Archive
Stick it to the Man!
If you like this blog; or even if you just like the idea of this blog but dislike me – vote for it.
It’s independent. It has no external funding, no support from any company and owes allegiance to no-one. It’s just me and my cynicism.
I need your support. Vote for this blog: ‘most entertaining security blog’. But do it now, because voting closes tomorrow.
Vote here: http://www.ashimmy.com/2014/01/2014-social-security-blogger-award-voting-is-now-open.html
PrisonLocker + CryptoLocker = PowerLocker
This is a bit worrying:


Nothing, but nothing, can guarantee security!

Guaranteeing security merely means you’re clueless and dangerous. But it’s indicative of the panic around CryptoLocker.
Panic, of course, is a universal life force – it gives living energy to any inanimate object. When you add panic to any story, it gains a life of its own; it grows legs and runs.
Panic has now been added to PrisonLocker (AKA PowerLocker), a new encrypting malware being readied for release by a guy called gyx.
But if you read the original and excellent expose published last week by Malware Must Die, you cannot help but have a few questions. For example, each new announcement says release is imminent, but each new announcement doesn’t seem to bring it any closer.
Nor does the author sound much like the traditional hacker. His command of the written language is pretty good. There are relatively few typos or howling grammatical errors and the syntax is Anglo-Saxon – he’s probably British, or at least not American. He reads like a native English speaker. He spells ‘behaviour’ with a ‘u’ (an American or someone brought up on American-English would not), he writes created by the group “Romanian Antisec”. with the fullstop outside of the quotation marks (an American would put it inside).

Fraser Howard, Sophos
So with a few questions of my own, I spoke to Fraser Howard, a security researcher with Sophos. He too was a little puzzled.
“Typically,” he explained, “ransomware falls into one of two camps. The first simply locks the user out; but data and files are not normally modified or encrypted. This is easy to deal with – once the malware is removed, the user is back to normal. It’s more of an annoyance than anything else, scaring the user into paying up.
“The second encrypts the users’ files. The ‘serious’ ransomware families do this, using cryptography correctly to securely encrypt files without leaving the key anywhere accessible. PowerLocker,” he added, “claims to do both lockout and encrypt.”
This is one of the things that puzzles him: why have both? “Seems a bit daft to me – why bother locking them out if you have encrypted their data? The author claims: ‘Even if the user is able to somehow get out of locker screen, files will still be encrypted with practically unbreakable encryption.’
Well, that’s just flawed, illogical thinking.
“It makes me suspicious – it’s indecisive. When I read claims like this, it makes me wonder if the author is actually very capable.” But that’s not all. “Some of the text in the other screenshots [from the Malware Must Die report] make me suspect the author’s skills. Talk about ‘UAC bypass’ and ‘admin privileges’ – well, that’s all very basic stuff used by most malware today.”
My guess is that PrisonLocker was originally intended to be purely locking ransomware. Given the success and publicity surrounding CryptoLocker, gyx decided to add encryption. Not wishing to abandon what he’d already done, he kept the original locking mechanism. But with encryption now perceived as the primary sales incentive, the ‘prison’ epithet was no longer adequate, so he changed the name to ‘power’ locker (crypto locker already being taken).
But there’s one other thing we could consider. gyx is suggesting a purchase price of $100 for his malware. Firstly, he doesn’t seem intent on using it himself. Secondly, that’s remarkably cheap – unless, of course, it’s a ‘loss-leader’ being used to break into a new market.
And that, frankly, is what it seems like to me. A competent and well-educated coder has turned to the dark side, and is using this ‘project’ to get in. He understands software, but he doesn’t necessarily understand malware nor the malware marketplace. He’s selling it rather than planning to use it himself in order to stay one remove from the hacking, infecting and stealing side of malware – he sees himself more as an underworld manager than an underworld foot-soldier.
But saying all that, if PowerLocker is as good (or as bad) as he describes, then it is going to be a dangerous piece of malware. If it’s taken up by some of the better organised criminal groups with access to 0-day exploits, or simply experienced in the use of exploit kits like Magnitude, then PowerLocker could easily become the next PanicLocker.
The NHS wants to store and sell your health records
Some time this month, if you live in Britain, you will receive a leaflet from the NHS. Its purpose is to persuade you that a new central database of all your health information (more or less everything your doctor knows about you, has said to you, has prescribed for you, or advised you on) held and operated by the government, is a good thing. It is not a good thing, and the leaflet does not tell you all you need to know about the database.


