things… [details of the flaw and proof]
Please forward this information to your IT security team, so they can fix it. They may contact me in case they would need additional information and/or any assistance – I will be glad to help.
In some cases, where no vulnerability reporting address could be found, this or similar was sent to as many addresses as could be found.
Point one. Only one of the companies replied to the notification emails. This company basically said, thank you, fixed it. In reality it was only partly fixed and easily by-passed. So at the time of publishing the story, all of the websites had been contacted and given time to fix the flaw – but none of them had.
Point two. Shortly after publishing the story I received the following comments from one of the featured companies:
However try as I might I have found no-one at xyz inc who has ever heard of or from Mr Kolochenko, or yourselves, regarding any testing of our systems, vulnerabilities found, or in fact comments upon our security. Could you therefore please forward me [a copy of the several emails we had already sent].
Needless to say we did this, including an automated receipt email that proved that xyz inc had been sent and had received the email.
This head of xyz’s security then went on to accuse me of writing an advertorial for Kolochenko. He added,
…the vast majority of reported attacks on media broadcasters and press organisations so far in 2013 have had nothing to do with external attacks on websites or online presence, and the Syrian Electronic Army in particular have never used this attack vector – every one of their successful breaches has been the result of a phishing attack, which Mr Kolochenko’s tools will do nothing whatsoever to obviate.
This, of course, is both wrong and irrelevant – how the SEA’s preference for phishing (which could have been made easier by exploiting this vulnerability anyway) somehow protects xyz inc is beyond me.
The simple fact is this head of security was more concerned with deflecting any blame from himself, denying any vulnerability in his system and accusing me of lacking professional standards than in actually finding and fixing said vulnerability. A little humility and acceptance of help from security researchers might go a long way to making the internet a safer place.
Postscript. Following publication of the article, the websites in question fixed the flaws. As far xyz inc is concerned, Ilia subsequently received a further email:
We have now pushed out a fix for this vulnerability. Thanks very much for bring this to our attention.
Regards
xyz inc
To protect and serve: the police and breach notification
I sometimes wonder what is the purpose of the police: is it to protect the public or to catch criminals. The problem is that these two functions are often mutually exclusive — definitely in the short-term.
You could argue that by catching criminals you are protecting the public from their potential future crimes. You could also argue that catching this actual criminal might deter that potential criminal — and that again you are protecting the public from potential future crimes.
The weakness in this argument is that a criminal doesn’t become a criminal until after the crime is committed. By definition, catching a criminal means that you have failed to protect the public.
A clear definition of primary purpose will therefore affect basic police operations, and have a fundamental effect on the public.
Here’s an example; but it will involve a small leap of faith to begin with — I forget the precise source. I hope, however, you can trust my memory. It was a chat between two very successful hackers. One of them said words to the effect, “I watch the news because that’s how I learn when my hack has been discovered.”
Basically, that’s the time for him to get out, cover his tracks and lie low.
It follows that if there is no news of the breach, law enforcement has a greater opportunity to apprehend the criminal who might just hang around on the network long enough for the forensic investigators to gather incriminating evidence.
But at what potential cost to the public? Bill Snyder got caught up in the Vendini breach earlier this year, and wrote about it on CIO:
I got an email from Vendini on May 23 that says: “We regret to inform you that on April 25, 2013, Vendini, Inc. detected an unauthorized intrusion into its systems.” Excuse me? April 25? That’s nearly a month between the discovery of the hack and the arrival of that email, which means the bad guys had weeks to pillage my accounts, and hundreds of thousands, maybe millions, of people who have used the service. (Vendini also posted the message online.)
Why didn’t the company notify us? Says Vendini: “We are actively cooperating with federal law enforcement, and this notification to you was delayed specifically to support law enforcement’s investigation.”
Online Ticketer Vendini Hit by Hack, Warns Customers a Month Later
If this is true, it is an example of police action that prioritizes apprehension of the criminal over protection of the public. Had protection been the priority, then the breach notification would have been instant, regardless of making the potential apprehension potentially more difficult.
It’s a difficult one.
Well, actually, for me — no it is not. The absolutely prime, overriding, fundamental purpose of the police should be to protect the public. I would suggest that the loss of focus by the police — where success is now viewed as a league table of people locked up rather than the fulfillment of protecting and serving the public — is key to the increasingly macho and manipulative law enforcement agencies we now have.
A hack by any other name tastes just as bad
What is a hack? No, seriously, I need to know.
Last weekend the People/Mirror reported that Scout7 had been hacked and Manchester City’s scouting database compromised.
Scout7 came back and said it hadn’t been hacked and the integrity of its systems was sound. But City’s database was accessed by someone other than City.
Scout7 was saying that as far as its systems were concerned, it was a legal access via genuine credentials — implying that City must have lost, mislaid, or had its password stolen. It’s an interesting idea. The implication is that if you lose your house-keys and someone finds them, gets in while you’re out, and reads your personal, private diary, you haven’t been burgled.
That, of course, is emotionally absurd. But Scout7 is saying that it (the housebuilder) cannot be blamed for the burglary and doesn’t need to do anything about it. We’ll come back to that.
Meantime, how does this apply to ‘breach notification’? Is a breach a hack? Is the illegal use of legal credentials by a clear bad guy something that will require notification? Will companies be able to claim, we weren’t breached because the hackers got in through legitimate passwords, therefore we don’t need to tell anyone?
Incidentally, Kurt Wismer has an interesting story equally hinging on lack of semantic clarity: was the poor targeting in Stuxnet down to some lax manager saying , ‘make me a virus’, when he really meant, ‘make me a trojan’? Worth reading.
But back to Scout7. No, it cannot avoid its liability by implying it was a customer’s fault for losing his/her password. We all know that passwords do not provide adequate access security. So relying on them, and not adding a second factor to the access control, is effectively building something not fit for purpose. So as far as I am concerned, it got hacked.






