We’re moving and expanding!
This blog is moving (and expanding) to a full IT security news and views site (http://ITsecurity.co.uk).
Latest news on ITsecurity
But that’s all folks. If you want to keep up with the latest news and views, hop over to ITsecurity!
- Two iPhone hackers probably behind the Oleg Pliss attacks arrested in Russia
- CESG advice on securing Android in a BYOD environment
- Attacking smart TVs
- Comment spam – a growing problem
- Does the government run the spy agencies, or do the spy agencies run the government?
- The Reform Government Surveillance Nine should copy the ISPs’ methodology if they want to change government policy
- The tech giants’ letter to the Senate is just a load of fluff
- China’s response to US accusations of cyber spying
- NQ Mobile – still in the balance following Muddy Waters negative report last October
- The danger we face from the NSA’s collection of facial recognition images
- Europol, FBI, NCA and others disrupt the Gameover Zeus botnet — claim a 2 week window for users to get clean
- Mystery surrounds the fate of torrent site publichd.se
- Don’t Spy On Us – a day of action
- There is no ‘right to be forgotten’; and Google won’t forget you anyway
The new site will continue its role in challenging and disrupting the traditional view of security – but over a wider area. In particular it now has a Panel of Experts who will be contributing (when they get time from their day jobs) on a selection of specialist areas. Alphabetically, they include:
- Dr Brian Bandey – Dr Bandey’s Surgery: IP, Cloud, Big Data and e-Safety Laws Anatomised
- Alexander Hanff – CEO Think Privacy Inc: Globally respected Privacy expert
- David Harley – David Harley on malware
- Bev Robb @teksquisite –Internet security & social media consultant by stealth…
- Richard Smith – Financial skulduggery; especially of the tech variety
- Kevin Townsend – Opinions on current information security news and issues (that’s me!)
- Robin Wood – Penetration testing issues and passwords
All, except perhaps for me, are recognised world- and thought-leaders. So head over and check us out – and spread the word.
What’s with the TrueCrypt warning?
TrueCrypt, the free open source full disk encryption program favoured by many security-savvy people, including apparently Edward Snowden, is no more. Its website now redirects to its SourceForge page which starts with this message:
WARNING: Using TrueCrypt is not secure as it may contain unfixed security issues
This page exists only to help migrate existing data encrypted by TrueCrypt.
The development of TrueCrypt was ended in 5/2014 after Microsoft terminated support of Windows XP. Windows 8/7/Vista and later offer integrated support for encrypted disks and virtual disk images. Such integrated support is also available on other platforms (click here for more information). You should migrate any data encrypted by TrueCrypt to encrypted disks or virtual disk images supported on your platform.
This statement is so full of problems it is difficult to know where to start.
Is it a canary?
Canaries are warnings by a different method (if a canary died in a mine, the likelihood was that poison gas, otherwise yet undetected, was present). So one suggestion is that this message indicates government interference, and like Levison and Lavabit, it has been shut down to protect the users. (Levison said, “I have been forced to make a difficult decision: to become complicit in crimes against the American people or walk away from nearly ten years of hard work by shutting down Lavabit.”) Some have gone so far as to suggest a more explicit warning in TrueCrypt’s first paragraph: “not secure as”.
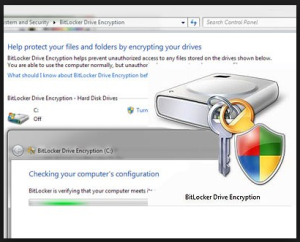
But for me the strongest suggestion that this might be a canary warning is the recommendation for Microsoft’s BitLocker. The message says “You should migrate any data encrypted by TrueCrypt to encrypted disks or virtual disk images supported on your platform.” It then proceeds to give a step-by-step how-to for migrating to BitLocker.
My problem is two-fold. Firstly, I find it difficult to believe that the developers of open-source cryptography would voluntarily recommend placing faith in a closed-source solution — and one from Microsoft to boot. Secondly, BitLocker gives up the ground won with such difficulty during the First Crypto Wars against Clinton’s Clipper chip and key escrow demands — BitLocker escrows the keys either with the IT department or with Microsoft’s cloud services. From both locations, using the PATRIOT Act, government agencies can retrieve those keys effectively on demand. This recommendation doesn’t make sense from a purely ‘security’ viewpoint.
Against this, however, we should note that ‘David’ (apparently a or the TrueCrypt developer) has told @stevebarnhart that there has been no government contact except one time inquiring about a ‘support contract’; that “BitLocker is ‘good enough’ and Windows was original ‘goal of the project’;” and that “There is no longer interest.” But whether ‘David’ is who he says he is, or whether what he says is true is anyone’s guess.