It is not a good thing.
Ross Anderson has provided an alternative leaflet providing more of the information that we should all be told. His leaflet provides a cut-out form that we can use to instruct our GP not to give any of our health data to the central database. We can do this. That’s the law. It’s in the Data Protection Act. If we do not do so, our health records will be uploaded automatically and we will not be able to get them removed. I suggest every Brit should read Anderson’s leaflet as well as the NHS leaflet; and I urge everyone to instruct their GP to block the upload.


Why do we need to object?
The data held will not be anonymised. It cannot be, because they want to marry our GP records with any records from hospital visits. That data will then be sold to third parties. The biggest buyers will be the pharmaceutical companies, either directly or disguised as research establishments or subcontracted to universities. By default, that data will not be anonymised.
They say we can insist on our own records being anonymised before sale. That is meaningless, irrelevant and impossible.
Raw medical records will not help in the development of new treatments or drugs. But it will help in targeting existing drugs. It will show relationships both geographically and socially between treatments and success or failure rates. It will, in short, enable the drug companies to target specific groups of patients or geographical areas with their existing drugs.
That will be the primary use of this database by the pharmaceutical companies – to locate targets and develop marketing strategies for their existing products.
Do not believe anything said to the contrary: this is what will happen.
What ties Microsoft, surveillance, Syria and the Syrian Electronic Army together?
The Syrian Electronic Army (SEA) yesterday hacked Skype’s WordPress and Twitter accounts. The likelihood is that the pro-Syrian group got hold of the password used by Skype’s media people, probably through its usual method of spear-phishing. My report on the incident for Infosecurity Magazine is here.
But this hack was a little different to SEA’s normal escapades. The group’s whole raison d’être is to deliver pro-Assad messages to counter what it believes is anti-Assad propaganda controlled and delivered by western governments. This is the reason that it has concentrated on attacking high-profile media companies.
Well, Skype is certainly high-profile — but the message is not ‘Syrian’. On both the Skype Twitter account and its WordPress blog the SEA message was this:

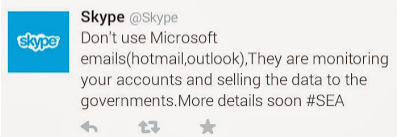
SEA’s message via Skype’s Twitter account

It’s a message you might more likely expect from Anonymous protesting against NSA surveillance and Microsoft complicity in that surveillance rather than a pro-Assad movement.
I asked SEA if it marked a change in its targets and tactics; and got this reply:
We can confirm that attack was done by us. and we gained access to important documents about monitoring accounts/emails by Microsoft.
It’s still about Syria. And we will detail that soon.
So that’s the big question now: what ties Microsoft, surveillance and Syria together?
An evolution in the theory of security risk management
Time to rewrite the text books. We have ‘security by threat transfer’, ‘security by threat avoidance’, ‘security by threat reduction’, and ‘security by threat acceptance’.
Now I bring you the latest evolution in the theory of security risk management: security by denial…