I find myself conflicted. This time my heart says, don’t think conspiracy; but my head says, this isn’t right.
What next?
For whatever reason, TrueCrypt can no longer be trusted. If we take David at face value, he has simply lost interest in the project and bowed out in a most unsatisfactory manner. That would imply that you can carry on using TrueCrypt; but that like XP, any future issues will not be resolved. So it’s probably best not to wait for them.
But if you were savvy enough to install TrueCrypt you will be savvy enough to migrate to an alternative without being persuaded into using BitLocker. BitLocker works with the Trusted Platform Module (TPM), a motherboard chip that to my mind turns Windows 8 into an NSA trojan. (See Is Windows 8 an NSA trojan?) This latest development merely reinforces my opinion.
It would be tempting to say it is time to migrate away from Windows altogether — perhaps to Linux. The reality, however, is that nothing is secure. What can be made by software can be unmade by software; that which can be built by computer power can be demolished by computer power. The unmakers have a thousand times the resources of the makers.
The solution is political, not technological. We the people have to reassert our role over the politicians. They are our servants. We pay them to do our bidding. And we have to make it absolutely clear that government interference and surveillance is unacceptable and must stop.
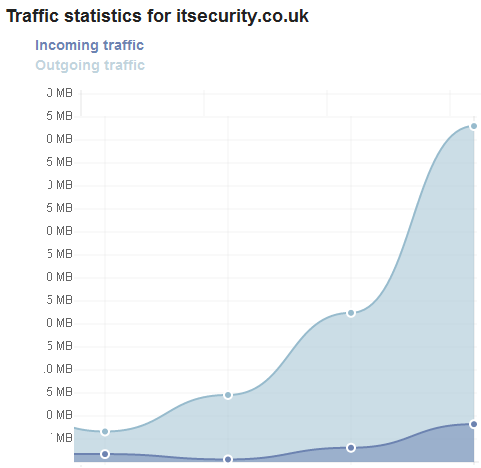
ITsecurity.co.uk went live
I guess we just went live. Traffic figures for the last four days.


Check it out. News and views from world security experts. And me.

More on the Avast breach and the hash used
My understanding is that the hash formula used by Avast to store its forum users’ passwords was
$hash = sha1(strtolower($username) . $password);
This is the formula built into the SMF open source forum software used by Avast. It is both good and bad. It confirms that the hash was salted (with the user’s username); but the use of SHA1 will raise some eyebrows. Robin Wood, a professional pentester, suggests that something like Bcrypt would have been much stronger.
Nevertheless, Wood points out, the use of the salt would make cracking much harder. “I have tables for a lot of the common hashing algorithms with just plain words (password, computer etc), but there is no way I can generate them with the salts (kevinpassword, kevincomputer, robinpassword, robincomputer).”
At a pinch, he admitted, he could generate a few tables for the most common passwords, such as root or admin or 123456. So some of the passwords could be cracked relatively easily by a sophisticated hacker, and even more could be cracked if there were world enough and time. Which is actually pretty much what Avast implied in its blog.
Again, my understanding (and you can interpret that any way you like) is that Avast is embarrassed and wishes to do the right thing. It is holding back from making a more complete formal statement simply because it is still investigating the breach — and doesn’t yet know whether it screwed up or was breached by an unknown 0-day in the SMF software.
One thing that does seem clear, however, is that the attackers were indeed sophisticated and not kiddies since the attack coincided with a multi-GBPS DOS attack. Users should therefore assume that if they used a simple password it is now known to the attackers. Those who used a strong password should assume that with time, it will also become known to the attackers. Since Avast immediately took down the forum the passwords will be of little value UNLESS the user reuses the same password elsewhere. It is for this reason that those passwords should be changed immediately; and users who do so should stop reusing passwords immediately.
So what next? In his original post, CEO Vince Steckler said that Avast will rebuild the forum and move it to a different software platform. It will be interesting to see whether the company publicise how it will store its users’ passwords on the new platform.
Avast forum hack demonstrates we need password storage disclosure
A blog post early this morning by Avast Software CEO Vince Steckler announced
The AVAST forum is currently offline and will remain so for a brief period. It was hacked over this past weekend and user nicknames, user names, email addresses and hashed (one-way encrypted) passwords were compromised.
AVAST forum offline due to attack
Avast’s reaction to this hack is in stark contrast to that of eBay’s recent reaction. While eBay said very little, Avast has quickly taken down the breached forum and contacted the users with laudable speed. And it has explained the risks.
While eBay gave no details about how its passwords were stored, Avast has indicated that they were hashed but can still be cracked. Like eBay it also lost usernames and email addresses, and that information alone is valuable to phishers. Steckler has advised users to change their passwords everywhere they have been reused — good and essential advice; but users should also be on guard against phishing attempts.