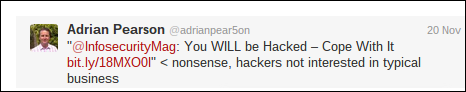

This, ladies and gentlemen, is why we have a problem.
Trust and the Internet
Wonderful idea from Deutsche Telekom. Yesterday it said it would launch a clean pipe secure service for small companies that cannot afford their own security. For a fixed monthly fee small companies will be able to access the internet via DT’s own secure data centres. “Hackers will have no chance,” said management board member Reinhard Clemens. Well, we’ll just gloss over that, and accept it at face value.
“The ‘clean pipe’ project, in which Deutsche Telekom partners with RSA – part of U.S. technology firm EMC – is in a test phase and scheduled to hit the market early next year,” reports Reuters.
So, just a little due diligence required before I sign up…
OK, Deutsche Telekom owns T-Mobile. T-Mobile “operates the fourth and fifth largest wireless networks in the U.S. market with 45 million customers and annual revenues of $21.35 billion.” (Wikipedia). Slight problem; that means that T-Mobile is subject to FISA in the US – and the US gets DT more than $20 billion.
OK, RSA is a huge name in encryption. That’s got to be good (even though it is, well, yes, an American company). RSA got big and very rich on its invention of public key cryptography. Thing is, RSA didn’t invent it – it was invented by Ellis, Cocks and Williamson at GCHQ.
Now the details are rather obscure and still shrouded in secrecy, but there are suggestions that GCHQ told the NSA what it had discovered, and shortly after that, public key cryptography was (re)invented in the US.
I would not for one moment suggest anything underhand in the timing – but given what we now know about both the NSA and GCHQ there is a temptation to ask whether public key cryptography would have been allowed to develop if the very same mathematicians who produced it had not also discovered a way to unpick it.
Mathematicians and cryptographers tell us that cryptography based on the difficulty in factoring large nearly primes is valid.
But…
And that’s the point. But.
Thank you NSA. Thank you GCHQ. You have reduced a wonderful and exciting internet into something dirty and distrustful. Thank you for removing any possibility of trust anywhere.
Why do we get hacked? A combination of arrogance and denial is one reason
Have you ever wondered why we hear of a new hack every day? Well, here’s one reason – the arrogance and denial of some of our security managers.
A couple of months back I was speaking to Ilia Kolochenko, the CEO of a pentesting firm called High Tech Bridge. I asked him if pentesting was really necessary. Well, he said, just this morning I found flaws in [several high-profile media websites] that could, if cleverly exploited, lead to the complete owning of the networks concerned.
Needless to say I was interested. I asked him if he could find more, and laid down a few conditions to ensure that these weren’t old vulnerabilities that he already knew about. He delivered the goods, and the full story was published in Infosecurity Magazine: Infosecurity Exclusive: Major Media Organizations Still Vulnerable Despite High Profile Hacks.
Before publishing the story, all of the companies were notified and given a period of time to correct the flaws. Here’s a sample of the notifications:
Last week I have accidentally found an XSS vulnerability on your website that allows to steal visitors’ sensitive information (e.g. cookies or browsing history), perform phishing attacks and make many other nasty things… [details of the flaw and proof]
Please forward this information to your IT security team, so they can fix it. They may contact me in case they would need additional information and/or any assistance – I will be glad to help.
In some cases, where no vulnerability reporting address could be found, this or similar was sent to as many addresses as could be found.
Point one. Only one of the companies replied to the notification emails. This company basically said, thank you, fixed it. In reality it was only partly fixed and easily by-passed. So at the time of publishing the story, all of the websites had been contacted and given time to fix the flaw – but none of them had.
Point two. Shortly after publishing the story I received the following comments from one of the featured companies:
However try as I might I have found no-one at xyz inc who has ever heard of or from Mr Kolochenko, or yourselves, regarding any testing of our systems, vulnerabilities found, or in fact comments upon our security. Could you therefore please forward me [a copy of the several emails we had already sent].
Needless to say we did this, including an automated receipt email that proved that xyz inc had been sent and had received the email.
This head of xyz’s security then went on to accuse me of writing an advertorial for Kolochenko. He added,
…the vast majority of reported attacks on media broadcasters and press organisations so far in 2013 have had nothing to do with external attacks on websites or online presence, and the Syrian Electronic Army in particular have never used this attack vector – every one of their successful breaches has been the result of a phishing attack, which Mr Kolochenko’s tools will do nothing whatsoever to obviate.
This, of course, is both wrong and irrelevant – how the SEA’s preference for phishing (which could have been made easier by exploiting this vulnerability anyway) somehow protects xyz inc is beyond me.
The simple fact is this head of security was more concerned with deflecting any blame from himself, denying any vulnerability in his system and accusing me of lacking professional standards than in actually finding and fixing said vulnerability. A little humility and acceptance of help from security researchers might go a long way to making the internet a safer place.
Postscript. Following publication of the article, the websites in question fixed the flaws. As far xyz inc is concerned, Ilia subsequently received a further email:
We have now pushed out a fix for this vulnerability. Thanks very much for bring this to our attention.
Regards
xyz inc
Find the Collaborator – a proposal for a new game
To find the criminal, you must follow the money. To find the collaborator, you should follow the favours.
Now, if this principle holds true, we’ve got a good game to play – finding which security firms collaborate with government agencies by looking at which companies ingratiate themselves most, and which companies receive the most government favours.
Premise
Remember, this is a game. The rules are similar to those used by law enforcement agencies in their own game called Find the Terrorist: one red flag if the suspect denounces the invasion of a foreign land; two red flags if he or she accuses the government of lying or expresses sympathy with Anonymous; three red flags if a Moslem country is visited and so on. Six red flags and you’ve found a terrorist.
Rules
In our game, the following are worth one red flag:
- production of absurd statistics that support government policy (such as the cybercrime cost figures generated by McAfee and BAE Systems Detica)
- continuing success against all natural market forces (such as Microsoft Office, when there are better free products such as Open Office and Google Docs)
- purchase of key personal data companies that are outside of core business (such as EMC buying RSA, and Microsoft buying Skype)
- existing accusations of collaboration (such as BT over Tempora, and backdoors in Windows)
- directly accusing foreign governments of involvement in specific cybercrimes when in reality their can be no objective proof (such as Mandiant’s famous accusations against Comment Crew, and various firms’ terminology that implies that ‘hackers in China’ really means ‘Chinese government hackers’).
The following are worth two red flags:
- preferential treatment that does not make economic sense (such as government insistence that costly products – eg MS Office – are used in government departments, schools and examinations – in preference to free products like Open Office)
- sudden increase in direct government-inspired attacks against the major competition (such as those against Google – so who is Google’s primary competition? Note, this doesn’t mean that Google is innocent.)
The following are worth three red flags:
- direct government ‘approval’ (such as the elevation of Mandiant, Detica, Cassidian, and Context to CESG’s Cyber Response Scheme)
- active support for proposals that will make government surveillance more simple, such as support for the Communications Bill in the UK, or the Trusted Computing Platform anywhere.
Game weaknesses
There aren’t any…
Game strengths
…because you can’t lose. All security firms collaborate with government to one degree or another. If they don’t do it willingly, they do so under coercion; and if they don’t do it yet, it’s because they haven’t been told to, yet. But they do or will do it. The only way for a company to avoid collaborating with government is to shut down – like Lavabit.
See also:
Is it safe to carry on using Dropbox (post Prism)? Yes and No: Part III
Is the anti-virus industry in bed with the NSA – why do CIPAV, FinFisher and DaVinci still defeat AV?
Is Windows 8 an NSA trojan?
Am I a terrorist?
Bruce Schneier speaks out against surveillance
Even if you can’t get off the pot, at least you can decide which side of the fence you wish to pee. Bruce Schneier, precariously positioned as the CTO of one of the ISPs known to have helped GCHQ tap the world’s fibre cables, and simultaneously a director of the EFF, has decided on the direction of his stream of anger.
I have resisted saying this up to now, and I am saddened to say it, but the US has proved to be an unethical steward of the internet. The UK is no better.
(Actually, the UK would be far worse if GCHQ had half the money that the NSA commands.)
But what to do? Schneier offers three suggestions: expose, design and influence governance.
Expose means to subject bad things to the disinfectant of sunlight. We need whistleblowers, says Schneier.
I already have five stories from people like you, and I’ve just started collecting. I want 50. There’s safety in numbers, and this form of civil disobedience is the moral thing to do.
Design is to redesign the internet and its software and hardware components in a manner that is resistant to government subversion.
In particular, we need open protocols, open implementations, open systems – these will be harder for the NSA to subvert.
And governance requires influencing the future governance of the internet.
We need to figure out new means of internet governance, ones that makes it harder for powerful tech countries to monitor everything. For example, we need to demand transparency, oversight, and accountability from our governments and corporations.
But he accepts that it won’t be easy or overnight.
Has any country that engaged in mass surveillance of its own citizens voluntarily given up that capability? Has any mass surveillance country avoided becoming totalitarian?
What we need now is for all the internet and security luminaries of the world to come out and stand with Schneier, and to say to government in a voice that cannot be ignored: Enough. You don’t get security by spying on everyone. And you don’t have secret projects hidden from your own people. You are our servants. You are not our masters.
The US government has betrayed the internet. We need to take it back
Getting past the hype – how to find the right security product
Readers will know I believe there is a conspiracy involving the security industry, intelligence agencies/law enforcement and governments. The purpose is to over-hype the security threat so that the industry can sell more product, intelligence and law enforcement can get bigger budgets and government can pass an increasing amount of more controlling legislation.
Now this doesn’t mean that there is no security threat nor that every person working for the security industry is involved in the conspiracy. But therein lies the problem: how do you navigate your way through all the hype that comes from
- a security industry that needs to sell product
- a security industry that seeks to ingratiate itself with government via clearly bloated threat estimates in order to land lucrative government contracts
- a marketing industry skilled in turning an incident into a crisis
- intelligence agencies/law enforcement seeking to justify increasingly out of control budgets
- governments wishing to control the electorate via 1984-style legislation
in order to find what you actually need to stop the genuine threats that really do exist.
Wisegate can help. It’s an independent organization of senior IT managers from across the whole spectrum of industry – and it regularly publishes reports drawn from its own internal roundtables and discussion groups. One recent report covers just this topic: CISOs Share Top 10 Tips for Managing Vendors.
Quite simply, this report is packed with ideas for getting past the hype to find the right product from the right vendor; and it then explains how to maintain the best possible relationship with that vendor going forwards.
For a taster, my favourite tip actually suggests asking the wrong question to get the right answer. One of the CISO members of Wisegate (this one from a large industrial manufacturing company) uses ‘disruptive questioning’ – he doesn’t just ask, what are your strengths?’; he more specifically says, “When are you not good? What do you do worse than your competitor?”
How the vendor answers these questions will tell you a lot about that vendor, his attitudes, and whether you will be able to work with him in the future.
For the full ten tips, see the Wisegate report, CISOs Share Top 10 Tips for Managing Vendors.
But I particularly like this one – which could be a rule for life in general: “Demand what you pay for, and say thank you when you get it.”