But while the Avast response has been better than eBay’s, it is still not enough — users need and deserve more. Steckler wrote,
Even though the passwords were hashed, it could be possible for a sophisticated thief to derive many of the passwords.
What does this mean; and what is a ‘sophisticated thief’? The thief was sophisticated enough to breach Avast’s defences, so we can assume he or they is sophisticated enough to use a password cracker. If he can ‘derive many of the passwords’, does that imply that a weak hashing algorithm was used, or simply that the hash was not salted? If a modern method of hashing was combined with secure salting, then it would be very difficult to derive the passwords.
Users deserve to know how their passwords are protected. This can only be done before the event, because once a breach has happened, the natural inclination of all companies is to minimize any blame on themselves. While the European Union is discussing mandatory breach disclosure as part of the General Data Protection Regulation, it simply does not go far enough. All companies that store user passwords should be obliged to publicly disclose how those passwords are stored and protected.
This will not help the thief. Once he has obtained the passwords, he will rapidly discover that information for himself. It will, however, help the user. The user can decide whether to trust the company before sign up; and will know how much to worry after a breach.
More to the point, however, is that security experts will publicly deride any company without good security — and that alone will force them to do better.
Hector ‘Sabu’ Monsegur to be sentenced while Hammond sits in prison
A common cry in Anonymous circles is ‘Free Jeremy Hammond; Fuck Sabu’. Jeremy Hammond is currently serving a ten-year prison sentence for his involvement in the Stratfor hack. Sabu (real name Hector Xavier Monsegur) will be sentenced tomorrow for his role in Lulzsec and many other hacks. He is expected, on FBI request, to walk free. The judge, in both cases, was and is judge Loretta Preska. Comparing and contrasting the behaviour of Hammond and Monsegur explains the Anonymous cry.

Sabu
Monsegur was the original founder of the original LulzSec hacking group, (in)famous for its ’50 days of lulz’ during the summer of 2011. Sabu was ‘outed’ and subsequently interviewed by the FBI. He rapidly (by the next day) agreed to cooperate; and has been cooperating ever since. There is some suggestion that the FBI pointed out that his two young nieces, for whom he is a foster parent, would have an uncertain future if he was incarcerated.
The extent of that cooperation is only just becoming clear, although it was always known to be extensive. Some of it borders on illegality, but is certainly immoral. The Stratfor hack was organized by Sabu at the behest of the FBI in order to entrap Jeremy Hammond – a member of Anonymous rather than Lulzsec but high, on the list of the FBI’s most wanted. It worked. It also, incidentally, ensnared Barret Brown who was arrested effectively for publishing a link to stolen Stratfor information; although his charges have now largely been dropped.
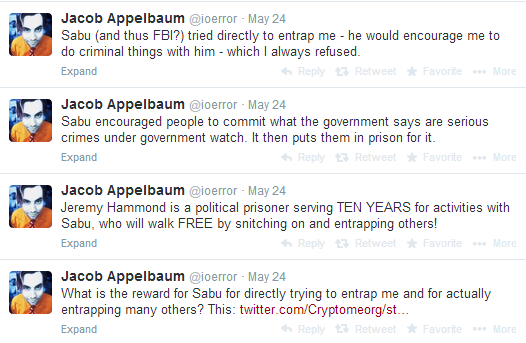
Sabu’s cooperation also led to the unmasking and arrest of the other members of LulzSec: 2 in the UK, 2 in Ireland and one in the US. It seems clear that he also tried to implicate and entrap many others; including, for example, Jacob Appelbaum.


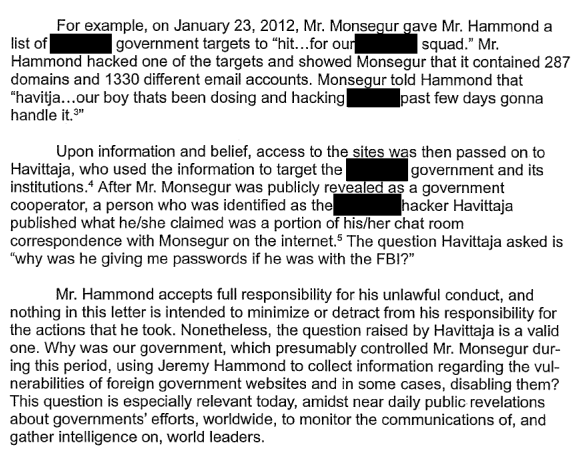
He also cooperated with the government, using Hammond, to enable it to hack foreign websites. Hammond’s attorneys wrote to judge Preska last month:


Hammond’s own behaviour has been in direct contrast. After his arrest he decided to fight the charges. Eventually, however, he gave up and accepted a plea deal with the government. Almost exactly one year ago he announced,
Today I pleaded guilty to one count of violating the Computer Fraud and Abuse Act. This was a very difficult decision. I hope this statement will explain my reasoning. I believe in the power of the truth. In keeping with that, I do not want to hide what I did or to shy away from my actions. This non-cooperating plea agreement frees me to tell the world what I did and why, without exposing any tactics or information to the government and without jeopardizing the lives and well-being of other activists on and offline.
Statement from Jeremy Hammond regarding his plea

Jeremy Hammond
(Associated Press)
His reasoning was not that he thought he would lose the case, but that the FBI would simply press similar charges elsewhere. “The process might have repeated indefinitely,” he said.
I have already spent 15 months in prison. For several weeks of that time I have been held in solitary confinement. I have been denied visits and phone calls with my family and friends. This plea agreement spares me, my family, and my community a repeat of this grinding process.
The key sentence in this announcement is, “This non-cooperating plea agreement frees me to tell the world what I did and why, without exposing any tactics or information to the government and without jeopardizing the lives and well-being of other activists on and offline.” So while Sabu cooperated with the FBI and will most likely walk free tomorrow, Hammond refused to cooperate and took a ten-year sentence. That, basically, is why the call is ‘Free Jeremy Hammond; Fuck Sabu.’
Tomorrow, 27th May 2014 at 11 am, Judge Preska will pronounce sentence on Sabu. In theory he faces a sentence of between 259 and 317 months for the crimes he as admitted. But, says the FBI in its pre-sentencing submission to Judge Preska,
Probation recommends a sentence of time served. As set forth in more detail below, Monsegur was an extremely valuable and productive cooperator.
Government’s notice of intent reference sentencing
He has, during the three years of his cooperation with the FBI, served seven months in prison. Judge Preska is expected to follow the FBI request and sentence him to seven months – allowing him to walk free.
We will update this post tomorrow with details of judge Preska’s sentence.
Update
The much delayed sentencing of former LulzSec hacker-turned-FBI informant Hector “Sabu” Monsegur finally took place on Tuesday, when he received time served plus one year of supervised release with computer logging.
Ars Technica
The eBay hack, the loss of 140 million records, and the PR fiasco
There are two functions to PR: the first is to shout the good news from the hilltops, while the second is to bury the bad. When bad news hits, PR says very little.
Bad news has hit eBay. It admitted Wednesday that it had been hacked – but it actually gives very little information. This is a mistake. It means that people will comb their words used looking for clues over what has actually happened. The result is conjecture; but what follows is the conjecture of some very clever security people.
Three things leap out from the eBay statement. The first is the repeated use of the word ‘encrypted’, with no mention of hashing for the passwords. The second is the duration of the breach – it occurred in February/March, but was only discovered a couple of weeks ago. And the third is the mention of the database – not part of, nor a geographical region, but the (whole?) database. So what can we surmise from all this?

Ian Pratt, co-founder of Bromium
Firstly, were the passwords encrypted or hashed? It makes a difference. The implication from the statement is that they were encrypted. Most security experts believe that this would be a mistake – passwords should be hashed and salted. In fact, Ian Pratt, co-founder of Bromium, goes so far as to suggest, “It would be rather unusual to encrypt passwords rather than hash them; it’s probably just lack of precision in the statement.”
But that’s what we said about the Adobe breach – and it turned out that the passwords were indeed encrypted rather than hashed. The opinion among the experts I talked to is fairly evenly balanced – while eBay’s semantics suggest they used encryption, many experts find it hard to believe. “This heavily implies that the passwords were not hashed,” said Chris Oakley, principle security consultant at Nettitude. “eBay’s report suggests that the passwords were encrypted rather than hashed,” added Brendan Rizzo, Technical Director EMEA for Voltage Security. Sati Bains, COO of Sestus, said, “Yes… it appears from the comment that they did [encrypt rather than hash].”
“Encryption and hashing are often confused with each other,” explains Jon French, a security analyst at AppRiver. “But from the sounds of the [eBay’s] press release, it seems they were using some sort of encryption.”
Andrey Dulkin, senior director of cyber innovation at CyberArk, is in no doubt. “Indeed, from the eBay statements we understand that the passwords were encrypted, rather than hashed. The fact that the statements repeatedly use the words ‘encrypted’ and ‘decrypted’ supports this interpretation.”
It is, of course, possible that eBay is simply not differentiating between the two processes, since most of its customers will not understand the difference. “The public understand the word ‘encrypted’ more than hashed – so encrypt is frequently used in place of hashed. But it is believed they were hashed,” suggests Guy Bunker, spokesperson for the Jericho Forum and a cyber security expert at Clearswift.
Ilia Kolochenko, founder and CEO of High-Tech Bridge (HTB), doesn’t believe we can tell from eBay’s comments. “The difference isn’t easily understood by users. Even the spokesperson might not be aware. It’s quite possible that the company simply didn’t want to introduce the complexity of describing the technicalities of hashing and salting in a brief announcement.”
What’s the difference, and why does it matter?
The primary operational difference is that encryption can be decrypted; that is the original plaintext can be retrieved from the ciphertext through the use of the encryption key. Hashed outputs cannot be mathematically returned to the original plaintext.
In practice, an entire database of passwords would be encrypted via a single encryption key. But if hashing was used, each individual password would ideally have an unknown value added to it (a ‘salt’) and the results would be separately hashed. “This salt,” explains Voltage’s Rizzo, “is a way to make sure that the hash of a particular password cannot be compared to the known hash of that same password by the attacker through the use of rainbow tables.”
This means that if an encrypted database is stolen, only one key needs to be found to unlock every password in the database.If the passwords are hashed, every single password needs to be cracked individually.
“The advantages to hashing,” Nick Piagentini, senior solutions architect at CloudPassage, told me, “are one, there is no need to manage sensitive encryption keys; two, hashing processes have less overhead to run than encryption processes; and three, there is no need to reconstruct the password data from the hash. Encryption would only be used if there was a need to get the original password back.”
Could the hackers have the encryption key?
This is the 64 million dollar question (and is only relevant if the passwords were encrypted). We don’t know, and we may never know. But it is certainly possible. There are two possibilities: it could have been cracked or it could have been stolen.
Reuters spoke to eBay spokeswoman Amanda Miller:
She said the hackers gained access to 145 million records of which they copied “a large part”. Those records contained passwords as well as email addresses, birth dates, mailing addresses and other personal information, but not financial data such as credit card numbers.
Hackers raid eBay in historic breach, access 145 million records
eBay says the database was compromised some time around late February or early March; but wasn’t discovered until about two weeks ago. What we don’t know is whether the compromise was still in active use by the hackers, what else they did during the two months they were undetected, or whether they left something unwelcome behind. Frankly, I find it hard to believe that having gained access without being discovered the hackers did not have a good look round.

Chris Oakley, principle security consultant at Nettitude
(Incidentally, it is worth pointing out at this point another comment from HTB’s Kolochenko. Basically, eBay’s statement that financial details were safely stored on a separate server is pretty meaningless. “The two servers would have to communicate,” he explained. “The hackers could have installed some malware to listen to the communication between the servers, and sniffed the plaintext traveling between them.”)
So could they have found the encryption key? Opinion is divided. “This is a primary argument for using hashing over encryption for password storage,” comments Nettitude’s Oakley; “an attacker who is able to compromise the database may also be in a position to obtain the encryption key(s).” (Incidentally, if the passwords were hashed rather than encrypted, the hackers could just as likely have found the salt or salt mechanism, rendering the hashed passwords relatively easy to crack via rainbow tables.)
On the other hand, “I would hope they [eBay] didn’t ‘tape the key to the door of the safe’”, comments Trey Ford, global security strategist at Rapid7. “eBay and PayPal have solid security teams, and go through regular third-party assessments. I refuse to believe they would handle encryption key materials that poorly.”
And yet they left the users’ email addresses and other personal information unencrypted. If they were using encryption seriously, they would have used a hardware security module (HSM) to house the keys, and would have encrypted everything. “They do not seem to be very confident about their encryption system,” comments Sebastian Munoz, CEO of REALSEC, “when they are suggesting their customers to reset passwords. If efficiently encrypted, using specific certified hardware, there would be no need to reset the passwords, since protection is guaranteed. When you use a Hardware Security Module (HSM) and not a simple and insecure encryption-by-software process, there is no way that hackers can gain access to the encryption keys.”
Munoz further suspects that software based encryption was used since only the passwords were encrypted. Since software encryption impacts on performance, then cost arguments come into play.

Sebastian Munoz, CEO of REALSEC
So, given the duration of the breach and the probable lack of an HSM, it is perfectly possible that the hackers also found the encryption key – and if this is the case, they now have access to all of the greater part of 145 million passwords, along with ‘email address, physical address, phone number and date of birth’.
If they did not find the key, would they be able to crack the encryption key? Again, opinion is divided – it all depends upon what encryption algorithm was used. Older encryption algorithms might be susceptible to a ‘known plaintext’ attack (see Wikipedia for details). Getting the necessary plaintext would be no problem. The most popular passwords are remarkable consistent – so a simple analysis with something like DigiNinja’s Pipal on an existing cracked database would provide a fair sampling of plaintext.
“However,” notes Bromium’s Ian Pratt, “assuming any kind of modern encryption (e.g. AES-128) was used then a known plaintext attack should not be feasible to recover the key and hence reveal other passwords.”
“Another approach,” suggested Clearswift’s Bunker, “is to ‘inject’ known passwords (either the hash or the encrypted version) into the database. This would create the equivalent of denial of service for the individual but would allow the attacker free reign over the account.”
The problem is we simply do not know what has happened. eBay’s attempts to downplay the incident is simply leading to conjecture.
UPDATE
While writing this report, Rapid7’s Trey Ford noticed adverts for the sale of eBay’s stolen database beginning to appear on Pastebin. “There has now been a posting on pastebin claiming to offer ‘145 312 663 unique records’ relating to the eBay breach,” he told me by email. We don’t know if they’re genuine, “it’s possible that a criminal has just spotted an opportunity to cash in on the attack with some other credentials dump they have.”
An analysis of the sample provided is inconclusive – the records are possibly genuine but not certainly genuine. But Ford had a look at the sample:
The sample that has been shared indicates that cracking the passwords will take considerable time. This is nothing like what we saw when LinkedIn was breached and the stolen credentials were quickly cracked due to only SHA-1 hashing being used for storage. In contrast, this credentials set is using PBKDF2 (Password-Based Key Derivation Function 2) SHA-256 hashes, which means they employ a strong hash function and also intentionally make cracking them more difficult and slow by individually salting and using a high number of hash iterations. The method used can be regarded as the state-of-the-art way to store passwords on web applications. Again though, we don’t know that these are credentials taken from the eBay breach, and no details have come from eBay on how they secure passwords.
This would fit in with eBay’s apparent confidence that the passwords cannot be hacked. However, Reuters spoke to eBay about the sample, and
eBay’s [spokesperson Amanda] Miller said the information was not authentic.
U.S. states probe eBay cyber attack as customers complain
AppRiver’s Jon French also noticed the Pastebin offer. He told me by email,
I’ll be wary of anything like this until I see people saying they see their own names (or if I end up seeing mine). Eventually if the Pastebin offer is legit, someone will post the file for free somewhere or some security company that buys it will verify authenticity.
His colleague, Troy Gill, a senior security analyst at AppRiver also suggested something that serious criminals will be well aware of: “There is always the remote possibility that this is a honey pot set by authorities to lure in would be buyers.”
Summary
eBay is taking the standard route for crisis management: say nothing. This is hugely disrespectful to its customers, who need and have a right to know everything possible. But eBay is also making a mistake in trying to downplay the effect of the stolen data. It says it has “no evidence of the compromise resulting in unauthorized activity for eBay users, and no evidence of any unauthorized access to financial or credit card information.” This is meant to make its customers feel better – the danger is that it might.
What eBay isn’t saying is that the unencrypted personal data also stolen (email address, physical address, phone number and date of birth) is a phisher’s wet dream. Armed with that information criminals will be able to concoct very compelling emails and cold call telephone calls. This is likely to happen on a vast scale and very soon. eBay might feel confidant about its own business, but the data it has lost puts millions of individuals and other companies in danger.
“When companies like eBay keep silent about the details,” commented High-Tech Bridge’s Kolochenko, “I would tend to expect the worst.” It is perhaps worth remembering the Adobe incident, which started off with a breach of a couple of million and slowly escalated into one of the worst breaches in history.
The Master Troll, Weev, delivers a masterpiece of trolling

Andrew Weev Auernheimer
It is always a pleasure to see a master at work; and Andrew Weev Auernheimer is not known as a master Troll without good reason. He was arrested, charged with hacking AT&T, sentenced to three years in prison, and eventually released after the case against him was thrown out on appeal. See here for background.
Now he has written to the government and delivered an invoice for the time he spent assisting the FBI. His open letter is full of gems.
His basic argument is that he is entitled to recompense, and that the best way to calculate this would be on his hourly freelance rate. The genius is that while the overall is absurd, the individual elements are all plausible and logical.
I have, over the course of 3 years, been made the victim of a criminal conspiracy by those in the federal government. This was a conspiracy of sedition and treason, perpetrated with violence by a limited number of federal agents to deprive me of my constitutional rights to a fair trial and unlawfully put me in prison.
Each element of that statement is morally if not legally defensible — even the sedition and treason.
Sedition is the charge for crimes which undermine the Constitution with violence. I can assure you that violence was used against me, and the Third Circuit Court of Appeals has already verified that the case against me undermined the Constitution.
Treason is less easily defined, and is not specifically defined by Weev. Nevertheless, it is generally accepted to be an attack against the state by a member of that state — and an attack against the US Constitution can be considered an attack against the state. The appeal court, in dismissing the case, wrote
As we progress technologically, we must remain mindful that cybercrimes do not happen in some metaphysical location that justifies disregarding constitutional limits on venue.
Court of Appeals vacating Weev’s conviction
The implication is that by disregarding the constitutional limits, the FBI attacked the constitution — ergo, treason.
Having made his case, Weev then seeks restitution.
I was taken from my childhood home at gunpoint on January 18th, 2011, and I was not allowed to freely exercise my liberties as a citizen until April 11th, 2014. That’s 1179 days that you used my time that I am now billing you for (I gave you a discount by not including the last day).
The real gem in the whole letter, however, is that he demands payment in bitcoins.
I am owed 28,296 Bitcoins. I do not accept United States dollars, as it is the preferred currency of criminal organizations such as the FBI, DOJ, ATF, and Federal Reserve and I do not assist criminal racketeering enterprises.
This is a masterclass in trolling from a Master Troll. The tragedy for society in the United States is that it is perfectly correct.
Now the government’s answer, or lack of it, will be permanently preserved in the Bitcoin block chain as a matter of public record. PAY ME MY MONEY, YOU LYING SUBHUMAN GARBAGE. You also should resign from your posts, as you’ve shown yourselves to be collective disgraces to rule of law and enemies of the United States Constitution. Those of us who actually love this country should take your places.
A more reasoned argument coming to a similar conclusion was published by Chris Hedges earlier this month:
The government, by ignoring the rights and needs of ordinary citizens, is jeopardizing its legitimacy. This is dangerous. When a citizenry no longer feels that it can find justice within the organs of power, when it feels that the organs of power are the enemies of freedom and economic advancement, it makes war on those organs. Those of us who are condemned as radicals, idealists and dreamers call for basic reforms that, if enacted, will make peaceful reform possible. But corporate capitalists, now unchecked by state power and dismissive of the popular will, do not see the fires they are igniting.
The Post-Constitutional Era
FBI indicts five members of the Chinese military for hacking US companies
Eric Holder yesterday announced: “Today, we are announcing an indictment against five officers of the Chinese People’s Liberation Army for serious cybersecurity breaches against six American victim entities.”


The five Chinese military men wanted by the FBI

The five officers are known by the aliases UglyGorilla, Jack Sun, Lao Wen, hzy_1hx and KandyGoo. They are members of the PLA’s military unit 61398 (you may recall that this is the unit accused by Mandiant last year as being the source of the APT1 hacking group). They stand accused of using spearphishing to penetrate six US companies (Westinghouse Electric, Alcoa, Allegheny Technologies Incorporated, U.S. Steel, the United Steelworkers Union and SolarWorld) to conduct economic espionage.
“This is a tactic that the U.S. government categorically denounces,” said Holder. “As President Obama has said on numerous occasions, we do not collect intelligence to provide a competitive advantage to U.S. companies, or U.S. commercial sectors.” This is from the man who lied to Congress.
It is also inaccurate. The Snowden files have shown that the NSA has bugged trade negotiations; and trade negotiations are quite plainly ‘economic’ – with US industry likely to benefit. And of course the NSA’s hacking of Chinese servers, and excluding Huawei over fears that it might be backdoored while it proceeded to backdoor Cisco equipment has sort of ceded the moral high ground.
I asked FireEye, which now owns Mandiant, if it had supplied any of the information used by the FBI in its indictment. A spokesperson told me, “The US government just used information from the APT1 report which was published. We did not actively provide information. We believe this was a natural escalation after the revelation – the PLA group went quiet but now are very active again so was only a matter of time.”
But there may be another reason for the delay between Mandiant’s initial report and this indictment… Generally speaking, law enforcement needs a victim complaint over intelligence of a crime before it can take action against the suspected criminal; so it has had to wait for the hacked companies to investigate and complain before it could commence the indictment proceedings.
Luis Corrons, technical director at PandaLabs, finds this a frequent problem. “This year I have handed LEA information about 3 different criminal cases; and all 3 of them have real evidence of who is behind them. But if there is no official complaint from the victims, nothing happens. One of the cases is multinational – the local LE tried to convince a Spanish company who was victim to present a complaint, but it didn’t want to. Now the LEA is trying in different countries trying to convince victims to present a complaint.
“But this is not the only problem,” he continued.” Some investigations are really complex, and while for me it can be ‘easy’ to gather evidences, for an LEA to do it in the proper and legal way can take months or even years.”
If that’s the case here, this indictment is actually quite speedy.
But is it wise?
Much of the security industry is in favour of the US action. “This really could be a landmark moment that has the potential to change the way in which we respond to the growing threat presented by digital criminality,” said Martin Sutherland, managing director of BAE Systems Applied Intelligence, in an emailed statement. “This current case is encouraging and sets an interesting precedent for other countries combating digital crime.”
“The US government is toughening up its language against nation-state and industrial cyber-espionage,” said Bob West, chief trust officer at CipherCloud in another email. “We’re calling out the Chinese government for its role fostering theft of American intellectual property and doing it by naming specific hackers with military ties.”
“While I doubt that foreign military commanders who are prosecuted by the Department of Justice will be successfully apprehended and brought to justice,” said Tom Cross, director of security research at Lancope, “these prosecutions do send a clear message regarding what sort of behavior the United States views as unacceptable.”
In each case I asked a few questions. Most pertinent was this:
Is it not pure hypocrisy? We know from the Snowden files that the NSA has hacked Chinese servers. Holder says ‘we do not do it for economic advantage’. Leaving aside any cynicism over such a statement, isn’t it irrelevant? Holder is saying that the accused have broken US laws; but the US breaks Chinese laws. So what is the legal difference?
I have not had a reply. In fairness, it probably has as much to do with trans-Atlantic time zones as a disinclination to respond; and I will update this post with any replies that I get.
However, it is the problem I have with the US action. It is a nation that claims to uphold the rule of law – but only the rule of US law. This action says to the world, you must all abide by our laws, but our laws are the only ones that we need abide by.
Worldwide crackdown on BlackShades RAT users
First official indications emerged at the Reuters Cybersecurity Summit (although there have been rumblings in hacker circles for a couple of weeks now). This was last Wednesday. The FBI executive assistant director Robert Anderson, appointed in March to oversee ‘all FBI criminal and cyber investigations worldwide, international operations, critical incident response, and victim assistance’, announced:
There is a philosophy change. If you are going to attack Americans, we are going to hold you accountable. If we can reach out and touch you, we are going to reach out and touch you.
Within days it emerged that the FBI is reaching out to touch buyers and users of the BlackShades remote access trojan — not just the FBI, but law enforcement agencies around the world. It was officially a two-day operation involving the law enforcement and judicial agencies of more ten different countries, coordinated in Europe out of Eurojust with representatives from Eurojust, Europol’s EC3 and the FBI present.
To put the size of the operation in context, action took place in the Netherlands, Belgium, France, Germany, UK, Finland, Austria, Estonia, Denmark, USA, Canada, Chile, Croatia and Italy. 359 house searches were undertaken; over 1,100 data storage devices were seized; and 97 arrests have been made. Seventeen arrests were in the UK.
BlackShades is a remote administration tool; but coupled with malware it becomes a remote access trojan. It can be bought on the internet for anything between £40 and £100 depending on the variant purchased. Although there is (at the time of writing this) no official confirmation of any arrests in the US, the FBI’s influence is clear throughout. Indeed, the UK’s National Crime Agency (NCA) specifically describes the operation as ‘initiated by the FBI’. And noticeably, the bshades.eu website has been seized by the FBI.


There is little doubt that BlackShades is a serious threat. The NCA suspects that its UK users may have stolen 200,000 user names and passwords around the world. Nevertheless, it is simply not as well known, nor has done the same amount of damage, as some of the other well-known malwares. So why chose BlackShades rather than, for example, Zeus?
“I suspect,” David Harley, senior research fellow with ESET told me, “that BlackShades – and, maybe more to the point, its users – constituted a relatively easy target because it had operated within an area seen as legally ‘grey’. It looks to me as if those involved were often less scrupulous about covering their tracks than the career criminals associated with more heavyweight malware. It could be that they see themselves as borderline legal or at any rate of less interest to law enforcement, despite their association with the somewhat notorious Cool Exploit kit.”
The ‘grey area’ is that a remote administration tool is not illegal; it is only when it is used as a remote access trojan that it becomes so. Consider this, for example, from a German BlackShades user highlighted by Rickey Gevers:
Click it for full size. The author writes, “Hey guys, guess what happened today.” He had a visit from the German police who took away his computer because it contains BlackShades.
But he’s not worried because he only used it for testing purposes on his own computers — that is, as a remote administration tool.
But the other point to note is the date and his reference to rumours going on for days or weeks. It would seem that this operation has been going on for longer — and is probably a lot wider — than the official announcements so far. And remember also that we have not yet heard of any US arrests.
Last word goes to Rickey Gevers:
If all the above is true we are just seeing the tip of the iceberg. And are probably being witness of one of the biggest international raids ever related to cybercrime.